'Fake Airplane Mode' makes iPhone look offline to user, while an attacker stays connected
Security threats can crop up at any time, even on the iPhone, and now Jamf Threat Labs has demonstrated that even if you think Airplane Mode is on, you might be getting duped.

Jamf logo
At the time of publication, this particular attack has not been demonstrated in the real world. However, the mobile tampering technique is advanced enough that, in most scenarios for everyday users, it would go undetected.
Going undetected is the whole point of "Fake Airplane Mode," as detailed by Jami Threat Labs. The idea is that an attacker can make it look like a user's iPhone has Airplane Mode switched on, effectively disconnecting them from Wi-Fi and cellular networks.
In reality, though, this particular attack means that Airplane Mode is not switched on, even as it disconnects internet connectivity to everything except the attacker's specified app. This exploit makes it so the attacker can retain connection with the iPhone of choice, even though the user believes they are offline.
The whole process relies on both SpringBoard and CommCenter, with the former handling the UI elements and the latter handling network connectivity. At the same time, Jamf Threat Labs had to find a way to manipulate the pop-ups that normally notify the user what's happening on their device.
The UI elements here is what really sell the attack, with the attention to detail. Just like iOS is designed to do, after switching on Fake Airplane Mode the Cellular icon dims.
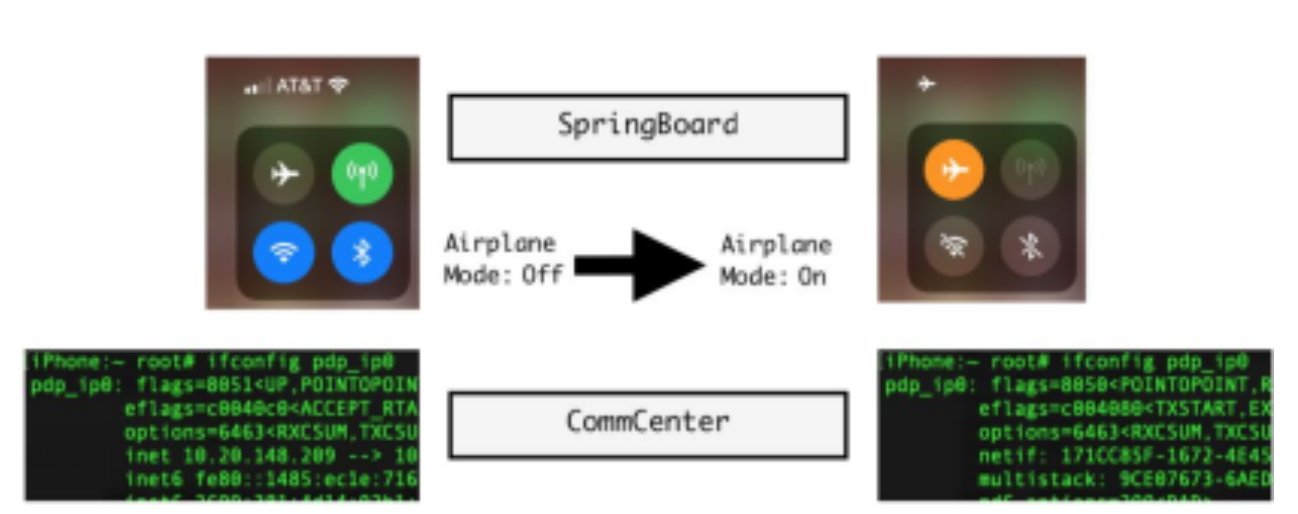
Making "Fake Airplane Mode" look real
The full report from Jamf Threat Labs details the code utilized to get from one step to the next, as far as the Fake Airplane Mode is concerned. But the research led by Hu Ke and Nir Avraham notes that the attacker needs to go through the series of exploits after they evade detection to begin with.
What's more, the paper does not outline how an attacker would go about enacting the exploits to begin with, whether the attacker can do so wirelessly or if they need physical access to the device they intend to attack.
The paper mainly outlines two very important elements: that it's relatively simple enough to not only spoof Airplane Mode at the system level, but to make it look like nothing is wrong at all on the UI level.
It's not clear if this has been reported to Apple.
How to stay safe
As mentioned above, it's not specifically outlined how an attacker might actually instigate the exploits required to initiate Fake Airplane Mode. With that being said, the general rules for keeping your data safe while out in the world remain true here.
Which means iPhone users should remain vigilant about the Wi-Fi hotspots they connect to, and should never let a stranger gain access to their device, especially for not any length of time.
On a related note, especially when it comes to pop-ups on an iPhone, a researcher walking the conference floor at Def Con 2023 showed how easy it is to utilize Bluetooth Low Energy to spoof an Apple device. Which can lead to an attacker prompting an iPhone owner to input their password when they least expect it.
Read on AppleInsider

Comments