Evolved and more powerful macOS malware strain sold cheaply to criminals
Researchers have discovered another data-seizing macOS malware, with "Cthulhu Stealer" sold to online criminals for just $500 a month.
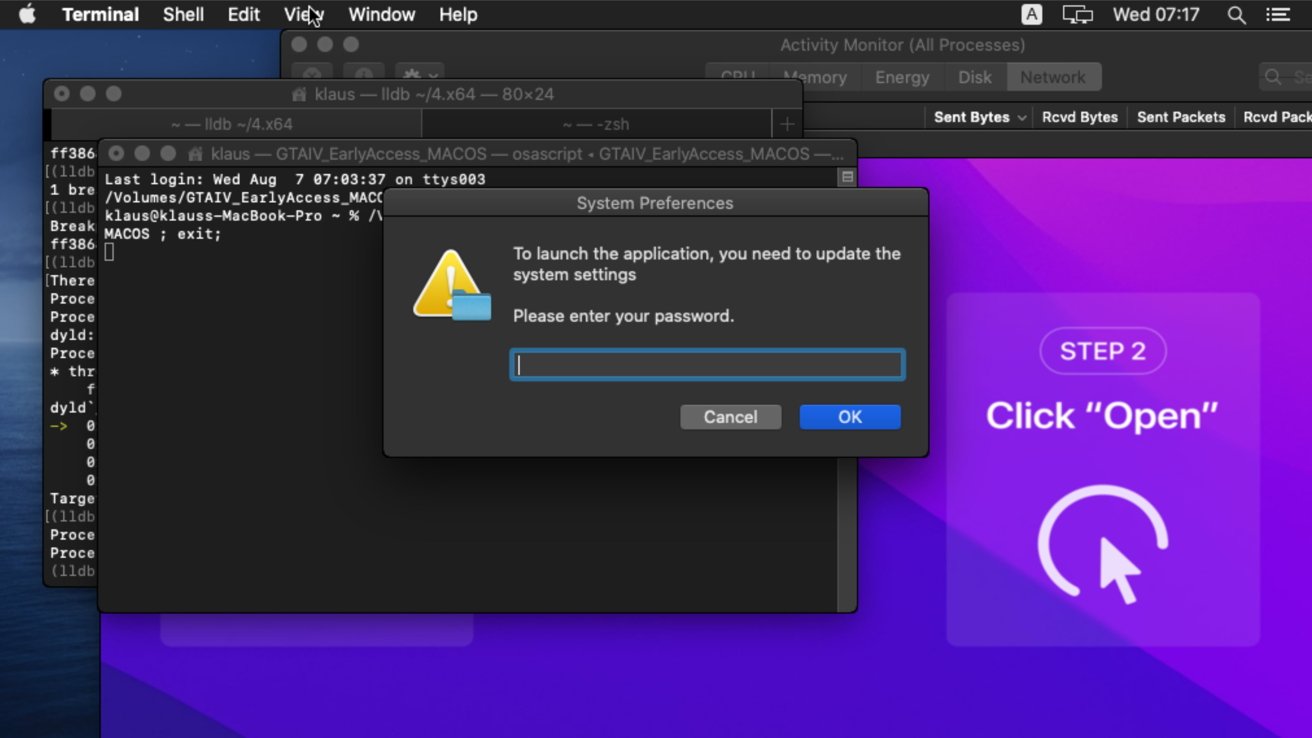
Cthulhu Stealer in action [Cado Security]
The Mac is becoming even more of a target for malware, with warnings surfacing from researchers surfacing on a regular basis. In the latest example, it's for malware that's been in circulation for quite a few months.
Explained by Cato Security and reported by Hacker News on Friday, the malware referred to as "Cthulu Stealer" has apparently been around since late 2023. Consisting of "Malware-as-a-Service," it was able to be used by online criminals for a mere $500 per month.
Bad disk images
The malware takes the form of an Apple disk image that contains a pair of binaries. This allowed it to attack both Intel and Apple Silicon Macs, depending on the detected architecture.
To try and entice consumers to open it, the malware would be disguised as other software, including Grand Theft Auto IV and CleanMyMac. It also appeared as Adobe GenP, a tool for patching Adobe apps so that they don't rely on receiving a paid security key from the Creative Cloud.
The supposed contents was a ploy to convince users to launch the unsigned file and allowing it to run after bypassing Gatekeeper. The users are then asked to enter their system password, followed by a password for the MetaMask cryptocurrency wallet.
With those passwords in place, system information and iCloud Keychain passwords are stolen, along with web browser cookies and Telegram account details. They are sent off to a control server.
"The main functionality of Cthulhu Stealer is to steal credentials and cryptocurrency wallets from various stores, including game accounts," said Cato Security researcher Tara Gould.
Borrowing code
Analysis of the malware indicates that the malware is similar to another that was previously found by the name of "Atomic Stealer."
It is thought that whomever made Cthulu Stealer used the code that produced Atomic Stealer as a base. Aside from functionality, the main evidence of this is an OSA script that prompts for the user's password, which has the same spelling mistakes.
Unusually for discovered malware, it appears that the creators of Cthulhu Stealer aren't able to manage it, due to payment disputes. The developer behind it was permanently banned from a cybercrime marketplace that advertised the tool over accusations of an exit scam that affected other marketplace users.
Protecting yourself
Users don't have to do that much to protect themselves from Cthulhu Stealer, not least because of ownership control issues.
As usual, the advice is to be vigilant about what apps you download, that you download from safe sources, and to pay attention to what the app does as you install it.
As for overriding Gatekeeper, this is something that can be accomplished easily in macOS Sonoma and earlier releases. For macOS Sequoia, users cannot Control-click to override Gatekeeper, but will need to visit System Settings then Privacy & Security to review a software's security information instead.
This change should reduce the number of instances where Gatekeeper is bypassed, simply by adding more obstacles.
Even so, users should still pay attention whenever Gatekeeper raises an objection to installing or running an app.
Read on AppleInsider

Comments