Apple will alert users exposed to state-sponsored spyware attacks
As part of Apple's initiative to battle state-sponsored spyware, or more specifically the surveillance and monitoring of Apple device owners, the company is introducing a system that will alert users when they are believed to be targets of such attacks.
On Tuesday, Apple announced that it filed suit against NSO Group and its parent company over the creation and deployment of the Pegasus spyware.
Ostensibly developed to aid in law enforcement campaigns, Pegasus relies on vulnerabilities, like the now-patched FORCEDENTRY exploit, to install a surveillance package capable of granting access to iOS and Android device microphones and cameras, as well as onboard data. The tool is sold -- allegedly indiscriminately -- to governments with poor human rights track records, who have in the past used it to monitor journalists, activists, researchers, politicians and other targets of interest.
Apple said it is notifying a "small number of users" who were targeted by FORCEDENTRY, and promised to continue to alert customers if and when future attacks are detected.
"Any time Apple discovers activity consistent with a state-sponsored spyware attack, Apple will notify the affected users in accordance with industry best practices," the company said.
The system is already active, as a Reuters report on Wednesday details alert messages that were sent to at least six Thai activists and researchers.
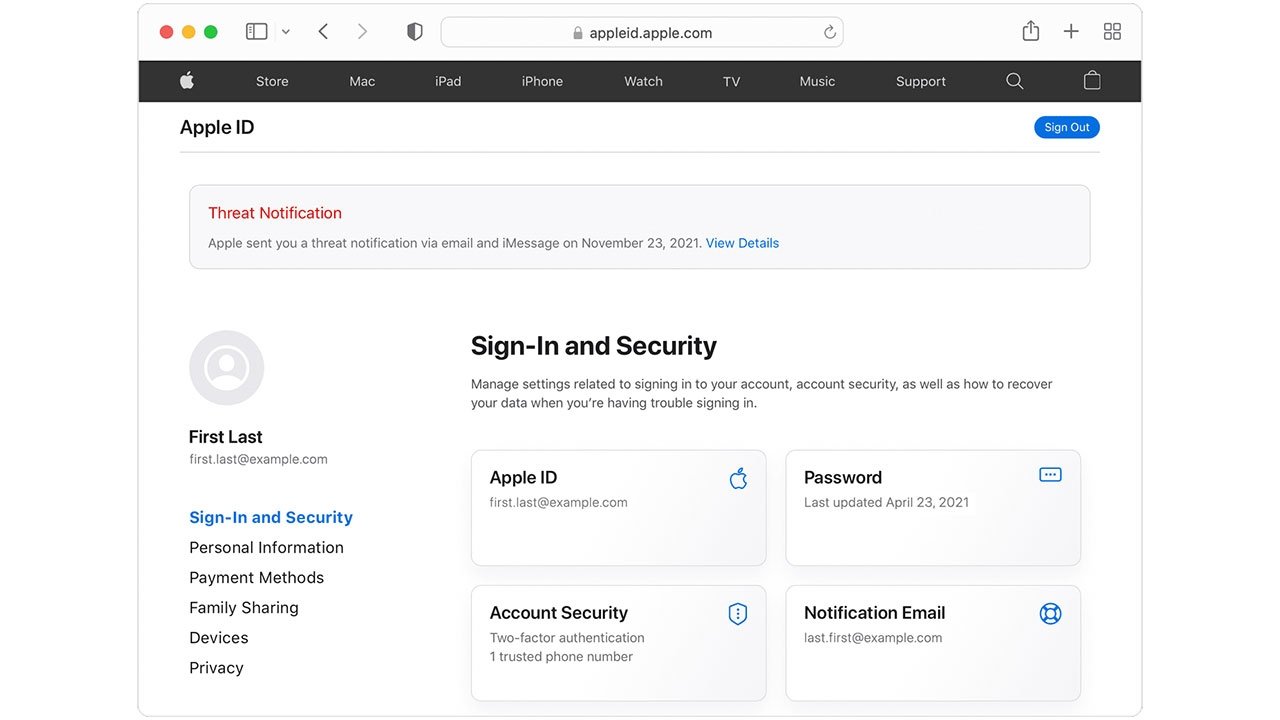
Apple explains threat notifications in a support document. While the inherent nature of state-sponsored attacks -- expensive, complex and highly targeted -- precludes most users from being exposed, Apple says that if one of its customers is affected they can expect to be informed in two ways: a prominent alert notification displayed at the top of the Apple ID website and alerts sent via email and iMessage to the address and phone number associated with an Apple ID.
Notifications from Apple will never ask users to click links, open files, install apps or profiles, or provide their Apple ID password or verification code by email or on the phone, the company says. Those who receive a threat notification can verify its authenticity by visiting the Apple ID portal, where an identical alert will appear should the message be genuine.
The tech giant acknowledges that false alarms are possible and that the system might not detect all attacks. As a precaution, users are urged to follow these best practices:
Read on AppleInsider

On Tuesday, Apple announced that it filed suit against NSO Group and its parent company over the creation and deployment of the Pegasus spyware.
Ostensibly developed to aid in law enforcement campaigns, Pegasus relies on vulnerabilities, like the now-patched FORCEDENTRY exploit, to install a surveillance package capable of granting access to iOS and Android device microphones and cameras, as well as onboard data. The tool is sold -- allegedly indiscriminately -- to governments with poor human rights track records, who have in the past used it to monitor journalists, activists, researchers, politicians and other targets of interest.
Apple said it is notifying a "small number of users" who were targeted by FORCEDENTRY, and promised to continue to alert customers if and when future attacks are detected.
"Any time Apple discovers activity consistent with a state-sponsored spyware attack, Apple will notify the affected users in accordance with industry best practices," the company said.
The system is already active, as a Reuters report on Wednesday details alert messages that were sent to at least six Thai activists and researchers.
Apple explains threat notifications in a support document. While the inherent nature of state-sponsored attacks -- expensive, complex and highly targeted -- precludes most users from being exposed, Apple says that if one of its customers is affected they can expect to be informed in two ways: a prominent alert notification displayed at the top of the Apple ID website and alerts sent via email and iMessage to the address and phone number associated with an Apple ID.
Notifications from Apple will never ask users to click links, open files, install apps or profiles, or provide their Apple ID password or verification code by email or on the phone, the company says. Those who receive a threat notification can verify its authenticity by visiting the Apple ID portal, where an identical alert will appear should the message be genuine.
The tech giant acknowledges that false alarms are possible and that the system might not detect all attacks. As a precaution, users are urged to follow these best practices:
- Update devices to the latest software, as that includes the latest security fixes
- Protect devices with a passcode
- Use two-factor authentication and a strong password for Apple ID
- Install apps from the App Store
- Use strong and unique passwords online
- Don't click on links or attachments from unknown senders
Read on AppleInsider

Comments
I took it that they were talking about Macs -- where side loading apps has been the predominant method.
"Your iPhone has been compromised by state-sponsered spyware. They are watching and listening to your every move. They know where you live, the names of your children and where they go to school. Click this link immediately so Apple can fix this for you."
https://appleinsider.com/articles/19/01/30/apple-has-revoked-facebooks-enterprise-developer-certificates-after-sideload-violations
This can be one source of apps downloadable from outside the App Store. Another I think is through Test Flight, which gives a developer an avenue to let a small set of users “beta” test an app before it goes onto the App Store.