Critical security flaw is exposing older Wemo Smart Plugs to hackers
Researchers found a security flaw in an older version of the Wemo Mini Smart Plug that involved changing its name -- and Belkin isn't going to fix it.

Wemo Smart Plugs have a flaw
The Wemo Mini Smart Plug is designed to offer convenient remote control over lights and basic appliances, such as fan lamps, through a mobile app. The application utilizes Wi-Fi for communication and seamlessly integrates with HomeKit and other smart home ecosystems.
Among other functions, the app lets people change the device name. The length is limited to 30 characters or less, but only the app enforces that rule.
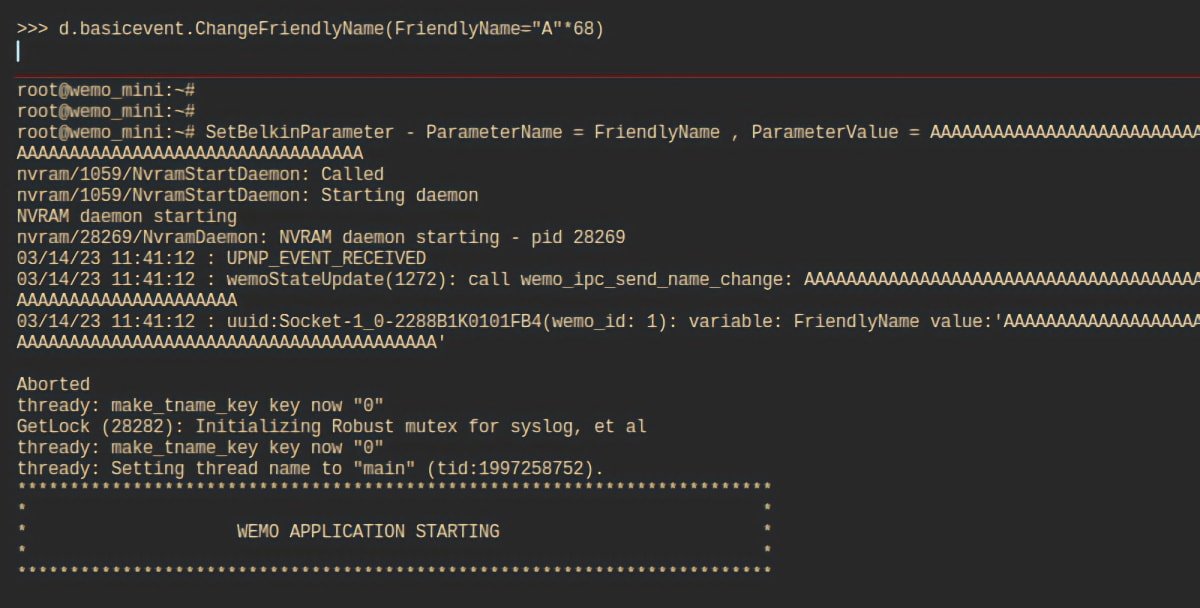
However, through reverse engineering, the security experts at Sternum discovered a method to circumvent the character limit, thereby triggering a buffer overflow. They subsequently named this vulnerability "FriendlyName."
A buffer overflow happens when there's too much information put into a storage area (buffer) that it can't handle. It's like pouring more water into a cup than it can hold, causing it to overflow.
That can lead to unexpected results in computer systems because the extra information can overwrite or change nearby data. Hackers can use a buffer overflow to gain unauthorized access or cause malfunctions in a computer program.
Accessing the firmware
The researchers from Sternum examined the smart plug's firmware and used it to change the device's name to one that was longer than the app's rule of 30 characters. The resulting overflow allowed them to issue commands to the device and control it.
In the hands of a malicious hacker, that could lead to data theft or possibly controlling other devices plugged into the Wemo device.
The team contacted Belkin to inform the company of the security flaw. However, Belkin said it wouldn't fix the vulnerability because the Wemo Smart Plug V2 is at the end of its life.
The current Wemo Smart Plug is version 4.
Considering the lack of future updates for version 2 of the Wemo device, there is also the option to explore newer smart plug alternatives if they desire ongoing support and enhancements.
Read on AppleInsider

Wemo Smart Plugs have a flaw
The Wemo Mini Smart Plug is designed to offer convenient remote control over lights and basic appliances, such as fan lamps, through a mobile app. The application utilizes Wi-Fi for communication and seamlessly integrates with HomeKit and other smart home ecosystems.
Among other functions, the app lets people change the device name. The length is limited to 30 characters or less, but only the app enforces that rule.
However, through reverse engineering, the security experts at Sternum discovered a method to circumvent the character limit, thereby triggering a buffer overflow. They subsequently named this vulnerability "FriendlyName."
A buffer overflow happens when there's too much information put into a storage area (buffer) that it can't handle. It's like pouring more water into a cup than it can hold, causing it to overflow.
That can lead to unexpected results in computer systems because the extra information can overwrite or change nearby data. Hackers can use a buffer overflow to gain unauthorized access or cause malfunctions in a computer program.

Accessing the firmware
The researchers from Sternum examined the smart plug's firmware and used it to change the device's name to one that was longer than the app's rule of 30 characters. The resulting overflow allowed them to issue commands to the device and control it.
In the hands of a malicious hacker, that could lead to data theft or possibly controlling other devices plugged into the Wemo device.
The team contacted Belkin to inform the company of the security flaw. However, Belkin said it wouldn't fix the vulnerability because the Wemo Smart Plug V2 is at the end of its life.
The current Wemo Smart Plug is version 4.
How to protect yourself from "Friendlyname"
Sternum says people who own one of these plugs shouldn't connect them to the internet. They also shouldn't be allowed to connect to sensitive devices on a home network.Considering the lack of future updates for version 2 of the Wemo device, there is also the option to explore newer smart plug alternatives if they desire ongoing support and enhancements.
Read on AppleInsider

Comments
Don’t you have to be on the WiFi network to do this and then don’t you already have a much bigger problem?
WiFi routers simply don't have enough differentiated features for Apple to stand out from the rest of the marketplace.
That's probably why they bailed on this market.
In any case, Apple cannot fix all of the problems of these poorly designed and poorly supported IoT devices. If a big, recognized company like Belkin won't support their brands, why would we expect other big companies to be any different. We've already seen Google abandon tons of hardware.
Even the best designed Apple router won't fix a buffer overflow vulnerability in a moldy old smart plug.
Once they have a toe-hold on your LAN, UPnP lets a device establish an inbound route through your router. But if the device is going to phone home anyway, how is UPnP making it worse?
As I mentioned, many of these vulnerabilities are based on the "possibility" of someone gaining access to your system due to a discovered issue, which in the case and many others, is the identification of code that is vulnerable to attack. Many of these vulnerabilities exist in code that has been thoroughly tested from a functional standpoint - but not from a security standpoint.
The exact issue with this specific vulnerability is due to the use of a C/C++ string copy function (strcpy) that does not inherently verify that the memory space allocated for the copied string is large enough to hold the string being copied. The developer obviously coded and verified that the failure condition could never be encountered through "normal" user interaction and took steps to protect themselves but obviously failed to consider every possible way the string could exceed the maximum size.
Is this a bug? From a design-for-security (DFS) perspective it is, but not all developers and development organizations followed DFS strategies when the code was written and tested and/or the safeguards they put in place were incomplete. The code was written tested, and deemed to be fully functional. But in the face of security threats, being fully functional is no longer good enough. It has to be secure too. (It also has to be "safe" from a number of other perspectives like thread safe, not leak memory, not leak private information, handle exceptions appropriately, handle locality issues like language, date & time formats, and units of measure correctly, etc., too, so being fully functional plus secure isn't even good enough.)
How common is this specific issue? Very common. These kinds of vulnerabilities are everywhere. All you have to do is go looking for them, as the team that discovered the Wemo issue did. There was nothing obvious to draw them to the particular Wemo model in question. All they had to do was examine its code, look for instances where known "unsafe" functions were being used, and see whether these unsafe functions could be exploited. It's very likely that many other devices from many different vendors would have yielded similar results. This is the nature of the security beast - if you think something is safe because it hasn't been identified as being vulnerable, it's more likely that the product simply has not been scrutinized for vulnerabilities. Over time this situation has improved, but we are nowhere near the point of saying that everything out there has actually been put to the test from a security standpoint. It hasn't.
Still, there's a huge difference between possibility and probability. The probability that a particular user of these Wemo smart plugs is going to be impacted is very remote. From a probability standpoint I think it is far more likely that a user of devices other than the one in question here would be impacted through an attack mechanism that has not yet been publicly identified, if for no other reason that this particular issue requires some enabling conditions that some users will now mitigate by shutting down at least one of the potential ingress mechanisms. There has to be some kind of reward for the attacker to go after someone, and in all likelihood you and I are not worth the effort.
As for UPnP, it doesn’t let devices discover other LAN devices. It lets them reveal themselves to the internet via port forwarding. So, it seems there’s a subtlety at play here about how the first assault is completed. Anyway, yup, turn off UPnP unless you know you need it.
Igot good service from Meross -will likely go with them when I finally have had enough of Belkin's shenanigans.