Researcher estimates GrayKey can unlock 6-digit iPhone passcode in 11 hours, here's how to...
New estimates from a security researcher suggest GrayKey, a digital forensics tool in active use by U.S. law enforcement agencies, is capable of cracking Apple's standard six-digit iPhone passcode in an average of 11 hours. Longer codes, however, could take years to process. Here's how to beef up your handset's security.
Taking a closer look at GrayKey, Matthew Green, an assistant professor and cryptographer at the Johns Hopkins Information Security Institute, says the iPhone unlocking device has the potential to crack a simple four-digit code in six and a half minutes, or 13 minutes at the longest.
According to his calculations, Green estimates a six-digit passcode takes up to 22.2 hours to break, while processing an 8-digit code can take as few as 46 hours or up to 92 days. That figure jumps to 25 years, or 12 years on average, for strong 10-digit passcodes made up of random numbers.
Green published the estimates in a tweet picked up by Motherboard on Monday.
Notably, Green's estimates are much faster than those reached in previous reports, which guessed a six-digit passcode would take "days" to crack.
The latest assessment assumes GrayKey uses an exploit that bypasses Apple's built-in security protections. Specifically, iOS delays multiple incorrect passcode attempts in a bid to thwart brute force attacks. These pauses are enabled after four consecutive attempts and run from one minute for a fifth unsuccessful attempt to one hour for the ninth consecutive error.
Further, users can elect to wipe their iPhone's data after ten consecutive failed attempts. GrayKey seemingly bypasses this failsafe, as well.
As suggested in previous reports, GrayKey developer Grayshift is thought to rely on an undisclosed iPhone jailbreak or zero-day exploit to achieve the relatively quick turnover. The firm markets GrayKey in a $15,000 internet-connected "flavor" with limited unlocks and a $30,000 unrestricted version.
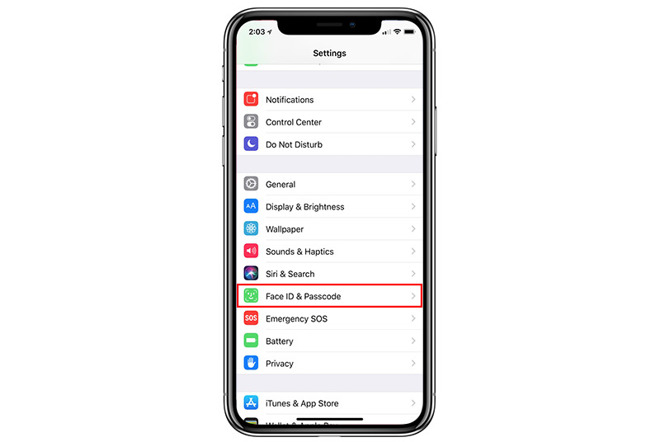
If you are currently operating an iPhone or iPad without a passcode, navigate to Face ID & Passcode or Touch ID & Passcode in the Settings app and select Turn Passcode On. You will be presented with an option to enter a six-digit passcode, but that option is made less secure with tools like GrayKey.
Instead, select the Passcode Options link to enter a custom numeric code or custom alphanumeric code. As noted by Green, an 8-digit code now offers a moderate level of security, while 10-digit codes provide even stronger protection. Alphanumeric passwords with random letter, number and symbol combinations typically provide the highest level of security.
Enter your new passcode or password into the box and reconfirm on the next screen to activate.
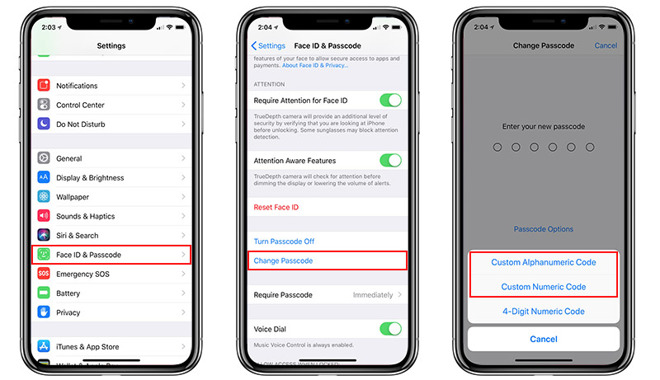
Enter your passcode once more to reveal a passcode settings screen, then select Passcode Options. Choose either Custom Alphanumeric Code or Custom Numeric Code and plug in your desired passcode. Re-enter the code on the next screen to activate.
Taking a closer look at GrayKey, Matthew Green, an assistant professor and cryptographer at the Johns Hopkins Information Security Institute, says the iPhone unlocking device has the potential to crack a simple four-digit code in six and a half minutes, or 13 minutes at the longest.
According to his calculations, Green estimates a six-digit passcode takes up to 22.2 hours to break, while processing an 8-digit code can take as few as 46 hours or up to 92 days. That figure jumps to 25 years, or 12 years on average, for strong 10-digit passcodes made up of random numbers.
Green published the estimates in a tweet picked up by Motherboard on Monday.
Notably, Green's estimates are much faster than those reached in previous reports, which guessed a six-digit passcode would take "days" to crack.
The latest assessment assumes GrayKey uses an exploit that bypasses Apple's built-in security protections. Specifically, iOS delays multiple incorrect passcode attempts in a bid to thwart brute force attacks. These pauses are enabled after four consecutive attempts and run from one minute for a fifth unsuccessful attempt to one hour for the ninth consecutive error.
Further, users can elect to wipe their iPhone's data after ten consecutive failed attempts. GrayKey seemingly bypasses this failsafe, as well.
As suggested in previous reports, GrayKey developer Grayshift is thought to rely on an undisclosed iPhone jailbreak or zero-day exploit to achieve the relatively quick turnover. The firm markets GrayKey in a $15,000 internet-connected "flavor" with limited unlocks and a $30,000 unrestricted version.
Enable passcode
Six-digit passcodes became the norm for iOS in 2015 with the release iOS 9. Previously, Apple required a simple four-digit passcode to protect iPhone and iPad from would-be intruders, but policies changed with the advent of advanced biometrics like Touch ID and, more recently, Face ID. The specter of warranted -- and unwarranted -- government access to consumer devices is also thought to have played a role in Apple's move to longer, more secure codes.
If you are currently operating an iPhone or iPad without a passcode, navigate to Face ID & Passcode or Touch ID & Passcode in the Settings app and select Turn Passcode On. You will be presented with an option to enter a six-digit passcode, but that option is made less secure with tools like GrayKey.
Instead, select the Passcode Options link to enter a custom numeric code or custom alphanumeric code. As noted by Green, an 8-digit code now offers a moderate level of security, while 10-digit codes provide even stronger protection. Alphanumeric passwords with random letter, number and symbol combinations typically provide the highest level of security.
Enter your new passcode or password into the box and reconfirm on the next screen to activate.
Switching to a longer passcode
If you are already using Apple's standard 6-digit code and want to update to a longer numeric or alphanumeric value, navigate to Face ID & Passcode or Touch ID & Passcode in the Settings app, enter your passcode and select Change Passcode.
Enter your passcode once more to reveal a passcode settings screen, then select Passcode Options. Choose either Custom Alphanumeric Code or Custom Numeric Code and plug in your desired passcode. Re-enter the code on the next screen to activate.


Comments
It’d be nice if there was a single quick action which could be taken to disable FaceID for one login—like a wink, or a smile, or lack of a smile, etc., something user definable.
If you have legitimate highly sensitive information there and have a fear that you may be targeted by an investigative agency who also believes they have a legitimate need to look at it and you need to keep out of their hands then by all means set up the longest pass code you can remember. Otherwise I'm not convinced hand-wringing and worry over Graykey are warranted. The standard 6 digit pass-code should be quite sufficient. Just my opinion.
There seems to be many options Apple has here to expand scope and blow machine out of water while keeping easy for user.
Also, identity theft is a money-making enterprise. Who's to say this device won't be bought by some group of phone thieves who steal phones for their credit card and other identity info? Buying an expensive device to steal a hundred times more from many phones would still be a profit for them.
It would also be nice if Apple closed this bug which gets around the longer and longer wait periods between attempts.
I'd also like a feature where if anybody yelled in anger near my phone that it would not unlock without then requiring BOTH, else it would require just biometric.
How about if facial recognition could let me program in a winking pattern or funny face or something? Better, it could give me a clue of WHICH of the facial actions were required. I'd know if the image on the screen raised an eyebrow that I'm supposed to frown. or some such.
I’ve always had the erase feature enabled. And, my login passwords are now 24(+) characters. (Takes about 3 sec. to type)
Most administer passwords have been 12 characters for a while now (for businesses). The biggest problem is unknown or unpatched vulnerabilities.
The 4 digit passwords were laughable... they might keep unmotivated children out.
TouchID is surprisingly responsive to non-standard skin patterns.
I still want an option where the device tells you that the password is wrong after the first time you type it correctly, forcing you to do it twice (or more) for actual entry.