Twitter confirms staff manipulated for high-profile account access by hackers
Twitter's employees were manipulated into providing access to the social network's internal systems to attackers, the company has revealed in an update to its investigation into a recent Bitcoin scam, one that affected prominent accounts including Apple.

Published late on Friday, the update details what Twitter's security teams believes happened on July 15, which saw a number of Twitter accounts with high follower accounts post a tweet designed to take Bitcoin payments from the account's readers.
Twitter's summary of events seemingly confirms early reports claiming some sort of social engineering was attempted, the microblogging service believes attackers targeted "certain Twitter employees" and was successful with a small number. Credentials acquired via the scheme were then used to access Twitter's internal systems, including getting through the company's two-factor protections.
As of the time of the update, Twitter believes only 130 accounts were targeted in the attack, which included Apple and personalities such as Tesla's Elon Musk and Amazon's Jeff Bezos. For 45 of the accounts, attackers were able to "initiate a password reset, login to the account, and send tweets."
Up to eight of the accounts were also subjected to an extra step, where the attackers used the "Your Twitter Data" tool to acquire more details about the account and the user. Interestingly none of the eight accounts this happened to were verified accounts.
Following the discovery of the attack, Twitter's incident response team secured and revoked access to the systems to prevent any further damage. Other preemptive measures were also taken by the team, including preventing accounts from tweeting or changing passwords "to prevent the attackers from further spreading their scam as well as to prevent them from being able to take control of any additional accounts" while the investigation was in progress.
Multiple teams are said to be working around the clock and with law enforcement on the investigation, and determining longer-term actions Twitter needs to implement to improve its security.
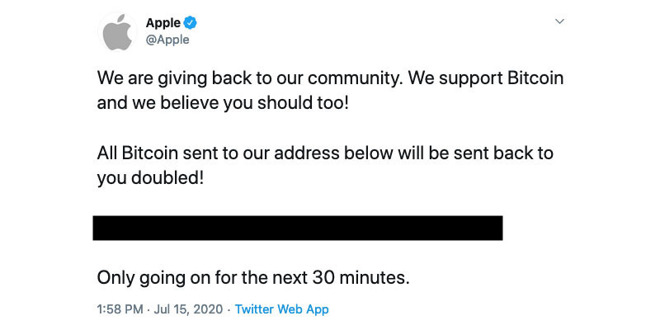
The now-deleted tweet from Apple's Twitter account
In terms of the information that the attackers were able to access, Twitter believes the private details for the "vast majority" of accounts wasn't accessed. For the known 130 accounts, Twitter knows the attackers were not able to see previous account passwords as they were not stored in plain text nor available in tools, but they were able to view personal information including email addresses and phone numbers.
Twitter claims it is "actively working on communicating directly with the account-holders that were impacted" by the breach.
Along with restoring account access to still-locked accounts, continuing the investigation, and increasing system security, Twitter will be instigating company-wide training to "guard against social engineering tactics," furthering training received through onboarding and its regular self-instigated phishing exercises.
"We're acutely aware of our responsibilities to the people who use our service and to society more generally," the update concludes in its apology. "We know that we must work to regain your trust, and we will support all efforts to bring the perpetrators to justice."
The update ends "We hope that our openness and transparency throughout this process, and the steps and work we will take to safeguard against other attacks in the future, will be the start of making this right."
Published late on Friday, the update details what Twitter's security teams believes happened on July 15, which saw a number of Twitter accounts with high follower accounts post a tweet designed to take Bitcoin payments from the account's readers.
Twitter's summary of events seemingly confirms early reports claiming some sort of social engineering was attempted, the microblogging service believes attackers targeted "certain Twitter employees" and was successful with a small number. Credentials acquired via the scheme were then used to access Twitter's internal systems, including getting through the company's two-factor protections.
As of the time of the update, Twitter believes only 130 accounts were targeted in the attack, which included Apple and personalities such as Tesla's Elon Musk and Amazon's Jeff Bezos. For 45 of the accounts, attackers were able to "initiate a password reset, login to the account, and send tweets."
Up to eight of the accounts were also subjected to an extra step, where the attackers used the "Your Twitter Data" tool to acquire more details about the account and the user. Interestingly none of the eight accounts this happened to were verified accounts.
Following the discovery of the attack, Twitter's incident response team secured and revoked access to the systems to prevent any further damage. Other preemptive measures were also taken by the team, including preventing accounts from tweeting or changing passwords "to prevent the attackers from further spreading their scam as well as to prevent them from being able to take control of any additional accounts" while the investigation was in progress.
Multiple teams are said to be working around the clock and with law enforcement on the investigation, and determining longer-term actions Twitter needs to implement to improve its security.

The now-deleted tweet from Apple's Twitter account
In terms of the information that the attackers were able to access, Twitter believes the private details for the "vast majority" of accounts wasn't accessed. For the known 130 accounts, Twitter knows the attackers were not able to see previous account passwords as they were not stored in plain text nor available in tools, but they were able to view personal information including email addresses and phone numbers.
Twitter claims it is "actively working on communicating directly with the account-holders that were impacted" by the breach.
Along with restoring account access to still-locked accounts, continuing the investigation, and increasing system security, Twitter will be instigating company-wide training to "guard against social engineering tactics," furthering training received through onboarding and its regular self-instigated phishing exercises.
"We're acutely aware of our responsibilities to the people who use our service and to society more generally," the update concludes in its apology. "We know that we must work to regain your trust, and we will support all efforts to bring the perpetrators to justice."
The update ends "We hope that our openness and transparency throughout this process, and the steps and work we will take to safeguard against other attacks in the future, will be the start of making this right."

Comments
Good Lord, I'm sorry but try as I may, I can't seem to muster much sympathy for the people dumb enough to fall for this one.
This is even dumber then the ever so slightly less obvious "African Prince" emails.
Oh-ooh Darwin … please believe me … I'll never do you no harm …
https://www.microsoft.com/en-us/research/publication/why-do-nigerian-scammers-say-they-are-from-nigeria/?from=http%3A%2F%2Fresearch.microsoft.com%2Fpubs%2F167719%2Fwhyfromnigeria.pdf
They even claim they’re from Nigeria when they’re not, because if that doesn’t make you suspicious then nothing will, apparently.
There will always be ways to create situations where someone might be tempted to do something that could potentially be exploited.
For instance, if the staff use hardware tokens (that must be physically touched when a login happens) an attacker could give the appearance of a bad network connection (requiring the user to login again each time) to trick the staff into giving access to the systems.
Training for something like that is very hard because part of a good security system is also to kick people out to avoid idle connections to be highjacked (sometimes due to physical access to the computer), so the user might be very used to having to login repeated during the day; and it's not always obvious even to the designers of such a system when it's a legit situation, or a cleverly designed attack.
And… it keeps being like that… for every "smart" thing you might think of I could give an example of how the waters would get muddled by a potential attack vector. (Including that we might reach a point where what you suggest would be secure, but it would create such a silly situation that the staff couldn't easily do their job; or the company would have to spend a fortune hiring only highly skilled security experts, and then retrain them into doing the actual work needed, like being doormen, secretaries, kitchen staff, etc.)
Life happens.
Sure, the simple attacks won't even work, and the obvious stuff will be, well, obvious; but once a new attack vector is found and exploited right, then it will fit in perfectly with the actions that the security system itself forces the users to take.
For instance, how often don't we all just push a button repeatedly when it doesn't work, or when our credit card doesn't work we repeatedly "blipp", swipe, and insert it (and/or try different codes)… and so on… so we're all conditioned to automatically try again when tech doesn't work; and all of that are perfectly good examples of situations where we could be tricked into repeatedly handing over new codes.
I used to observe the way my IT/support customers were conditioned to respond to dialog boxes by inserting error conditions that didn’t even exist (“your device is not ready to be used”, when it says “your device is now ready to be used”), because that’s what they expect: yet another problem.
We have countless egregious examples of just how buggy and flawed our most frequently used computer tech is (iOS, from supposedly the most brilliant tech company ever, is a pile of bugs and conflicting gestures). From mysteriously offline back-end systems that we just wait for our service providers to reboot, to obvious crashed signage. From cheaply built physical hardware to badly designed UIs.
The state of being flawed is normalized by the tech geeks. “You don’t understand how complex software is” becomes a special pleading (logical fallacy) defense of inherently bad tech. Non-tech users and customers are bullied into accepting it because where is there any other option? Free market? Ha ha ha ha ha. The state of computing itself, and the culture of “everything has bugs”, is the problem, not the individual brands (though yesterday’s Apple were more strict about the number of bugs they allowed in shipping products and used to have design so good that it pushed the industry forward a little bit; but no longer).
When is this industry going to finally mature? Lawmakers are so clueless about the industry that they can barely ask the right questions when they finally get some tech executives into a deposition. They don’t know when to call BS on said executives.
This is full blown CULTURE. Almost nobody knows how to see outside the context of broken crap as a norm.
You must have scored one hundred percent in every assessment you've undergone in your life.
Someone of your ability must be incredibly wealthy from providing complex products and/or services that are flawless.
Yet with all your talent, it's incomprehensible why you've failed to persuade the tech geeks and industry to follow your perfectly superior approach.
First of all , Training should be on going for staff. You don't wait for the wheels to fall off the bus and then say you are going to train your staff. The IT dept. is F.U.B.R.
Their security was probably more than decent, with on going training and all, but then something unexpected happened; and there's no real quick fix to it all, and no one in particular to blame, so the public announcement becomes "we will invest in making stuff better, we promise", because anything else would cause people to freak out and the valuation drop.
So don't sit there like you're commenting based on some deep inside knowledge when you can't even tell real facts from the usual stuff that comes from PR people.
Then they need new PR people. The attack vector they quote does not give confidence in their training.