'Operation Triangulation' exposes advanced iMessage attack on security firm
Security experts have disclosed an astonishing four-year campaign of iPhone hacking targeting the Russian security company Kaspersky, which has been labeled "the most sophisticated exploit ever."

Researchers uncover a sophisticated iPhone attack
Operation Triangulation's attack involved a complex series of exploits, including a zero-click iMessage attack, targeting iOS up to version 16.2. The attack began with a malicious iMessage attachment exploiting an undocumented TrueType font instruction, leading to remote code execution.
The exploit chain incorporated multiple techniques such as return/jump oriented programming, JavaScript obfuscation, and manipulation of JavaScriptCore and kernel memory, according to Kaspersky researcher Boris Larin.
Exploiting hidden hardware registers
A key part of the attack was using special hardware controls (MMIO registers) to get around Apple's Page Protection security layer. It was done through specific weaknesses, tracked as CVE-2023-41990, CVE-2023-32434, and CVE-2023-38606 in the database of security flaws.
By exploiting these flaws, the attackers could access all the memory of the iPhone and gain complete control to carry out further actions like sending recordings from the microphone, pictures, location information, and other confidential data to their servers.
One of these weaknesses, CVE-2023-38606, was especially tricky, letting attackers bypass extra security in newer iPhones. That was done by sending data to certain parts of the iPhone's memory using some hidden parts of Apple's chips, which were probably meant for checking and fixing problems.
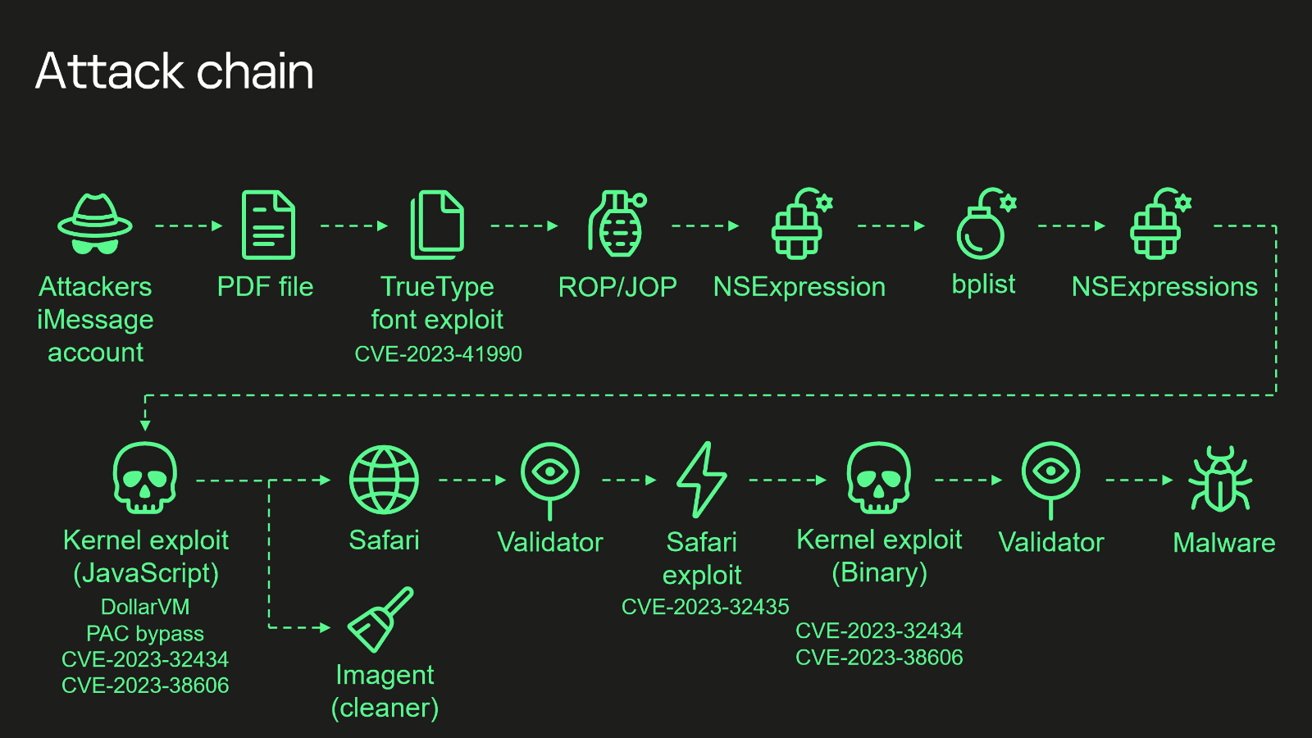
Diagram of the Triangulation exploit chain
The researchers found these hidden parts connected to the iPhone's graphics processor. When they tried to access them, it caused the graphics processor to crash, which showed they were a part of the attack.
One particular control, numbered 0x206040000, was vital because it was used at the start and end of the attack. That suggests it was used to turn on or off a unique hardware feature or to manage alerts during the attack.
Apple fixed the security problem by updating the device's internal map (known as the device tree) to recognize and control access to specific memory areas, specifically the ranges 0x206000000-0x206050000 and 0x206110000-0x206400000, which were being misused in the attack.
The device's system (XNU) uses this map to decide if it should allow access to certain parts of its memory. Each area in the map is clearly labeled to show what kind of memory it is and what it's used for.
Is it possible to stay safe from Triangulation?
Apple has already patched the combination of exploits used here.
While it's impossible to stay safe from a zero-day attack, iPhone users can still take several steps to mitigate the damage. However, in this case, it was a targeted munition, directly aimed at Kaspersky employees.
Regularly updating the iOS to the latest version is crucial, as it includes fixes for known security vulnerabilities. Users should exercise caution with messages, especially from unknown sources, avoiding clicking on suspicious links or downloading attachments.
Employing strong, unique passwords and enabling two-factor authentication for the Apple ID adds another layer of security. Next, regular backups of iPhone data can mitigate damage in case of an attack.
Finally, Apple added a feature called "Lockdown Mode" to iPhone, Mac, and iPad in iOS 16, macOS Ventura, and iPadOS 16. It's a security feature designed primarily for high-profile individuals who might be targets of sophisticated cyberattacks.
The feature isn't intended for everyday use due to its highly restrictive nature, significantly limiting device functionality.
Read on AppleInsider

Comments
So that remains the big question:
How did the attacker become aware of that piece of hidden hardware, something only a very select number of Apple employees or perhaps the chip manufacturer should have been known existed? I can understand the Russians pointing fingers at Apple as being in cahoots, but there's no evidence at the moment Apple was aware the hidden hardware had been exploited, much less advised any governmental agency about how it might be used for spy games.
Oh well dear hearts Happy New Year ( and if drinking or otherwise self medicating ) pass the keys to someone SOBER please !!!
Possible it could be one of the tools sold on dark web or by a group indirectly related to 2600 hacking group. Doubt this was the work of an individual hacker. Although it may be easier than I'd imagine to develop (unsure what type of tools may exist to decompile executable code back to source code). Assume that iOS would be compiled to machine readable code for performance (not interpreted). I'd expect AI to be used in newer malware soon (if not already used), leading to a large uptick in malware and viruses.
Seem to be more zero-click exploits recently. In the past, we could largely protect ourselves by only clicking on links from known sources. Interesting that a security related firm's employees appear to have been the main target. Also interesting that the exploit started four years ago. Maybe attempt was to determine corporate plans of Kaspersky to develop competitive products, or access data concerning customers?
This hardware angle to the story was discovered several months ago, and the fact that Apple has been silent about it since (AFAICT) may indicate the answer isn't so easy.