Flaw in macOS Archive Utility let attackers bypass Gatekeeper
One of the best reasons to keep macOS up to date is protecting yourself against security issues -- and Jamf found a big one in the summer of 2022 that allowed attackers to bypass macOS Gatekeeper.

macOS Archive Utility
Jamf Threat Labs found the vulnerability in macOS Monterey 12.5. The company reported it to Apple on May 31, 2022, and Apple patched it in July.
Jamf says it started when its team found a flaw in Safari that could bypass Mac endpoint security, a system API that monitors for potentially malicious activity.
Prior to the patch, an attacker could put a malicious app inside a ZIP file using a specific Terminal command to exploit the Safari flaw. After the team reported that flaw to Apple, they researched other archiving features that could be vulnerable to similar issues.
Jamf found that creating an Apple Archive using Archive Utility with a similar command resulted in the file bypassing Gatekeeper and all security checks upon opening with a double click.
An Apple Archive is the company's proprietary format that allows for lossless compression. These files have an extension ".aar" when shown in Finder. However, the team says the flaw isn't limited to Apple Archives.
When Archive Utility extracts an archive, it applies the quarantine attribute to all extracted items.
In their example, the team added an image file outside the usual place where the system applies com.apple.quarantine. Then, when Archive Utility unarchived the file, that image did not have the quarantine attribute, even though the other files did have it.

The file without a quarantine attribute
As a result, Gatekeeper won't check that file outside the usual directory within the archive. Instead of an image file used in the example, an attacker could add a malicious application.
Then, when the user opens the archive they downloaded from the internet, the malicous code could automatically run, and the user wouldn't see a security prompt by the system.
Users can download other security apps, such as antivirus or antimalware.
Tools from Objective See are a popular alternative to antivirus, although they can be used in tandem. They're free, open-source apps that complement the Mac's native security.
iOS 16 Rapid Security Response
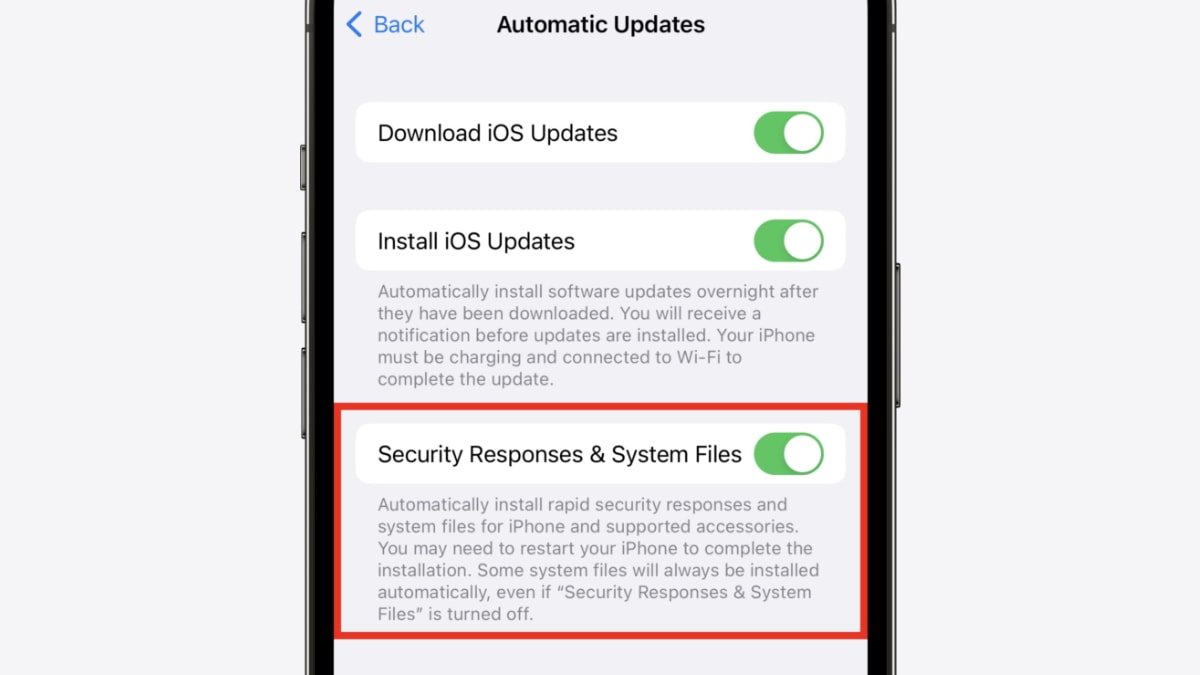
In iOS 16, iPadOS 16, and macOS Ventura, Apple has a feature called Rapid Security Response. It lets the company send security updates to devices without needing a full software update.
On iOS 16 and iPadOS 16, it's found in Settings > General > Software Update > Automatic Updates. A toggle called "Install Security Responses & System Files" says that patches for security bugs and system files will be automatically installed.
The user may need to restart their device to complete the installation, but some system files may be installed automatically even if the toggle is turned off.
Read on AppleInsider

macOS Archive Utility
Jamf Threat Labs found the vulnerability in macOS Monterey 12.5. The company reported it to Apple on May 31, 2022, and Apple patched it in July.
Jamf says it started when its team found a flaw in Safari that could bypass Mac endpoint security, a system API that monitors for potentially malicious activity.
Prior to the patch, an attacker could put a malicious app inside a ZIP file using a specific Terminal command to exploit the Safari flaw. After the team reported that flaw to Apple, they researched other archiving features that could be vulnerable to similar issues.
Archive Utility
After testing macOS Archive Utility, a built-in app that can compress and uncompress files, they found a different flaw. It's tracked as CVE-2022-32910 in the Common Vulnerabilities and Exposures database that keeps track of security flaws across platforms.Jamf found that creating an Apple Archive using Archive Utility with a similar command resulted in the file bypassing Gatekeeper and all security checks upon opening with a double click.
An Apple Archive is the company's proprietary format that allows for lossless compression. These files have an extension ".aar" when shown in Finder. However, the team says the flaw isn't limited to Apple Archives.
How Safari is linked
Jamf explains that when an archive is downloaded from the internet, it has a unique attribute added to it called com.apple.quarantine. It tells macOS that the file has been downloaded from a remote source and should be checked before it's allowed to run.When Archive Utility extracts an archive, it applies the quarantine attribute to all extracted items.
In their example, the team added an image file outside the usual place where the system applies com.apple.quarantine. Then, when Archive Utility unarchived the file, that image did not have the quarantine attribute, even though the other files did have it.

The file without a quarantine attribute
As a result, Gatekeeper won't check that file outside the usual directory within the archive. Instead of an image file used in the example, an attacker could add a malicious application.
Then, when the user opens the archive they downloaded from the internet, the malicous code could automatically run, and the user wouldn't see a security prompt by the system.
How to protect yourself
The most obvious way to protect yourself from this attack is by keeping macOS up to date, as the flaw has been patched since the summer.Users can download other security apps, such as antivirus or antimalware.
Tools from Objective See are a popular alternative to antivirus, although they can be used in tandem. They're free, open-source apps that complement the Mac's native security.

iOS 16 Rapid Security Response
In iOS 16, iPadOS 16, and macOS Ventura, Apple has a feature called Rapid Security Response. It lets the company send security updates to devices without needing a full software update.
On iOS 16 and iPadOS 16, it's found in Settings > General > Software Update > Automatic Updates. A toggle called "Install Security Responses & System Files" says that patches for security bugs and system files will be automatically installed.
The user may need to restart their device to complete the installation, but some system files may be installed automatically even if the toggle is turned off.
Read on AppleInsider

Comments
Hi Paul, the Console is a normal part of every operating system, it's a place where you can see your computer's "inner monologue" shall we say, the countless little status updates that all the background processes are generating behind the scenes. No need to worry about this, it's not a secret and it's not a security risk. Here's some articles about the Console that will hopefully put your mind at ease.
https://support.apple.com/guide/console/welcome/mac
https://macpaw.com/how-to/use-mac-console-app