iMessage Contact Key Verification appears in first iOS 16.6 beta
One of the first found feature changes in iOS 16.6 and iPadOS 16.6 may be an iMessage verification system that could help prevent government agencies from eavesdropping on the conversations of critics.
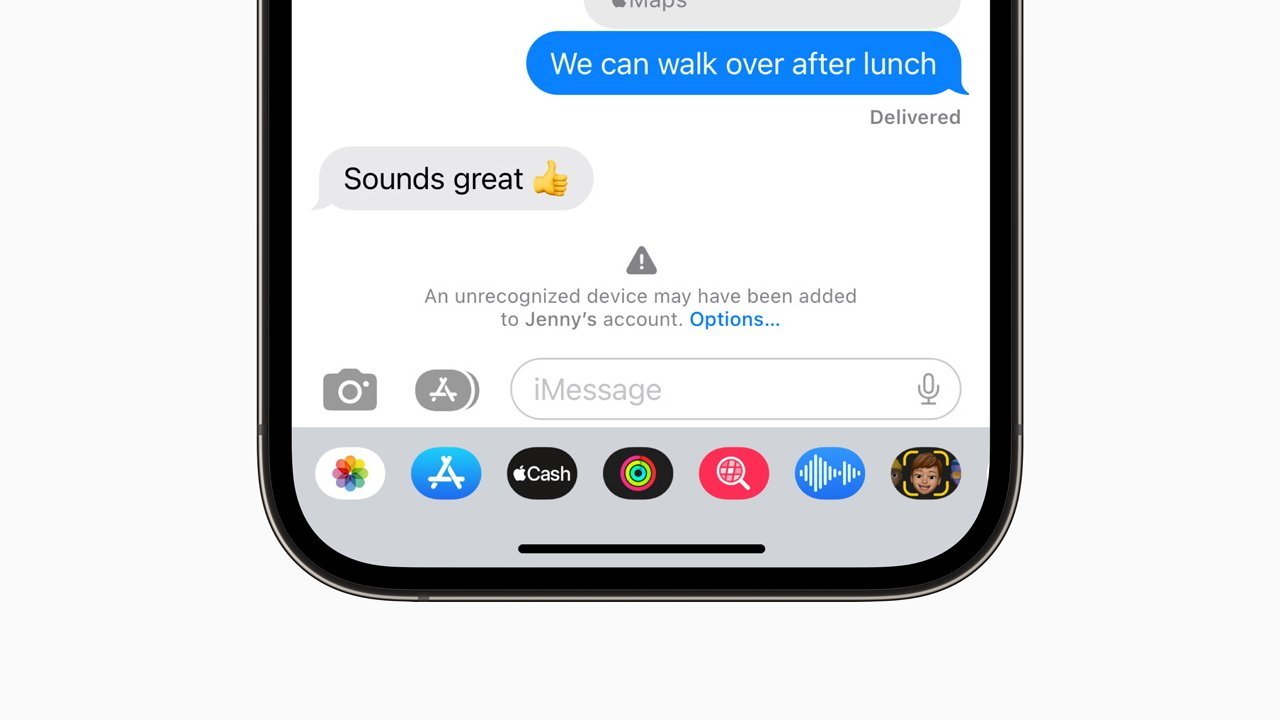
An example of an alert from iMessage Contact Key Verification
In December 2022, Apple introduced a number of security protections to help protect the sensitive data of its users in iCloud and iMessage. Months later, in the first beta of iOS 16.6 and iPadOS 16.6, Apple seems to be preparing to take one of the features live.
Released on May 19, the first developer beta of the new cycle includes a setting in iMessage to enable iMessage Contact Key. While the setting exists in the beta, reports MacRumors, it doesn't appear that the setting has been enabled in iOS itself, making its appearance an indicator that it should arrive in the near future.
During its introduction, Apple said that iMessage Contact Key Verification would arrive sometime in 2023, but not when.
The feature works as an enhancement to existing end-to-end encryption in iMessage itself, and specifically targets users who face what Apple refers to as"extraordinary digital threats." This refers to journalists, human rights activists, and members of government who may face attempts to break Apple's security and to eavesdrop on messaging conversations.
The Contact Key Verification feature allows a user to verify they are messaging only with the intended recipient, without interference from outside forces. For added security, users can verify with each other by comparing a Contact Verification Code in person, over FaceTime, or via other secured communications.
Users who have enabled iMessage Contact Key Verification will be alerted automatically if a state-sponsored attacker were to somehow succeed in breaching cloud servers or to otherwise find a way to monitor encrypted communications.
Read on AppleInsider

An example of an alert from iMessage Contact Key Verification
In December 2022, Apple introduced a number of security protections to help protect the sensitive data of its users in iCloud and iMessage. Months later, in the first beta of iOS 16.6 and iPadOS 16.6, Apple seems to be preparing to take one of the features live.
Released on May 19, the first developer beta of the new cycle includes a setting in iMessage to enable iMessage Contact Key. While the setting exists in the beta, reports MacRumors, it doesn't appear that the setting has been enabled in iOS itself, making its appearance an indicator that it should arrive in the near future.
During its introduction, Apple said that iMessage Contact Key Verification would arrive sometime in 2023, but not when.
The feature works as an enhancement to existing end-to-end encryption in iMessage itself, and specifically targets users who face what Apple refers to as"extraordinary digital threats." This refers to journalists, human rights activists, and members of government who may face attempts to break Apple's security and to eavesdrop on messaging conversations.
The Contact Key Verification feature allows a user to verify they are messaging only with the intended recipient, without interference from outside forces. For added security, users can verify with each other by comparing a Contact Verification Code in person, over FaceTime, or via other secured communications.
Users who have enabled iMessage Contact Key Verification will be alerted automatically if a state-sponsored attacker were to somehow succeed in breaching cloud servers or to otherwise find a way to monitor encrypted communications.
Read on AppleInsider

Comments
Us commoners have nothing to worry about anyway, we aren't that valuable or interesting.
That way, if someone manages to log in as you to iCloud by stealing credentials or somehow breaching iCloud, they can't just use any iPhone to log in and communicate as you without the other part knowing you're using a new device, the other party will know since they've never seen your device key before.
How does it know which ones are real and which ones are eavesdroppers? If it can tell, why not just prevent the eves-dropper from connecting in the first place?
iMessage allows its users to sync their conversations between devices logged in on the same iCloud account so that you can continue on your iPhone, iPad, or Mac regardless of where it was initiated. Previously when a new device was added, only the adding party was notified of the new device. With this new setting both parties will be notified.
Maybe there’s a write up somewhere…
On the one hand, it addresses a long-standing design flaw in iMessage -- it was impossible to verify the identify of the other party. You just had to blindly trust the Apple provided the right encryption key to you, and you weren't subject to a man-in-the-middle attack. This is opposed to Signal and WhatsApp which support verification. Basically, these systems create a "fingerprint" of the encryption keys used in your conversation -- both parties can verify this fingerprint to ensure they both see the same keys.
Historically, iMessage did not have this -- so you could not know if you were really talking directly to someone or if your conversation was being relayed through an eavesdropper, or if Apple had secretly added an eavesdropper to your conversation. Now, this will be possible.
Edit: WhatsApp is actually innovating here. Most users do not manually verify safety numbers, so WhatsApp is rolling out an automatic key verification system which has a public log of all public keys in the system. See this announcement for a high-level overview. There is also an extended deep-dive discussion on the Security Cryptography Whatever podcast.