Israeli spyware claims to beat Apple's iCloud security
NSO Group, which previously hacked WhatsApp, is advertising that it is able to gather all of an individual's cloud-hosted data from Apple, Google, Microsoft and more, using its Pegasus malware.

Apple's iCloud is one of many cloud services the NSO Group reportedly claims it can hack
The Israeli company, NSO Group, has been telling its government customers that its Pegasus malware can now extract far more data about any given individual. As well as data on the person's smartphone, the claim is that the group can covertly retrieve all of the information that person has stored on servers owned by Apple, Google, Microsoft, Facebook and Amazon.
According to the Financial Times, that information includes all messages and photos, plus data concerning the entire history of the phone's location.
The NSO Group, whose software was recently used to hack WhatsApp, says that it develops this malware specifically for government use only.
"We do not provide or market any type of hacking or mass-collection capabilities to any cloud applications, services or infrastructure," a spokesperson said.
The FT notes that the group did not deny the claims of these capabilities, and that separate research efforts have shown the presence of Pegasus malware on the phones of journalists and human rights activists. The newspaper's unnamed sources who described an NSO sales demonstration, also provided documentary evidence.
The documents include a sales one which says full access is provided to a person's data without "prompting a two-step verification or warning email on [the] target device."
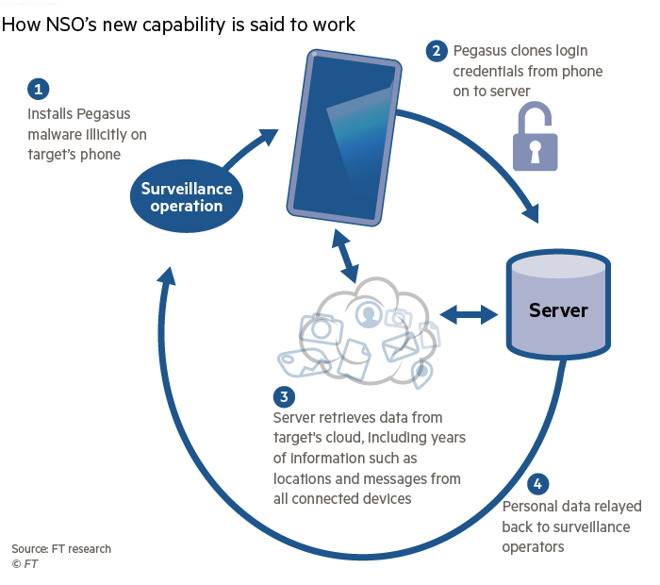
Graphic from the Financial Times illustrating how the NSO Group's Pegasus software now works (Source: Financial Times)
This Pegasus malware must be installed on the phone, with what appears to require root access. If an assailant has root access, a user has problems beyond iCloud monitoring. Methods of penetration have been demonstrated previously..
Once it is loaded, however, it's believed that the Pegasus malware copies the login credentials used to access cloud storage. That information is then sent to the government or other organization using the malware, and they then have full access to that cloud storage.
According to sales documents, the system works with even the latest iPhones and Android phones.
Apple responded to reporters from the FT, saying that its iOS is "the safest and most secure computing platform in the world." Apple has managed to block previous versions of Pegasus, both on iOS and macOS.
"While some expensive tools may exist to perform targeted attacks on a very small number of devices," continued Apple, "we do not believe these are useful for widespread attacks against consumers."
Similarly, Microsoft said it is "continually evolving" its protections. Amazon and Microsoft say they're investigating.

Apple's iCloud is one of many cloud services the NSO Group reportedly claims it can hack
The Israeli company, NSO Group, has been telling its government customers that its Pegasus malware can now extract far more data about any given individual. As well as data on the person's smartphone, the claim is that the group can covertly retrieve all of the information that person has stored on servers owned by Apple, Google, Microsoft, Facebook and Amazon.
According to the Financial Times, that information includes all messages and photos, plus data concerning the entire history of the phone's location.
The NSO Group, whose software was recently used to hack WhatsApp, says that it develops this malware specifically for government use only.
"We do not provide or market any type of hacking or mass-collection capabilities to any cloud applications, services or infrastructure," a spokesperson said.
The FT notes that the group did not deny the claims of these capabilities, and that separate research efforts have shown the presence of Pegasus malware on the phones of journalists and human rights activists. The newspaper's unnamed sources who described an NSO sales demonstration, also provided documentary evidence.
The documents include a sales one which says full access is provided to a person's data without "prompting a two-step verification or warning email on [the] target device."

Graphic from the Financial Times illustrating how the NSO Group's Pegasus software now works (Source: Financial Times)
This Pegasus malware must be installed on the phone, with what appears to require root access. If an assailant has root access, a user has problems beyond iCloud monitoring. Methods of penetration have been demonstrated previously..
Once it is loaded, however, it's believed that the Pegasus malware copies the login credentials used to access cloud storage. That information is then sent to the government or other organization using the malware, and they then have full access to that cloud storage.
According to sales documents, the system works with even the latest iPhones and Android phones.
Apple responded to reporters from the FT, saying that its iOS is "the safest and most secure computing platform in the world." Apple has managed to block previous versions of Pegasus, both on iOS and macOS.
"While some expensive tools may exist to perform targeted attacks on a very small number of devices," continued Apple, "we do not believe these are useful for widespread attacks against consumers."
Similarly, Microsoft said it is "continually evolving" its protections. Amazon and Microsoft say they're investigating.

Comments
Sounds like an old joke about viruses on Linux - they work if you find and install correct versions of all necessary libraries.
At the same time it's pretty unlikely they have any interest in you, probably as likely as the CIA sending an operative to your home posing as your internet service provider.
“some expensive tools may exist to perform targeted attacks on a very small number of devices, we do not believe these are useful for widespread attacks against consumers.”
Lots of claims by this company that sound like marketing tropes and little evidence that they can do what they say they can do, at least on iOS anyway.
Simple example of a targeted attack:
Journo critical of a government enters that country to report on issue X. At customs, journo's devices are taken for "inspection" by customs agents.
I'm sure we can all come up with any number of valid scenarios where governments around the world would have ability to gain physical access to a target's devices.
The larger problem is software and devices like this always, always, always make it into the hands of individuals with bad intent. Sometimes it's the actual gov'ts. Sometimes it some shady a-hole buying Cellebrite's tools off eBay.
Apple can't close every security hole, but they do a darn good job of securing Apple devices against things most folks should have any concern with. This in not one of those things.
Any time your phone leaves your possession you’re vulnerable. The simplest way is if you go through a border or customs, if you’re required to give up your password or unlock your device you’re SOL.
You could bring a “burner” phone or phone set up with a dummy account. After getting to your destination, you’d need to wipe the device and set it up properly.
Technically, someone could physically modify your device if it leaves your possession but it would be difficult to do so...
After doing your business, and uploading everything to iCloud, one drive, etc. you’d need to wipe the device before going back through customs.
Some country’s forbid or block the use of VPNs (etc.) so downloading the software at your destination would be a problem...
This (and other tools) is 1984 made easy/cheap, but the bigger problem is when these tools become available to every petty criminal... and they inevitably will. It wouldn’t be that difficult to weaponize this tools inside Apps that users install inadvertently...
Remember, a “free” App isn’t free. The FaceApp that’s making rounds in the news is just the tip of the iceberg, and that’s only getting attention because of its Russian origin. If it was from Israel (etc) would it get flagged?
As far as know, root access can only be gained by jailbraking. So not possible to install from App Store.