Google Ads used to distribute Mac malware disguised as 'Loom' app
Experts recently discovered a macOS stealer malware disguised as the popular screen recording app Loom, spread through deceptive Google-sponsored URLs.

Crazy Evil malware
Moonlock Lab found a sophisticated macOS stealer malware disguised as Loom, orchestrated by the notorious Crazy Evil group. It uses deceptive Google-sponsored URLs to trick users into downloading harmful software.
The investigation began when Moonlock Lab identified a Google ad promoting the official Loom app. The ad seemed legitimate and enticed users to click on a trusted source.
However, clicking the link redirected users to a site nearly identical to the official Loom website, hosted at smokecoffeeshop[.]com. Users were prompted to download what they believed was Loom, a malicious file containing stealer malware.
The campaign was not limited to Loom. The attackers had also created fake versions of other popular applications, including Figma, TunnelBlick (VPN), Callzy, and a suspiciously named file, BlackDesertPersonalContractforYouTubepartners[.]dmg.
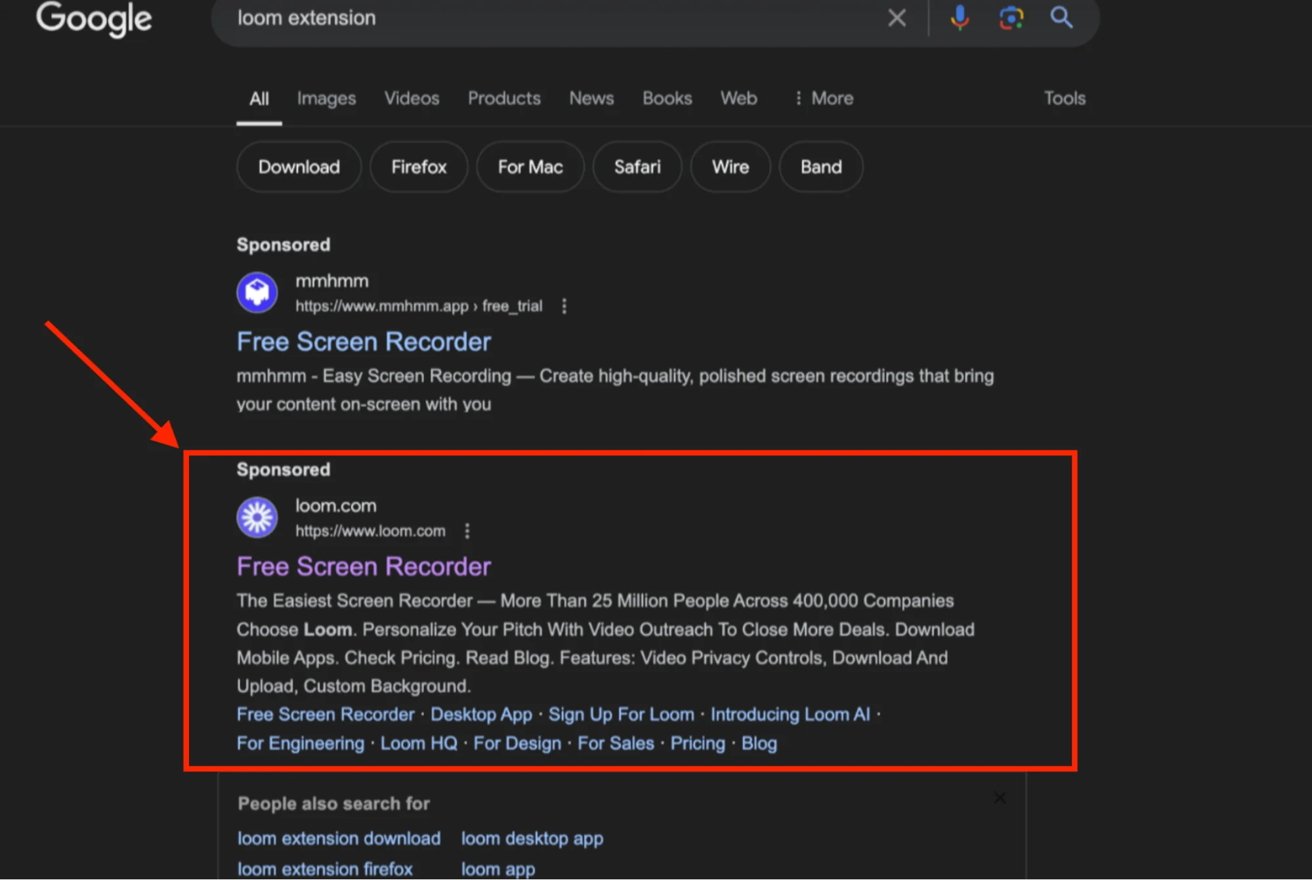
A deceptive Google sponsored link
The last example suggests a phishing campaign targeting YouTube content creators, a tactic previously used against Windows users but now repurposed for macOS.
Similar phishing emails were sent to Windows users in 2022. Mac users face the same threats, with attackers exploiting the relationship between gaming companies and content creators. They lure bloggers and content creators with promises of lucrative contracts to promote games like Black Desert Online on their channels.
A malicious LedgerLive clone
An aspect of the campaign involves using a stealer that replaces the legitimate LedgerLive app with a malicious clone. LedgerLive is widely used by cryptocurrency holders, making it a target for cybercriminals.
Attackers can access and drain victims' cryptocurrency wallets by replacing the genuine app with a harmful version. The malicious clone mimics the legitimate app's appearance and functionality, making it difficult for users to detect the compromise.
Moonlock Lab's investigation found strings containing "Ledger" in the infected files, confirming the malicious intent towards users' cryptocurrency assets. The stealer, identified as a variant of AMOS, retains key features like grabbing files, hardware information, passwords, data from browsers, and keychain dump credentials.
Darknet recruitment and attribution
Darknet recruitment ads posted by Crazy Evil seek individuals to join a team using this variant of macOS stealer. The recruitment announcement details benefits like reliable protection and exploiting various formats for different victims.
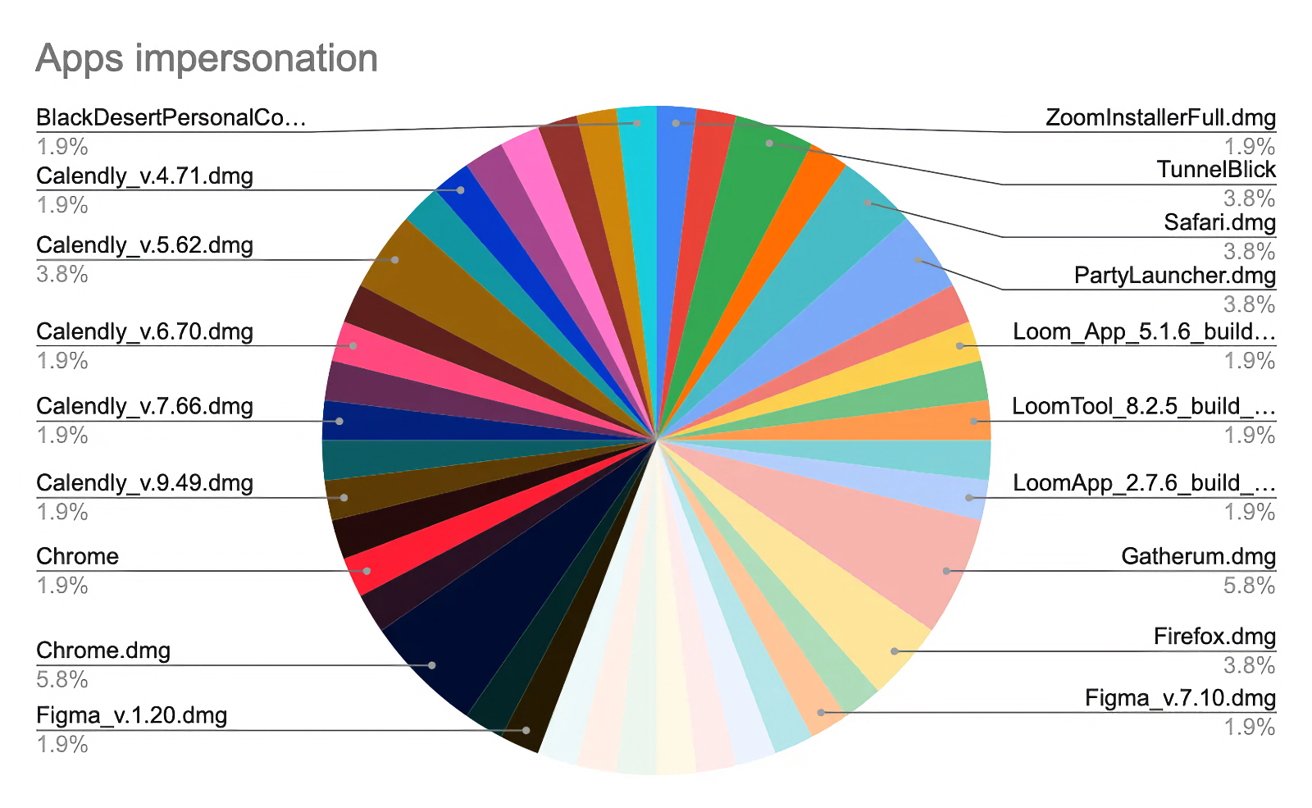
The extent of the campaign
Interestingly, Moonlock Lab identified an IP address linked to a governmental entity with high malware association and 93 files marked as malware. The IP address hosted macOS-related files from the campaign starting July 23, 2024.
How Mac users can stay safe
Mac users can protect themselves by taking proactive measures. Always double-check URLs when downloading files, even from trusted sources like Google Ads or top search results.
Regularly scan your device with reliable anti-malware tools like CleanMyMac X with Moonlock Engine to ensure no malicious software is present. Keep software up-to-date to protect against known vulnerabilities.
Finally, be cautious with emails offering contracts or deals from unknown senders to prevent phishing schemes. The Mac's built-in security features, Gatekeeper and XProtect, provide extra protection against malicious software and are enabled by default.
Read on AppleInsider

Comments
Edit: you don't even need to click the malicious ad. Just the display of it may trigger the automatic download.