Apple engineers partner with Cloudflare to improve internet privacy
Engineers at Apple are working with Cloudflare and Fastly to create Oblivious DNS, a new standard that can make it harder to track a user's online activities.

While the Internet offers various privacy protection measures for its denizens, including encryption and VPNs, one of the areas that are more easily trackable is the Domain Name System. Effectively the address book for the Internet, DNS enables the use of domain names that link to specific website IP addresses, making the entire system more usable to humans.
However, the nature of DNS means it is sent and received between machines in cleartext, which is easily observed by third parties, making it a trackable item. Developments like DNS over HTTPS (DoH) make it harder for outside forces to change DNS queries to point to malicious sites, but it still makes it possible for user activities to be tracked.
In a bid to make DNS more private and less trackable, a group of engineers at Apple, Cloudflare, and Fastly have come up with Oblivious DNS over HTTPS (ODoH). By separating the IP address from the query, it offers the chance for DNS queries to be made safer as not all parties have access to both the IP or query at the same time.
The DoH server is able to decrypt the query, produces an answer to it, encrypts that answer, and sends it back to the proxy, which then sends it back to the client.
In effect, the proxy is aware of encrypted messages between the client and the DoH server, but not the message content. Meanwhile, the DoH server knows the content of the message itself, but only the address of the proxy, not the client.
While it would be theoretically possible for the contents of the message and the address of the client to be combined if both the proxy and DoH server are owned by the same entity, a fundamental rule of it is that the proxy and DoH server do not collude at all.
In practice, this would largely consist of ensuring the proxy and DoH server are owned by different companies.
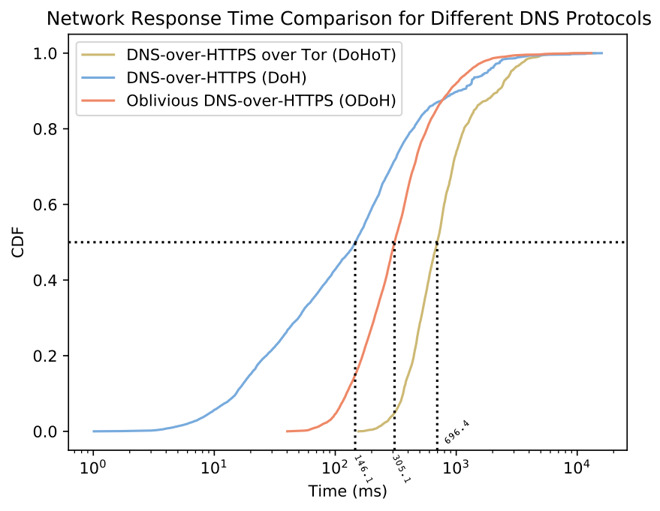
Cloudflare's graph showing the network response time for ODoH versus DoH and DoH over Tor.
The addition of encryption and decryption, as well as a proxy, to a DNS query may cause some concern for users who want their DNS queries to operate as fast as possible. To head off those worries, Cloudflare claims its initial testing of ODoH configurations are actually quite promising.
According to the company, the additional encryption is "marginal" in its effect, with a time cost of less than 1 millisecond for 99% of queries.
While the existing effort is meant to refine the system further, it may be quite some time before it becomes usable by consumers. Despite Apple being involved in the project, it doesn't guarantee that it will appear in iOS, macOS, or Safari anytime soon.
The longest wait will be for it to be certified as a standard by the Internet Engineering Task Force, which will make it more attractive to developers to implement.

While the Internet offers various privacy protection measures for its denizens, including encryption and VPNs, one of the areas that are more easily trackable is the Domain Name System. Effectively the address book for the Internet, DNS enables the use of domain names that link to specific website IP addresses, making the entire system more usable to humans.
However, the nature of DNS means it is sent and received between machines in cleartext, which is easily observed by third parties, making it a trackable item. Developments like DNS over HTTPS (DoH) make it harder for outside forces to change DNS queries to point to malicious sites, but it still makes it possible for user activities to be tracked.
In a bid to make DNS more private and less trackable, a group of engineers at Apple, Cloudflare, and Fastly have come up with Oblivious DNS over HTTPS (ODoH). By separating the IP address from the query, it offers the chance for DNS queries to be made safer as not all parties have access to both the IP or query at the same time.
How does ODoH work?
The system works by relying on both public key encryption and a network proxy sitting between the client and the DoH server. The query is encrypted by the client and dispatched to the DoH server via the proxy.The DoH server is able to decrypt the query, produces an answer to it, encrypts that answer, and sends it back to the proxy, which then sends it back to the client.
In effect, the proxy is aware of encrypted messages between the client and the DoH server, but not the message content. Meanwhile, the DoH server knows the content of the message itself, but only the address of the proxy, not the client.
While it would be theoretically possible for the contents of the message and the address of the client to be combined if both the proxy and DoH server are owned by the same entity, a fundamental rule of it is that the proxy and DoH server do not collude at all.
In practice, this would largely consist of ensuring the proxy and DoH server are owned by different companies.

Cloudflare's graph showing the network response time for ODoH versus DoH and DoH over Tor.
The addition of encryption and decryption, as well as a proxy, to a DNS query may cause some concern for users who want their DNS queries to operate as fast as possible. To head off those worries, Cloudflare claims its initial testing of ODoH configurations are actually quite promising.
According to the company, the additional encryption is "marginal" in its effect, with a time cost of less than 1 millisecond for 99% of queries.
When will ODoH be ready to use?
On Tuesday, Cloudflare and its partners, including PCCW Global, Surf, and Equinix have launched Oblivious DNS over HTTPS proxies, to encourage its further development and implementation, using Cloudflare's 1.1.1.1 DNS resolver. Test clients have been open-sourced, to allow interested parties to test it out for themselves.While the existing effort is meant to refine the system further, it may be quite some time before it becomes usable by consumers. Despite Apple being involved in the project, it doesn't guarantee that it will appear in iOS, macOS, or Safari anytime soon.
The longest wait will be for it to be certified as a standard by the Internet Engineering Task Force, which will make it more attractive to developers to implement.

Comments
Are you using a single PiHole for all of your devices?