Apple reinforces iMessage security with contact key verification
Apple enhances iMessage security with "Contact Key Verification," fortifying user privacy and identity verification against evolving threats using cryptographic methods and Key Transparency.
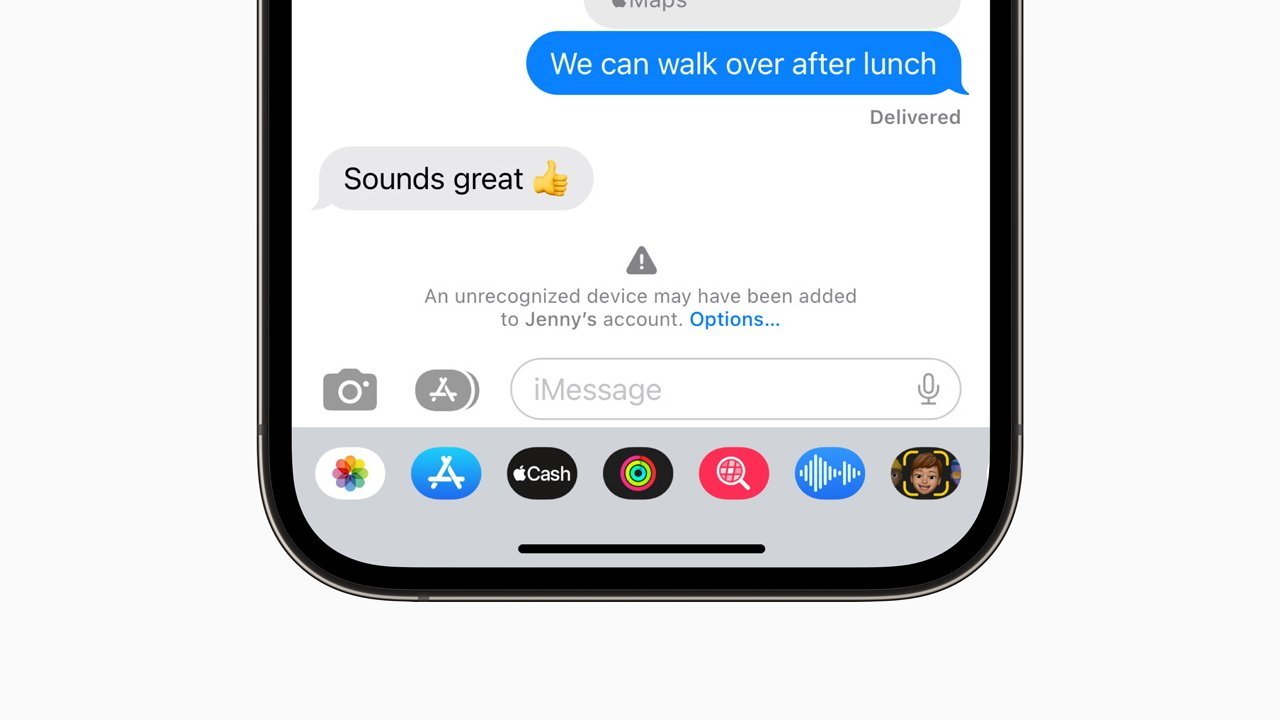
An example of an alert from iMessage Contact Key Verification
Contact Key Verification is a security feature that helps detect sophisticated attacks on iMessage servers and allows users to verify the identity of their communication partners. This feature specifically addresses the vulnerabilities that are associated with key directory services.
Such services usually map user identifiers to public keys, which could become a single point of failure if they get compromised. Contact Key Verification aims to overcome this issue by providing a more secure way of verifying the identities of communication partners.
To tackle this issue, Apple has introduced a mechanism known as Key Transparency (KT). Similar to Certificate Transparency, KT uses a verifiable log-backed map data structure that allows cryptographic proofs and audits for consistency over time, offering scalability and user privacy. Apple's implementation of Key Transparency goes beyond the existing key directory system.
It introduces an account-level ECDSA signing key, generated and stored on the user's device in iCloud Keychain. Devices use this synchronized account key to sign iMessage public keys, and this data is stored in the Identity Directory Service (IDS) database and synchronized with the Key Transparency service.
When users enable Contact Key Verification, their devices automatically and cryptographically verify the data presented by IDS against the KT map. If inconsistencies are detected, users are notified. Furthermore, users' own devices periodically verify the data to ensure consistency across all their devices.
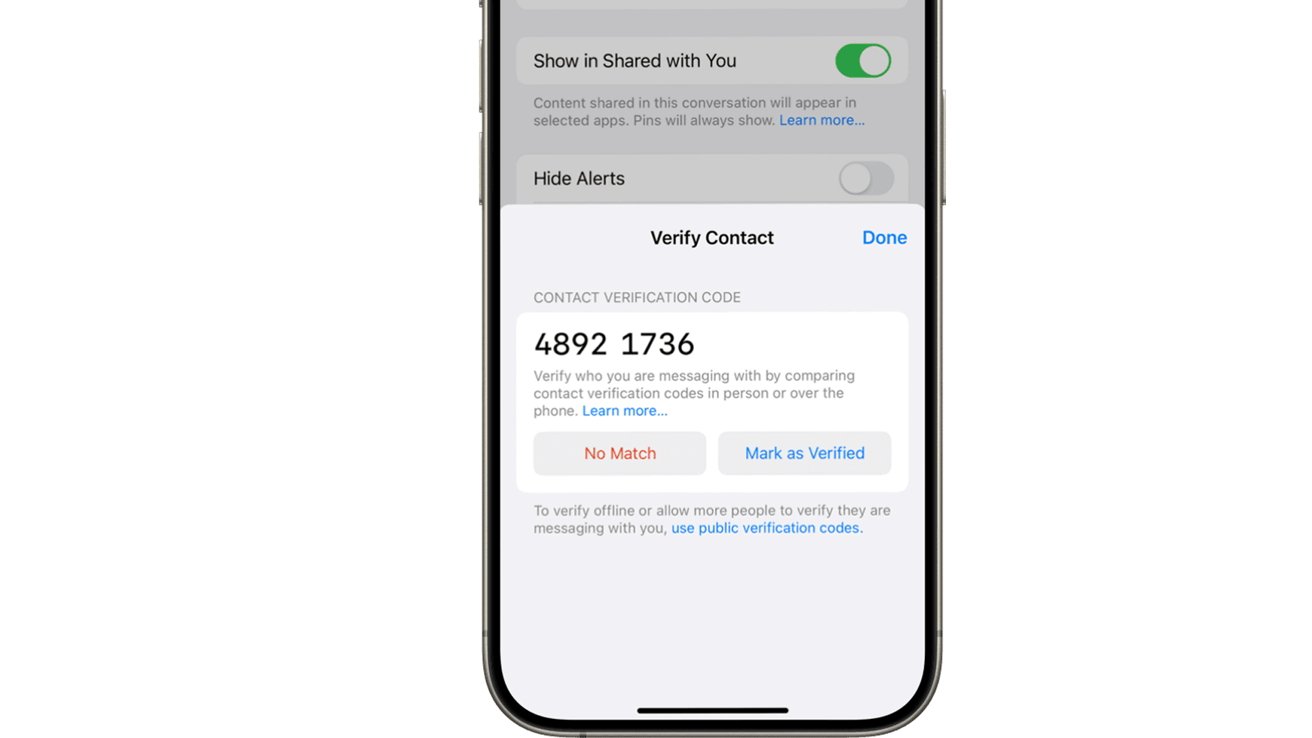
Apple has also incorporated a feature for manual contact verification using shortcodes, providing an additional layer of security for users who require it. This verification process extends to all users' devices, maintaining consistency when signing in on new devices.
In addition, Apple has introduced public verification codes for users with public personas, ensuring that their contact key is accurately verified.
Apple's implementation includes on-device verification of critical append-only logs for user control and security. The Messages app verifies log consistency, addressing potential compromise of the KT service.
Apple will launch Key Transparency, with internal auditing across production trees and more details to follow about public auditing. iMessage Contact Key Verification is available in developer previews of iOS 17.2, macOS 14.2, and watchOS 10.2, promising enhanced security for Apple's messaging platform.
Read on AppleInsider

Comments
In other words, the reason for this complexity is to prevent scumbags stealing our data. Does Apple really need to have more of a reason to implement better security?
You don't require it. Calm down.
EDIT: Here's one old article that explains it.
https://threatpost.com/apple-imessage-open-to-man-in-the-middle-spoofing-attacks/102610/
User: "Hey Apple, please make sure our iOS and macOS devices are rock-solid secure."
Apple: "We are always looking for ways to increase security in these fast-paced times, with new threats emerging all the time."
User: "Great! This is why I buy your products."
Apple: "We've introduced a new contact keys feature that will make messaging more secure."
User: "Great, but why all the complexity?"