Ransomware attackers are targeting US healthcare and education services
The USA is now seeing more ransomware attacks than the next 22 most-affected countries combined, according to a new report that expects the number of incidents to rise sharply.

Security research firm Malwarebytes has previously reported on the different approaches bad actors take to users of Macs compared to PCs. Now in its latest annual report, the writers say there were 1,462 reported ransomware attacks in the US alone.
"Over the last 12 months, education and healthcare were the most beleaguered sectors in the US outside of services," says Malwarebytes in its report. "They received so many attacks that if they were countries, they would be the fourth and sixth most attacked in the world, on either side of Germany."
The broad category of Services attracted 26% of all US ransomware attacks. Financial services was the lowest-specified category, being the target of 2% of US ransomware attacks in the year to July 2023.
"While the number of active groups in the US has increased over the last year," continues the report, "the escalation in the number of monthly attacks appears to be the result of existing ransomware groups being more active."
Malwarebytes further claims that there is evidence ransomware is growing, and specifically that it is increasing the use of ransomware-as-a-service (RaaS). An up-and-coming group, CL0P, is making waves with its ascension using RaaS, overtaking large groups like LockBit some months.
RaaS can be spread by various methods, but reportedly the most common one is that it is sent out by email.
"In March, CL0P used a zero-day vulnerability in the GoAnywhere MFT secure file transfer tool to break into numerous victims' networks, chalking up 48 known attacks-almost double LockBit's total," said Malwarebytes. "In late May, after two quiet months, CL0P returned, abusing a zero-day in Progress Software's file transfer tool MOVEit Transfer to compromise an even larger number of victims, again vastly exceeding LockBit's output that month."
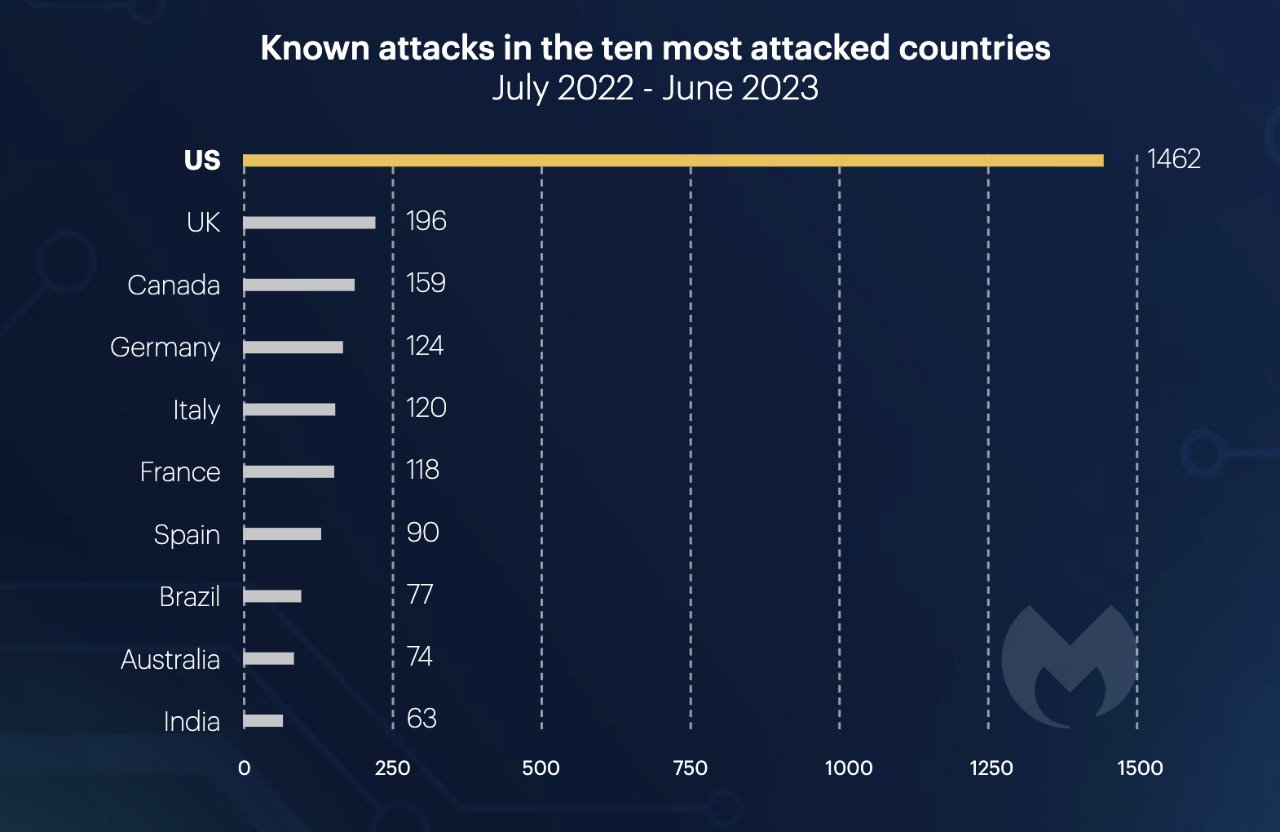
Top ten most ransomware attacked countries in the last year (Source: Malwarebytes)
"[However, from] CL0P's perspective the campaign has achieved mixed success," said Marcelo Rivero, Malwarebytes' threat intelligence analyst and ransomware specialist. "While it exploited a previously unknown vulnerability, the generally low quality of the data stolen may have compromised its objectives."
Viruses are still more prevalent on PCs, but Macs are an attractive target for criminals, so the use of malware that a user may be tricked into installing is growing. Most recently, in April 2023, the Windows LockBit ransomware software began targeting Macs for the first time.
The full report is available directly from Malwarebytes.
Read on AppleInsider

Comments
Ransomware would typically lock up your data and demand you pay to unlock it.
Now, it tries to skim data out of the system before locking it up and demands a fee for unlocking but with the extra leverage of 'if you don't pay, we will make your data 'public'.'
Tjis is what happened with Hospital Clinic in Barcelona, which refused to pay and is still recovering.
Yes, AI is already being used in attacks but AI is also being used in defence.
Also, a good back up strategy (and air gapped) is key.
New solutions are coming to market which allow the storage media system itself to 'detect' a potential ransomware attack as data is being written and react accordingly.
This is key for cloud based systems. 5G network slicing, containerisation, robust hypervisors, multi-cloud strategies etc also help to reduce propagation.
Unfortunately, major institutions have been shown to have failed in protecting their systems.
Protection is possible and recovery should be a viable option (with a good backup plan).