What you need to know about security keys on iOS and macOS
A physical security key, like a YubiKey, is an excellent way to bolster your two-factor authentication and help keep your online accounts and data safe from attackers. Here's what you need to know about using them on iOS and macOS.

While all forms of two-factor authentication are better than relying on just a password alone, a physical key carries a number of benefits over more popular methods like one-time passcodes (OTP). If you're not sure where to start, here are some basics.
Two-factor authentication (2FA) adds that second element -- something you have -- as a required step during the login process. But most basic 2FA systems rely on passcodes sent via SMS text message, a method that's vulnerable to skilled attackers and techniques like SIM-jacking.
Security keys can help do away with some of the inherent vulnerabilities. They're essentially a small device about the size and shape of a USB drive. Once they're set up, you just plug them into your device and use them as a second factor for authentication.
By requiring physical access to your key, it significantly reduces the chance that someone will be able to break into your accounts even if your passwords have been compromised.
There are many security keys available on the market today, but it's best to stick with ones that adhere to FIDO Universal 2nd Factor or U2F. Some popular manufacturers include Yubico, HyperFido and Thetis.
Security keys are generally much more secure than other 2FA methods.
Security keys are not the only option for 2FA or multi-factor authentication. And compared to other options, they have their own set of downsides.
For one, security keys aren't currently compatible with Apple ID or iCloud services. Apple relies on its own 2FA system, sending one-time passcodes to your trusted Apple devices.
Apple's 2FA is more secure than an SMS passcode. But you can't use Apple 2FA to secure your Gmail or Facebook accounts. That's where a third-party system comes in.
There are other options beyond physical security keys, such as authenticator apps which randomly generate one-time passcodes after specific intervals. These authenticator codes never leave your device, so they're also much more secure than SMS passcodes.
Like all one-time passcodes, authenticator apps are still vulnerable to certain types of phishing attacks. And if someone gained physical access to your iPhone or whatever device has your authenticator app, they could also gain access to your accounts.
A security key eliminates the phishing vulnerability because you're never required to copy, paste or type anything. Physical access to the key may be a concern, but someone would still need your password and you could always remove the key from your account at any time.
You can also use them to lock down your password manager vaults, although most password managers require a paid premium subscription to unlock that feature.
On macOS, you can use a security key on most web browsers. Some keys, like those made by Yubico, also allow you to actually lock your Mac device.
Compatibility on iOS is a bit more finicky. Most third-party apps that allow security keys will support them on their iOS apps. As of iOS and iPadOS 13.3, Apple also natively supports security keys when logging into online services in Safari.
Some security keys also offer short-range wireless authentication via NFC, including popular Yubico models like the YubiKey 5. If your smartphone or tablet doesn't support NFC, look for a key that features a compatible connector.
Yubico has a dedicated webpage with setup instructions for all of its compatible services. At the top of that page, you'll see instructions for more popular platforms, but you can scroll down until you see the platform you'd like to secure. But, as mentioned earlier, an Apple ID isn't among those supported services yet.
You can follow the links from that webpage, or navigate to your service's website directly. Once you do, it's usually a matter of finding the service's security settings page and adding a security key as a 2FA option.
Note that you'll want to make sure you have a backup 2FA method in case you ever lose your security key. That could be a secondary security key or an authenticator app. Just make sure you add a backup method during setup.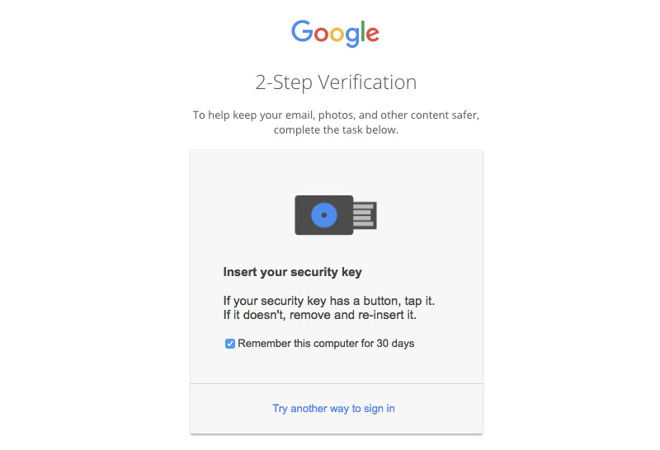
Most services will walk you through the steps of using a security key.
After you've added your security key as a second factor, you'll probably want to carry it with you wherever you go. Depending on your security settings, you won't be able to log into your accounts without it.
Like SMS-based 2FA, you won't need to use a security key when logging into trusted devices. Similarly, authenticating devices that are already logged into your accounts won't be necessary.
When it does come time to log into a 2FA-protected account, you'll usually plug your security key into a USB port on your computer or a Lightning port on your iPhone or iPad. As mentioned earlier, some keys support wireless authentication via NFC. If your key does, just hold it near your iPhone or NFC-compatible device.
Some models, like those by Yubico, will require you to physically make contact with the key itself. Usually, it'll be some type of contact point or button -- refer to your specific model's directions. Once you do, you should be logged in normally.
Despite that, security keys are still currently an excellent option for securing accounts, particularly for high-risk or security-conscious users. And as they become more popular, it's likely that services like Apple will adopt them more widely across the board.
The increasing prevalence of data breaches, phishing attacks and other security risks are going to make 2FA systems like security keys and authenticator apps much more necessary in the future.
But whether you start using security keys sooner, later or never, the important part is to be aware of all the limitations of your security. Using any type of 2FA is a step in the right direction.

While all forms of two-factor authentication are better than relying on just a password alone, a physical key carries a number of benefits over more popular methods like one-time passcodes (OTP). If you're not sure where to start, here are some basics.
What is a physical security key?
Account security with two-factor authentication largely comes down to two things -- something you know like a password, and something you have like access to a phone for OTP codes.Two-factor authentication (2FA) adds that second element -- something you have -- as a required step during the login process. But most basic 2FA systems rely on passcodes sent via SMS text message, a method that's vulnerable to skilled attackers and techniques like SIM-jacking.
Security keys can help do away with some of the inherent vulnerabilities. They're essentially a small device about the size and shape of a USB drive. Once they're set up, you just plug them into your device and use them as a second factor for authentication.
By requiring physical access to your key, it significantly reduces the chance that someone will be able to break into your accounts even if your passwords have been compromised.
There are many security keys available on the market today, but it's best to stick with ones that adhere to FIDO Universal 2nd Factor or U2F. Some popular manufacturers include Yubico, HyperFido and Thetis.
How security keys compare to other 2FA methods

Security keys are generally much more secure than other 2FA methods.
Security keys are not the only option for 2FA or multi-factor authentication. And compared to other options, they have their own set of downsides.
For one, security keys aren't currently compatible with Apple ID or iCloud services. Apple relies on its own 2FA system, sending one-time passcodes to your trusted Apple devices.
Apple's 2FA is more secure than an SMS passcode. But you can't use Apple 2FA to secure your Gmail or Facebook accounts. That's where a third-party system comes in.
There are other options beyond physical security keys, such as authenticator apps which randomly generate one-time passcodes after specific intervals. These authenticator codes never leave your device, so they're also much more secure than SMS passcodes.
Like all one-time passcodes, authenticator apps are still vulnerable to certain types of phishing attacks. And if someone gained physical access to your iPhone or whatever device has your authenticator app, they could also gain access to your accounts.
A security key eliminates the phishing vulnerability because you're never required to copy, paste or type anything. Physical access to the key may be a concern, but someone would still need your password and you could always remove the key from your account at any time.
Compatible services on iOS and macOS
Pretty much any online account or platform that offers non-passcode 2FA will support security keys, although your own mileage may vary. That includes social media sites and online services like Google, Facebook, Twitter and Dropbox.You can also use them to lock down your password manager vaults, although most password managers require a paid premium subscription to unlock that feature.
On macOS, you can use a security key on most web browsers. Some keys, like those made by Yubico, also allow you to actually lock your Mac device.
Compatibility on iOS is a bit more finicky. Most third-party apps that allow security keys will support them on their iOS apps. As of iOS and iPadOS 13.3, Apple also natively supports security keys when logging into online services in Safari.
Some security keys also offer short-range wireless authentication via NFC, including popular Yubico models like the YubiKey 5. If your smartphone or tablet doesn't support NFC, look for a key that features a compatible connector.
Setting up a security key
The exact setup process for getting up and running will vary by model but is pretty much the same across the board -- there is an identification or linking process, and that's about it. While Google has their own physical security key, and so do other vendors, for the purposes of this piece, we'll stick to the most popular security key manufacturer, Yubico.Yubico has a dedicated webpage with setup instructions for all of its compatible services. At the top of that page, you'll see instructions for more popular platforms, but you can scroll down until you see the platform you'd like to secure. But, as mentioned earlier, an Apple ID isn't among those supported services yet.
You can follow the links from that webpage, or navigate to your service's website directly. Once you do, it's usually a matter of finding the service's security settings page and adding a security key as a 2FA option.
Note that you'll want to make sure you have a backup 2FA method in case you ever lose your security key. That could be a secondary security key or an authenticator app. Just make sure you add a backup method during setup.
Using a security key

Most services will walk you through the steps of using a security key.
After you've added your security key as a second factor, you'll probably want to carry it with you wherever you go. Depending on your security settings, you won't be able to log into your accounts without it.
Like SMS-based 2FA, you won't need to use a security key when logging into trusted devices. Similarly, authenticating devices that are already logged into your accounts won't be necessary.
When it does come time to log into a 2FA-protected account, you'll usually plug your security key into a USB port on your computer or a Lightning port on your iPhone or iPad. As mentioned earlier, some keys support wireless authentication via NFC. If your key does, just hold it near your iPhone or NFC-compatible device.
Some models, like those by Yubico, will require you to physically make contact with the key itself. Usually, it'll be some type of contact point or button -- refer to your specific model's directions. Once you do, you should be logged in normally.
Only the beginning of security keys on macOS and iOS
Security keys are not incredibly popular at this point. Because of that, many services and account types aren't compatible with them. Even if they are, compatibility isn't always implemented well.Despite that, security keys are still currently an excellent option for securing accounts, particularly for high-risk or security-conscious users. And as they become more popular, it's likely that services like Apple will adopt them more widely across the board.
The increasing prevalence of data breaches, phishing attacks and other security risks are going to make 2FA systems like security keys and authenticator apps much more necessary in the future.
But whether you start using security keys sooner, later or never, the important part is to be aware of all the limitations of your security. Using any type of 2FA is a step in the right direction.

Comments
2FA by picking up the device + FaceID. If you reboot the device you need the password (or if the device hasn’t been unlocked for a while).
I’m not a fan of the OTP that Apple uses because it seems to require a second Apple device. If you own an Apple Watch your probably good to go, but how many people carry their iPad with them...
Looks like a geek toy.