Apple's private Wi-Fi MAC addresses were security theater until iOS 17.1
Apple introduced a feature that would hide a user's permanent MAC address in 2020, but it's been virtually useless until iOS 17.1 thanks to a now patched vulnerability.
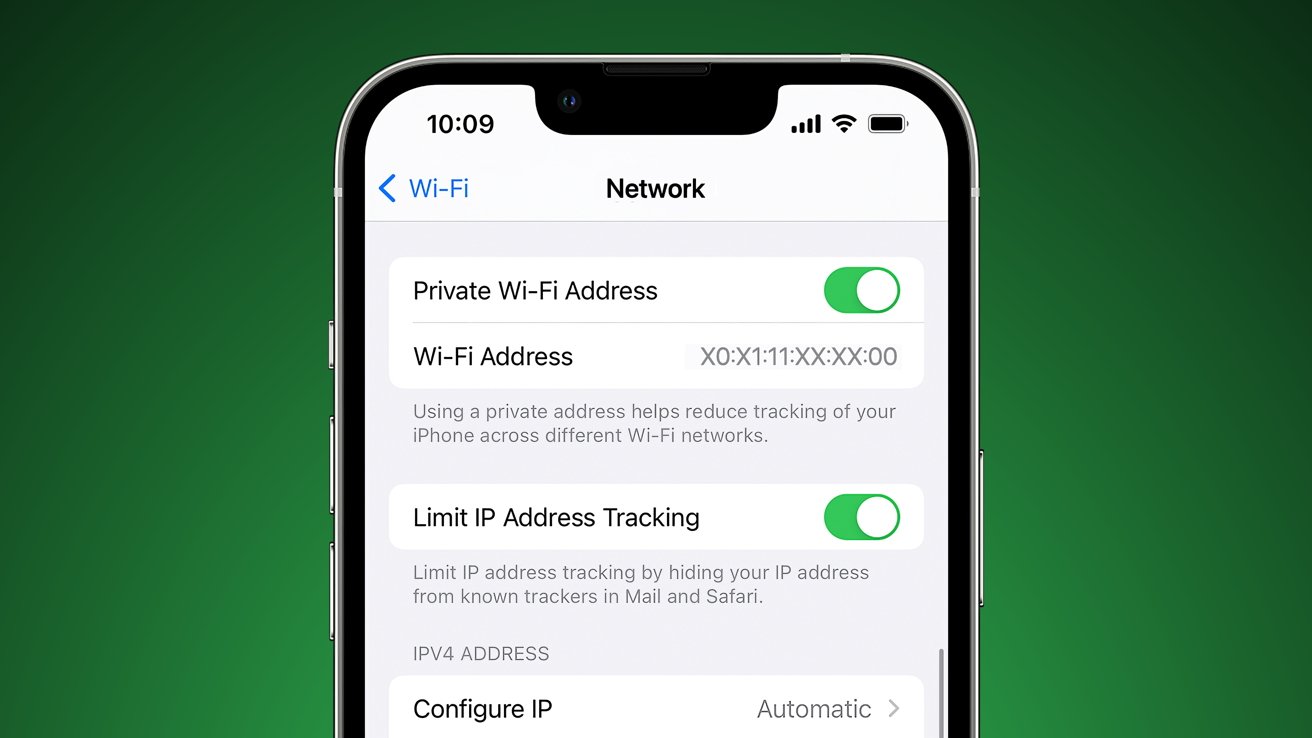
Private Wi-Fi address
When a device connects to a network, it performs a necessary handshake, sharing its unique MAC address. If an entity can access the MAC addresses accessing networks at a large enough scale, they could track users as they move between networks.
According to a report from Ars Technica, Apple implemented a feature that would prevent MAC address tracking, but a vulnerability has rendered it virtually useless since it debuted in iOS 14. The Private Wi-Fi Address feature is enabled by default and promises to assign a different MAC address to every unique SSID, which it did in practice.
The problem is the permanent MAC address that was supposedly being obfuscated by this feature was still being shared through port 5353/UDP. Basic MAC address sniffing was curtailed, but anyone looking could easily find the real MAC address, which presents a problem for those expecting this feature to work.
The report suggests that this would have been a simple fix, and it isn't clear why Apple took three years to implement it. General users don't need to worry about this vulnerability, but anyone who needed to hide their MAC address and expected the feature to work could have had their MAC address compromised.
Apple reports that the vulnerability has been patched in iOS 17.1. It was tracked as CVE02923-42846 and credited to Talal Haj Bakry and Tommy Mysk.
Read on AppleInsider

Comments
I'm glad it's fixed, but it looks like it wasn't general knowledge until CVE02923-42846 was published on the 25th.
It’s equally probable and I believe even more likely that this is simply a case of a pathetic level of security software implementation. The reason I say this is because the vast majority of Apple’s customers know little to nothing about this feature-fail and have no idea what a MAC address is, well, other than to think that a MAC address corresponds to the location of their closest McDonald’s restaurant. Plus, nobody was ever asked to remove their shoes.
Apple told us it’s safer to have it enabled, turns out a miscreant could get the actual Mac by probing a port on the device.
I’m a network engineer, have been for 23 years, when the manual says something specific you need to be able to trust it. Apple would have known about this “feature” I’m sure others that needed to know knew about this feature too.
the truth is you can’t trust anyone.
if available, it’s time to install a 3rd party firewall on your devices.
I do so love when people like you display your ignorance and condescension. It makes you sound so smart.
https://en.wikipedia.org/wiki/MAC_address
If I recall correctly, you may be able to determine from a given MAC address who manufactured the device (CISCO, HP, Apple), the device model number and even the serial number. It has been many years since I was looking into details. Details have likely evolved (it has been at least 7 years since I've spent time reviewing Media Access Control addresses).
Doubt that many Windows or macOS users look into this at great detail. Would be more of interest to networking specialists. Bet there are folks at NSA, CIA and FBI who are very interested in media access control addresses. Likely of great interest to other spy agencies domestic and foreign, as well as cyber criminals. Suspect you could spend a lifetime on detailed study (not my cup of tea).