AppleInsider · Kasper's Automated Slave
About
- Username
- AppleInsider
- Joined
- Visits
- 51
- Last Active
- Roles
- administrator
- Points
- 9,827
- Badges
- 1
- Posts
- 63,192
Reactions
-
Epic Games vs Apple set to restart in Australia with Google in tow
The paused courtroom fight between Apple and Epic Games in Australia is set to resume, but with a similar lawsuit against Google being incorporated into the same trial.
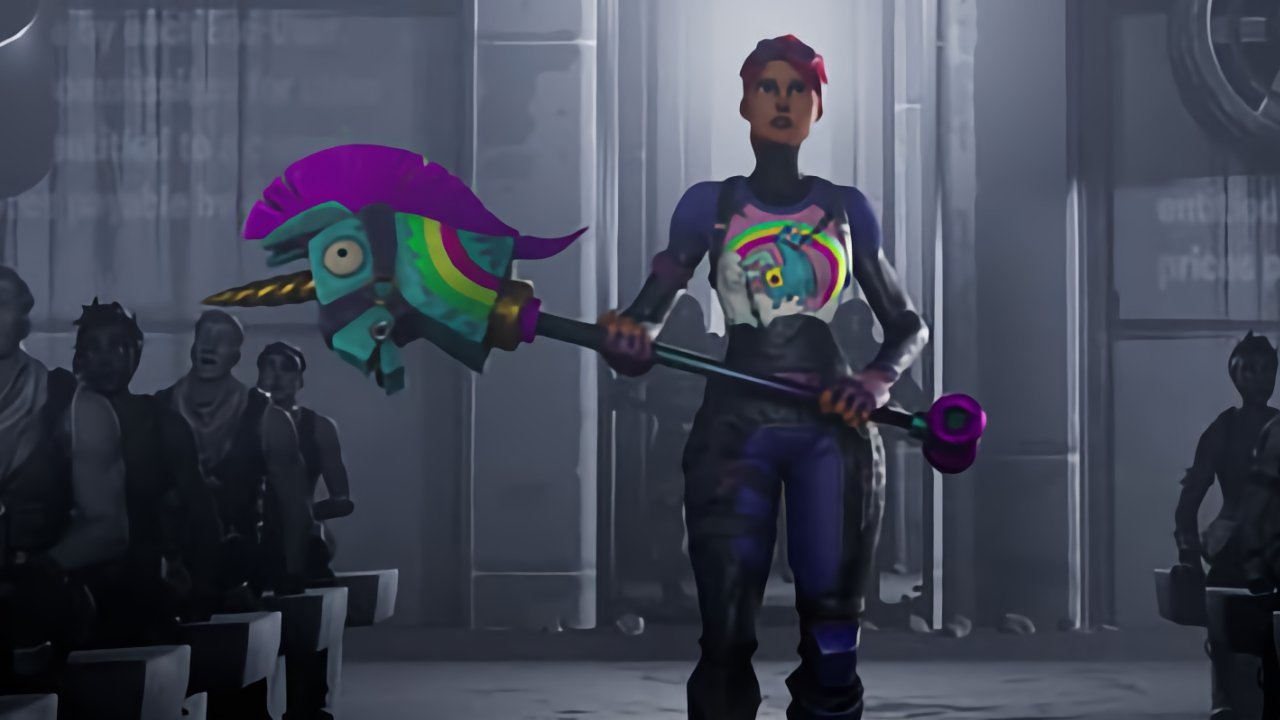
Still from Epic Games 'Free Fortnite' video
As part of its global legal battle against Apple over the popular game "Fortnite," Epic Games attempted to bring the battle to Australian courts in 2020. However, in April 2021, a judge ordered a stay on the case until the U.S. version of the dispute reached a conclusion.
With the American litigation all but concluded entirely, the courtroom action in Australia is preparing to start again. This time, Apple won't be the only one having to fend off Epic Games, as Google will also be in the same courtroom.
Just like in the United States, Epic had parallel cases against Apple and Google in Australia, with similar accusations of monopolistic behavior and disputes over in-app purchases.
Justice Jonathan Beach decided that it would be best to hear the two cases at the same time, as well as a class-action suit run on behalf of developers and consumers, reports The Guardian. The judge made the decision to avoid the duplication of witness evidence, which will include many high-profile people from all three companies.Five months, and beyond
The courtroom activity is expected to last for up to five months. The opening submissions will take two weeks which will then be followed by three months of evidence from experts and witnesses.
Much like the U.S. trial, the witnesses are expected to include major names at Apple and Google, with a number apparently already in Melbourne preparing for the hearing. Epic CEO Tim Sweeney is also allegedly in attendance.
After the three-month evidence period, closing submissions will last another two weeks, with the courtroom action ending in mid-July. However, the judgment from Justice Beach isn't expected to arrive within six months of the conclusion.
With the prospect of a lengthy appeals process, the lawsuits may not fully finish until 2025 or beyond.
Read on AppleInsider
-
How to use Apple's services on enterprise networks
Apple services use a variety of ports and connections that may not be immediately accessible when used on a corporate network. Here's how to access them on enterprise networks.

16-inch MacBook Pro
Security is a big issue when using devices to connect to Apple Services - especially for enterprise networks.
In enterprise, security is a top concern due to the fact that companies and organizations are constantly under external pressure from hackers, ransomware, denial of service (DoS), botnets, and other attacks.
Apple devices communicate with a variety of services on remote servers. Apple Push Notifications (APNs) are one such communication channel.
For example, if you see a Messages or FaceTime alert, you're seeing an Apple Push Notification.
Unlike some other network services, APNs require a service on a server that then communicates with Apple's APN servers.
Apple and third-party apps know how to send and receive APNs through these channels to communicate in real time.UNIX, ports, and protocols
In UNIX and Linux operating systems, networking layers and apps communicate on ports and sockets.
Think of a socket as a networking pipe where data flows between computers. Different networking protocols can be used on sockets in UNIX, but TCP/IP or UDP is used for most internet messaging communications.
TCP/IP uses a send-acknowledgment network packet model, whereas the UDP protocol sends data without receiving acknowledgments. The acknowledgment, or "ack" in TCP/IP is what allows reliable communication - if the networking layer doesn't receive an ack when it sends a packet, it waits a certain interval and then resends it.
In TCP, resends continue until an ack is received, or until application-layer software tells the socket to stop. This could be after a timeout, for example.
TCP's design was part of the original US Dept. of Defense ARPANET project, a project tasked with creating a reliable military communications network capable of withstanding a nuclear war. As such, the TCP/IP protocol knows how to automatically reroute data should communications fail.
This design ensured military hardware could continue to communicate even without human operators.
UDP, on the other hand, doesn't wait for acknowledgments - it broadcasts data in streams on certain ports but it doesn't care if certain destinations receive the packets or not. Hence UDP is known as the "streaming protocol" since it essentially broadcasts a continuous stream of data on a certain port.
UDP listeners can simply listen in on the indicated port to receive the stream of data packets. Most internet video and music streaming services use UDP for broadcast.
Other types of protocols are used for other kinds of communication. For example, web traffic uses HTTP or HTTPS.
Web security is provided by TLS/SSL and other security laters. The "s" in HTTPS stands for the "S" in SSL (Secure Sockets Layer). SSL was renamed to TLS, or Transport Layer Security years ago.
Hence the HTTPS protocol is really HTTP using transport or socket security (encryption).
Each service or protocol uses a numbered port. Ports tell an operating system where to listen for incoming data.
For example, standard HTTP uses port 80. The now little-used FTP protocol uses ports 21 and 20.
TCP and UDP are lower-level packet protocols whereas HTTP/HTTPS, FTP, and others are higher-level protocols.
Each "service" or type of data has a predefined port number so that network traffic doesn't get mixed up on arrival.
It is possible to change default ports to custom port numbers. Using custom port numbers is a security measure because hackers often look for specific types of traffic on known ports.
If you change the port number for standard types of traffic, hackers won't see that data on the standard port and therefore will have a more difficult time intercepting it.
When you run an app that uses network communication it typically creates a networking socket in code, on a certain port, and then begins transmitting and receiving network packets on that port. At the UNIX networking layer, incoming and outgoing traffic is routed to each networking socket at the app layer as data arrives or is sent.
Most UNIX networking "stacks" are written in the C programming language for speed - and because the first complete released UNIX sockets implementation - Berkeley Sockets Distribution or BSD was written in C. Most of Apple's current operating systems are based on modified versions of BSD called XNU developed at Apple.
Technically, the data packets are further broken down into frames at the data link layer, then finally into bytes at the physical or "phy" layer before they are sent by the networking device. But for the most part, you don't need to concern yourself with the data link or phy layers.
Frames are used because each physical networking technology (Ethernet, fiber, etc.) may use different frame types.
At the other end of the connection bytes and frames are reassembled into packets and are passed up to the networking layer, then finally to the application layer where their data is read and used.Proxy servers
For many reasons, most organizations use proxy servers as part of their network topology. A proxy server is a server that either acts as a data forwarding server, or as part of a firewall for security reasons.
Proxy servers can be used to receive requests, then forward those requests to other servers - usually content servers. Proxy servers are also sometimes used in load balancing systems.
Proxy servers are usually (but not always) physically distributed away from content servers.
Load balancers act as buffers so that content servers don't get overloaded or stop working due to high traffic loads. A typical organization network topology will include several proxy, content, and load-balancing servers.
Some companies (such as Barracuda, Citrix, Cisco, and others) specialize in selling load-balancing appliances that can be configured in racks or banks and then receive and reroute external traffic to content server destinations. Large companies often have entire rooms full of load balancers to distribute network loads across servers.
Content servers can further be distributed across one or more CDNs or Content Delivery Networks. CDNs are effectively distributed load balancers, ensuring that traffic is routed as efficiently as possible both geographically, and performance-wise.
Barracuda Load Balancer 340Apple Services
Apple provides a number of networking services and to do so it operates many custom servers and CDNs to handle the network traffic. To do so it often uses standard or custom ports for its servers.
With billions of Apple devices now in use daily, the network load on Apple's servers and services is tremendous, and to ensure everything continues to work smoothly, it must carefully design how its networking traffic is handled.
Apple also uses many domains for device management. Enterprise deployment of Apple devices can be too large to handle manually, and as such Apple provides MDM or Mobile Device Management - a term that now encompasses all Apple devices.
Apple doesn't provide MDM servers or services directly - it only defines how they are to be configured and deployed - implementation is left to third parties to handle.
Some Apple service domains support proxies and captive portals, but some don't.
A captive portal is a server or web page that provides authentication (sign-in) for various organization services. If you've ever gone to a Starbucks and had to sign in to its free WiFi you are using a captive portal.
For internal enterprise use, Apple's MDM defines the concept of enrollment - which is essentially registering an Apple device on a specific organization's network. Enrollment is used to determine which devices are known and recognized on organization networks and which aren't.
Enrollment helps security and network administrators detect hostile devices on internal and Virtual Private Networks (VPNs).
Other services provided by Apple act in conjunction with MDM and enrollment to provide miscellaneous functions such as time/locale settings, updates, and device termination.
For example the domains time.apple.com and time-ios.apple.com are used to set the date/time and even language for enrolled devices across all time zones/locations on the globe using Network Time Protocol (NTP).MDM services
If you're enrolling or deploying devices on corporate networks using an MDM solution, you'll need access to at least APNs, enrollment, external services, and software updates.
For APNs you'll need access to *.push.apple.com on ports 80, 443, 2197, and 5223 - and your third-party APN server solutions or proxies must be able to communicate over TCP on these ports without restriction.
If access to these ports is unavailable, then your enrolled users may not receive real-time notifications such as Messages, FaceTime, web, or software updates. Keep in mind many organizations like to use automatic software updates as doing so vastly reduces the need to manually update software.
Without access to APN ports automatic software updates may not work.
If you are using Apple School Manager or Apple Business Manager which utilize Apple device profiles, then you'll also need access to iprofiles.apple.com.
To ensure all your MDM services work correctly, speak with your MDM administrator(s) or MDM service providers to make sure all servers and software are configured correctly.Global HTTP Proxy MDM payload
Some organizations only allow web traffic to enter or exit the organization through predefined proxy servers. This topology ensures all web traffic can be traced, monitored, or blocked via proxy server configuration.
For example, proxy servers can be configured to block all traffic on certain ports, or only allow traffic on specific ports, while denying all traffic on other ports. This reduces the attack surface and minimizes ways for hackers to break into a network.
Proxy servers can also be used to forward or restrict which traffic gets sent to other servers - sometimes for security reasons, observability, or content delivery.
In the case of APNs, third-party servers essentially act as proxy servers for Apple's Push Notification service.
In the APN model, apps first send to or listen on their own APN servers, which then forward and receive notifications from Apple's APN service.
For organizational HTTP traffic, if you're using an MDM solution, you'll need to be aware of Global HTTP Proxy MDM payload settings for MDM-controlled devices.
A Global HTTP Proxy MDM payload tells an Apple device how and where to send and receive HTTP data on a proxy server.
For devices with manual authentication (i.e. - user name and password), you'll need to ensure proxy servers can receive Global HTTP Proxy MDM payloads. For devices with automatic login, you'll need to be able to provide a PAC file for each server or port you need access to.
Each HTTP Proxy MDM payload contains info on name and ID, which operating systems are supported, enrollment types, and if duplicates are allowed.
There are hundreds of Apple domains supported in HTTP Proxy MDM payloads, and your devices must ensure they can provide the correct payload for the services needed.
For complete info on HTTP MDM payloads see the section "Review MDM payloads for Apple devices" in the Apple Platform Deployment guide on Apple's site.
Apple's iCloud.CloudKit, App Store, and TestFlight
If you are a developer or software deployment administrator at an organization, you'll also need to be aware of any software that uses Apple's iCloud, CloudKit, or TestFlight apps.
CloudKit is Apple's API for communicating with iCloud's database services. If an app uses CloudKit to access remote databases hosted on Apple's servers you'll need to make sure those networking services and ports are configured correctly.
Most (but not all) of Apple's CloudKit APIs communicate on port 443 - the standard https port.
Without port 443 access, software can't send and receive HTTPS web data unless a custom port has been defined.
There are, in fact, over a dozen Apple-hosted CloudKit domains you'll need to be aware of.
Apple's app validation, receipts, and Notarization services and security also use port 443 so to ensure most App Store apps work, all your enterprise servers will need port 443 also.
App Store downloads use the ASN.1 (Abstract Syntax Notation One) security, and software from the App Store that doesn't validate using ASN.1 won't work on Apple devices. ASN.1 is a vast topic in and of itself, so we won't get into its details here.
Suffice it to say when you download or deploy software from the App Store to an Apple device, an encryption handshake of sorts happens which uses ASN.1 to exchange and validate a receipt tied to each app.
Without this receipt validation App Store apps can't run on iOS devices.
For Mac devices, Notarization works in a similar manner - with apps being Notarized by Apple also requiring a validation in order to run.
All of these security checks are performed over the internet so your enterprise networking must be configured to allow them to work.
Touch ID and Face ID also use TCP on port 443 at *.appattest.apple.com for validation.
Apple's developer TestFlight beta distribution service for pre-release apps also uses port 443.Other services and Firewalls
There are dozens of other Apple Services we didn't mention here. These include but aren't limited to:- Apple Diagnostics
- Apple ID
- Apple Pay
- Encrypted DNS
- Certificate validation
- Siri and search
- Associated Domains
Some corporate networks support firewalls that can allow or deny network traffic based only on the domain name. This configuration is easier for admins to manage, but it provides a less granular-level control over which servers a client can communicate with.
If your organization's firewalls allow domain-level access and filtering, you can allow access to all Apple remote services. This is done by allowing all Apple subdomains to pass through the firewall using the *.apple.com wildcard domain.
This is because all Apple remote services use servers on domains that end in "apple.com".
If your firewalls don't allow domain-level filtering and only support IP-level configuration, you can allow all outbound connections to Apple servers at 17.0.0.0/8 because the entire 17.0.0.0/8 block is assigned to Apple.
For a complete list of Apple domains, services, ports, protocols, and supported devices, see the support page Use Apple products on enterprise networks.
This page lists most public-facing services, domains, which ports and protocols they use, and which devices and operating systems are supported on each.
Not all Apple devices are supported on all services.Additional documentation
There are several other deployment and networking documents from Apple you'll want to take a look at. These include:- If your Apple devices aren't getting Apple push notifications
- Choose an MDM solution
- Apple Platform Deployment
If you're a developer, you'll also need to read the sections Registering your app with APNs and Sending notification requests to APNs in the User Notifications section of Apple's developer documentation.
That document also has info on how to set up APN servers.
For secure Mac app deployment, read Notarizing macOS software before distribution in the Apple developer security documentation.
Enterprise networking as well as device management are complex topics. We've only covered a part of what you need to know to use Apple devices on enterprise networks.
We also didn't touch here on profiles - files Apple devices use to verify and install software and provide network security.
In future articles we'll discuss deployment and MDM in depth, as well as firewalls, protocols, and networking information in more detail.
Read on AppleInsider
-
Rock Paper Pencil review: the iPad upgrade every artist needs
Astropad's Rock Paper Pencil is a textured screen protector and a replacement Apple Pencil tip that should be part of every artist's toolbox.

Astropad's Rock Paper Pencil
The iPad is a fantastic tool for creative people, especially since the Apple Pencil was released. While we believe Apple did a great job, there is still room for improvement when it comes to drawing and writing on the iPad.
For artists looking to upgrade their drawing and writing experience on iPad, the Astropad Rock Paper Pencil kit is a game-changer. This screen cover has been designed with precision and realism in mind, providing a paper-like texture, easy application, and a fine ballpoint tip for unparalleled control.Rock Paper Pencil review - design
Astropad's Rock Paper Pencil screen protector features a matte finish that mimics the texture of paper while minimizing glare. The first version attached to your iPad screen magnetically and could be removed easily.
This new version attaches more like a traditional screen protector with static cling, and the application was effortless.
Though we preferred the first version a little better, each has pros and cons. The new version feels like you probably shouldn't take it off your iPad for fear of dust sticking to it upon reapplication.
Still, to be fair, we didn't take the first version off our iPad, and the edges got dinged up a fair amount. This second version feels like it'll last a lot longer. Again, it's not a major deal either way.
Unlike some alternatives that simply change the screen's texture or the Pencil tip, the Rock Paper Pencil combines a custom Apple Pencil tip with a precisely engineered screen protector. We adore this approach.
The combination creates a remarkably realistic pen-on-paper feel when using your iPad, making drawing and taking notes less strenuous on your hand.Rock Paper Pencil review - in use
One common frustration with drawing on the iPad's glass screen is the slippery surface, which can hinder the consistency of strokes. It also can lead to debilitating hand cramps while working or writing for a long period of time.
Rock Paper Pencil review: we accidentally ordered the incorrect protector for our iPad Air -- if you order yours, it will have the correct cutout
By adding that subtle friction back, you'll find that you have way more control over how you lay down a line. Writing notes also feels better, significantly improving our handwriting legibility versus writing on the bare iPad screen.
The super-fine ballpoint tip ensures precise control, resulting in controlled and accurate lines -- and it really does feel like writing or drawing with a ballpoint pen. In addition, the pencil tip and screen protector are wear-resistant, promising long-lasting durability.
Rock Paper Pencil review: the stylus tip feels nearly identical to a ballpoint pen on paper
We were able to work in Procreate for several hours at a time without hand cramps, which isn't the case if we use the Apple Pencil directly on the iPad screen. You need to experience it to understand it, and if you're an artist who primarily works on iPad, we can't recommend it enough.
Another benefit is that the nano-texture technology used in this screen protector reduces glare and reflections while working. This is great if you're working in a particularly bright space, like an office with many windows.
One small thing to note is that you will smudge the screen protector. Pretty much no matter what you do, this screen protector will collect a fair amount of fingerprints as you use it.
Rock Paper Pencil review: the screen protector does collect fingerprints, though they're not terribly visible head-on
One of the advantages of the nano-texture technology used in this product is that when you look straight on, you won't be able to notice any streaks. However, the downside is that it can be a bit more difficult to clean. Astropad recommends using a lint-free wipe and 70% isopropyl alcohol to clean it. Although this method works, it may take a few attempts to clean it thoroughly.
Overall, we're big fans of the Rock Paper Pencil. Not only does it make it significantly more comfortable to write and draw on your iPad, but its glare reduction is fantastic. This might be the best artist-geared iPad screen protector we've tried.Rock Paper Pencil pros
- Added friction makes writing, drawing comfortable
- Custom pen tip improves accuracy
- Very easy to install
- Damage-free removal
- Easy to apply
Rock Paper Pencil cons
- Some users may prefer the original magnetic attachment style
Rating: 5 out of 5
Where to get Rock Paper Pencil
You can snag your own Rock Paper Pencil from Astropad for $39.99 or from Amazon for $39.99. It is available for the 11-inch iPad Pro and iPad Air, 12.9-inch iPad Pro, iPad Mini, 10.2-inch iPad, and 10.9-inch iPad.
Read on AppleInsider

-
How to take a full-page screenshot on iPhone
It's surprisingly simple to capture a long web page in a single screenshot on your iPhone or iPad, and edit it to hold just the information you want.
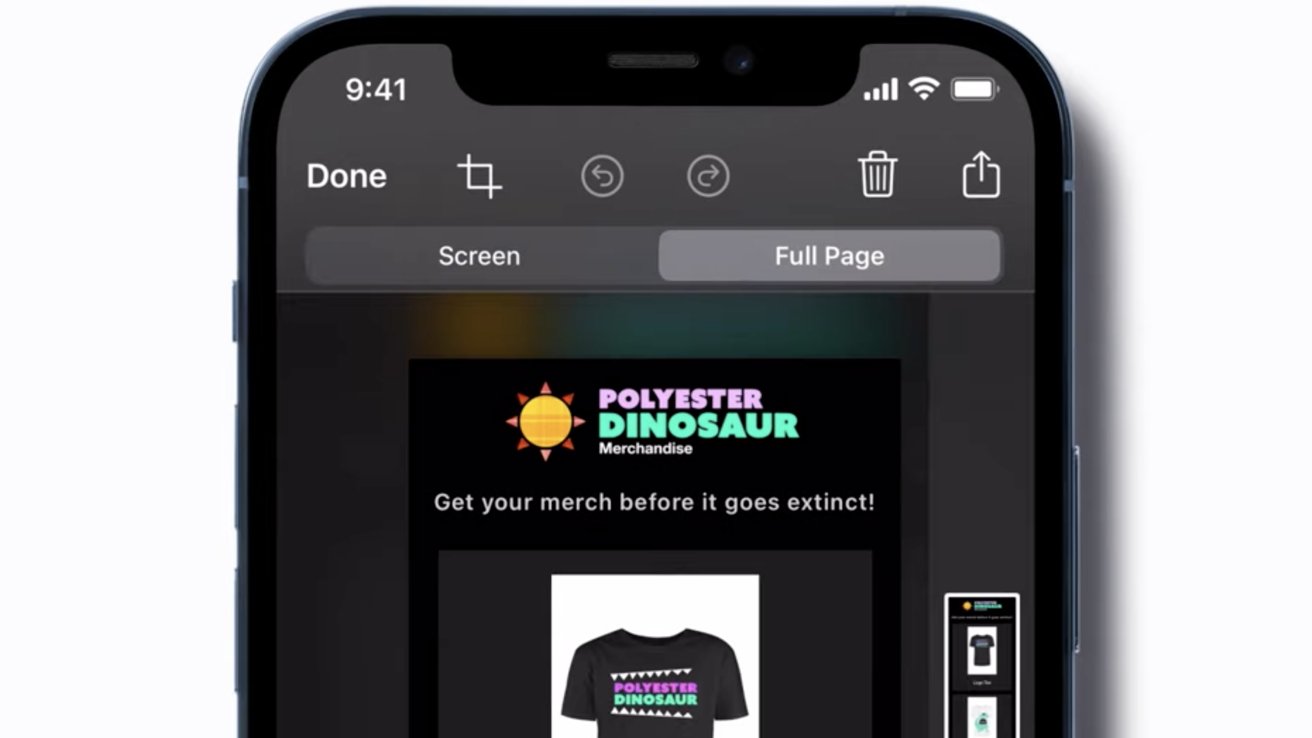
When you create a screenshot on your iPhone -- or iPad, for that matter -- the image that is created initially appears to be just the portion of the web page that appears on your screen -- a literal "screen" image. However, website articles and home pages tend to be much "longer," running off-screen until you scroll down.
In fact, though, your "screenshot" taken on an iPhone also captures the entire page of the website, no matter how long it is. You have to then say that you want the full screen image, but when you do, you can also easily edit the screenshot after it is taken to trim it to any section you really want.Taking a full-page screenshot on iPhone
To take a screenshot using your iPhone, press the upper volume button and the power button briefly at the same time. The screen will "flash" to indicate you were successful, and a small thumbnail of the visible screen content will appear in the lower-left corner, and move offscreen after a few seconds if you don't tap on it -- or if you flick it away to the left.
If you instead tap on the thumbnail, it will expand into edit mode, starting at the top of the captured page. You'll see a few standard editing tools above the image, and two choices just below the tools: "screen" and "full page."
If your intent was just to capture something on the visible screen area when you took the picture, you can tap on the "crop" tool to trim off anything you don't want, tap the "done" button, and choose where to save it. You can save it to the Photos app, the Files app, or create a Quick Note with the image in it.
You also get the option to "copy and delete," meaning to save the screenshot image to the clipboard but delete the actual screenshot, or delete the screenshot outright. The options for the "full page" image are slightly different: you can save to photos, save as a PDF to files, or copy-and-delete and just delete.
If you wanted to capture the whole page, though, just tap on the "full page" option, and you'll see a long, skinny, and very small thumbnail of the entire image to the right, while your screenshot remains on the left. Likewise, these tools are all available if you're working on your iPad.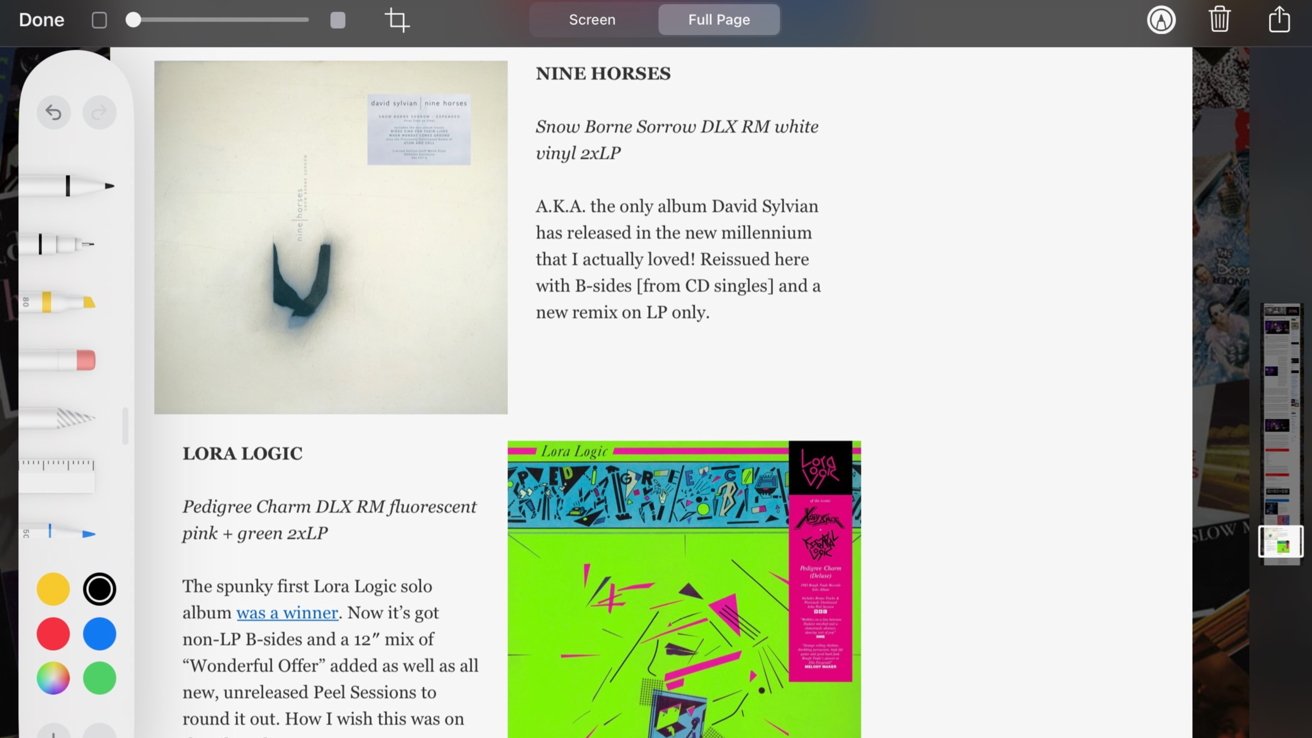
Editing a captured full-page screenshot on an iPadEditing your full-page screenshot
You can scroll down through the screenshot by moving the highlighted area of the thumbnail to get an idea of what, if anything, you'll want to trim. The tools at the top of the screen will let you undo or re-do your editing actions, trash the image, or send it somewhere.
When you want to save the full-page screenshot, just tap the "Done" button on the left side of the toolbar. You'll get the option to save it to Photos or save a PDF version to the Files app, where you'll be asked where in your iCloud files you want to keep it.
As with the "screenshot" option, you can use the "send" icon to email, message, AirDrop, and send to your full page screenshot to specific people, your preferred social media sites, or add to the Notes. By default, screenshots and full-page screenshots are saved as .png (portable network graphics) files, which is a lossless raster RGB format.
As with a lot of Apple features and apps, there are obscured but advanced features you can take advantage of behind the "simple" operations that most users find is all they need. For those occasions when you want to go beyond the basics, the tools to create something more impressive are there -- they just take a little more effort to find and utilize.
Read on AppleInsider
-
Apple spotlights Entrepreneur Camp alumni app developers
Marking five years of its Entrepreneur Camp development program, Apple has highlighted three creators who are working to solve real-world problems through the App Store.

L-R: Jenny Xu of Run Legends, Edna Martinson of Boddle Learning, and Jo Aggarwal of Wysa
The 2023 Entrepreneur Camp was split into two parts with one week for under represented business founders, and one for female founders. In both cases, the aim of the online event is to promote diversity and inclusivity in the technology industry.
In a new profile of successful Camp alumni, Apple says that its "ethos [is] that apps for everyone should be made by everyone." The three women profiled range across AI, fitness and education.Creating apps to make a better world
Entrepreneur Camp 2019 alumni Jo Aggarwal, is the CEO and founder of Wysa. It's an emotionally intelligent chatbot, written with therapists, that has helped millions of people across 95 countries.
"We set out to solve for global mental health and give people a safe space to work through their thoughts and emotions, building resilience irrespective of stigma, race, gender, access to a therapist, or diagnosis," said Aggerwal. "Language can also be a barrier, and in an effort to make Wysa's support more inclusive, we are launching Wysa in Spanish to create more equitable access to marginalized communities."
Then 2022 graduate Jenny Xu, created the game Run Legends, which fuses together her passions for gaming and running.
"When I started out in the gaming industry," said Xu, "I felt like I was the only one doing what I was doing... I grew up playing a lot of story-based interactive fiction -- artistic games that make you come away having learned something about life, and I think that's a genre that's predominantly popular with women."
"With Run Legends, even though it's a battle game, it isn't a game that makes people feel really aggressive when they're playing it -- they can feel empowered," she continued. " Now that I've raised some money and shipped some games, I try to give back and show that it's possible to build games that aren't just shooters, but games that actually make the world a better place."
Lastly, Edna Martinson from the 2023 Entrepreneur Camp's intake, developed an education app called Boddle to help "tackle learning gaps and boost [children's] confidence in the classroom."
"My perspective as a woman in this field has really shaped our team and how we connect with our community, especially since most elementary school teachers that we serve are women," says Martinson. :We've had a blast doing virtual career days on Zoom, showing kids how we made Boddle, and introducing them to game design."
"It's super rewarding to see the excitement on little girls' faces when they find out a woman cofounded Boddle," she continues. "It shows them they can be leaders in tech too."
Read on AppleInsider
