iMessage may be coming to Android with Sunbird
Android users may finally get an easy way to get iMessage in 2023 thanks to a new app called Sunbird.

Sunbird Messenger
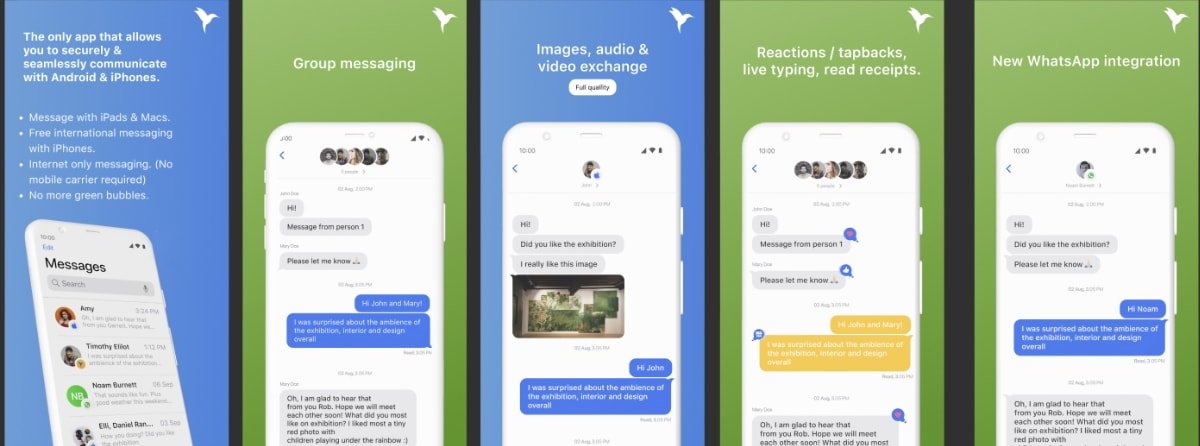
Launching in closed beta, for now, Sunbird claims it's the first and only fully-featured iMessage for Android app. It doesn't require a relay server, Apple device, or desktop software, only an Apple ID.
It supports encryption, full-quality photos and videos, iMessage group chats, reactions, tapbacks, live-typing indicators, and read receipts.
Apple's iMessage service is the main focus for now. In a conference with AppleInsider, the Sunbird team called it it the "low-hanging fruit" as they noticed how many Google searches exist for terms such as "iMessage on Android."
However, Sunbird aims to be a unified messaging app for many more services, including WhatsApp, Facebook Messenger, SMS/MMS, and others that the company will add in the future.
"We've solved 14 years of communications challenges associated with Android messaging," states Danny Mizrahi, CEO, and Founder of Sunbird Messaging. "By inventing new technology that gives Android users iMessage on Android, one can enjoy the most popular functions and features uniting the top messaging apps that people use every day. One inbox for all your messages."
The product roadmap for other messaging services includes Telegram, RCS, Instagram Direct Messaging, Slack, Signal, and Discord.
Sunbird is quick to mention that its servers never store personal data or third-party login information. All message types are end-to-end encrypted except for SMS, which doesn't support such security.
What Sunbird looks like
The company also plans to build a web app for Sunbird, but it doesn't have plans for an iOS app, at least currently.
Sunbird will roll out invitations in phases to join the closed beta user group beginning in late 2022. So far, the company hopes for a public release in mid-2023.
The app will be free for the foreseeable future.
There wasn't a clear indication if it was a live demo or not. The team did mention that their app is still in the early alpha stage.
They did answer a couple of questions surrounding privacy and security. Sunbird mentioned this subject more than once, saying that they don't store any user data or messages.
Services that it plans to include, such as iMessage and Signal, rely on end-to-end encryption. We asked if the company has done an independent security audit, and the team said that was on the roadmap for the future.
If the app does work as intended, it could be a major breakthrough for Android users. Instead of relying on non-encrypted methods such as Facebook Messenger or SMS, Sunbird may be able to provide a more private way to communicate with Apple friends and family.
Read on AppleInsider

Sunbird Messenger
Launching in closed beta, for now, Sunbird claims it's the first and only fully-featured iMessage for Android app. It doesn't require a relay server, Apple device, or desktop software, only an Apple ID.
It supports encryption, full-quality photos and videos, iMessage group chats, reactions, tapbacks, live-typing indicators, and read receipts.
Apple's iMessage service is the main focus for now. In a conference with AppleInsider, the Sunbird team called it it the "low-hanging fruit" as they noticed how many Google searches exist for terms such as "iMessage on Android."
However, Sunbird aims to be a unified messaging app for many more services, including WhatsApp, Facebook Messenger, SMS/MMS, and others that the company will add in the future.
"We've solved 14 years of communications challenges associated with Android messaging," states Danny Mizrahi, CEO, and Founder of Sunbird Messaging. "By inventing new technology that gives Android users iMessage on Android, one can enjoy the most popular functions and features uniting the top messaging apps that people use every day. One inbox for all your messages."
The product roadmap for other messaging services includes Telegram, RCS, Instagram Direct Messaging, Slack, Signal, and Discord.
Sunbird is quick to mention that its servers never store personal data or third-party login information. All message types are end-to-end encrypted except for SMS, which doesn't support such security.

What Sunbird looks like
The company also plans to build a web app for Sunbird, but it doesn't have plans for an iOS app, at least currently.
Sunbird will roll out invitations in phases to join the closed beta user group beginning in late 2022. So far, the company hopes for a public release in mid-2023.
The app will be free for the foreseeable future.
It's still early...
AppleInsider attended a presentation of the announcement. Sunbird showed a few demonstrations of the app, such as adding an integration with iMessage.There wasn't a clear indication if it was a live demo or not. The team did mention that their app is still in the early alpha stage.
They did answer a couple of questions surrounding privacy and security. Sunbird mentioned this subject more than once, saying that they don't store any user data or messages.
Services that it plans to include, such as iMessage and Signal, rely on end-to-end encryption. We asked if the company has done an independent security audit, and the team said that was on the roadmap for the future.
If the app does work as intended, it could be a major breakthrough for Android users. Instead of relying on non-encrypted methods such as Facebook Messenger or SMS, Sunbird may be able to provide a more private way to communicate with Apple friends and family.
Read on AppleInsider

Comments
I doubt Apple could target this client and ban anybody using it. I also don't see them going out of their way to break it, but if a change eventually does break it, Apple definitely won't care.
Most (if not all modern) Android devices include a secure enclave as well. When the user signs in to iMessage for the first time on the device by authenticating with their iCloud credentials, that is when the client generates the encryption keys, stores the private key in the secure enclave, and registers the public key with the iMessage server. So long as they have fully rerverse-enginered the API protocol from sign-in to sending/receiving messages, then it is pretty straightforward and largely identical to the iPhone workflow for the same operations.
It does require a relay server, it's just they provide one for you, presumably including a virtual Mac.
What they are describing sounds a lot like Matrix using the puppet bridge:
https://matrix.org/docs/projects/bridge/matrix-appservice-imessage
I can't see any major breakthrough for Android users. They don't have to rely on unencrypted messages (and Messenger is available on iOS too).
If anything, the breakthrough would be for iOS users as many Messages users probably don't know their messages are being sent, unencrypted, as SMS to Android users in their address books.
Added to that, Messages is probably not used very much at all outside the US. I know no iOS user that uses it.
It is basically Whatsapp all the way for everyone.
It's functionally the Turing test, except the interrogator trying to differentiate between the computer and the person is a computer, and it only speaks the iMessage protocol. As long as the other two parties to the test speak the iMessage protocol equally well, the interrogator won't be able to tell the difference.
Reverse engineering for interoperability is specifically protected by every copyright system I'm familiar with. It's definitely protected in the USA.
That's to interact with the application Messages on an iPhone, iPad, or Mac. It has absolutely nothing to do with iMessage the protocol.