Now patched macOS Calendar exploit let hackers steal data from iCloud
A security researcher has detailed an old hack in macOS that gave hackers full access to a user's iCloud, needing only a calendar invite to succeed.

Even Apple's Calendar app can be vulnerable
In 2022, security researcher Mikko Kenttala discovered a zero-click vulnerability within macOS Calendar that could allow attackers to add or delete files in the Calendar sandbox environment. The vulnerability allowed attackers to execute malicious code and access sensitive data stored on the victim's device, including iCloud Photos.
The exploit starts with the attacker sending a calendar invite containing a malicious file attachment. The filename isn't properly sanitized, which allows the attacker to perform a "directory traversal" attack, meaning they can manipulate the file's path and place it in unintended locations.
The vulnerability (CVE-2022-46723) lets attackers overwrite or delete files within the Calendar app's filesystem. For example, if the attacker sends a file named "FILENAME=../../../malicious_file.txt," it will be placed outside its intended directory in a more dangerous location in the user's filesystem.
Attackers could further escalate the attack by using the arbitrary file write vulnerability. They could inject malicious calendar files designed to execute code when macOS is upgraded, particularly from Monterey to Ventura.
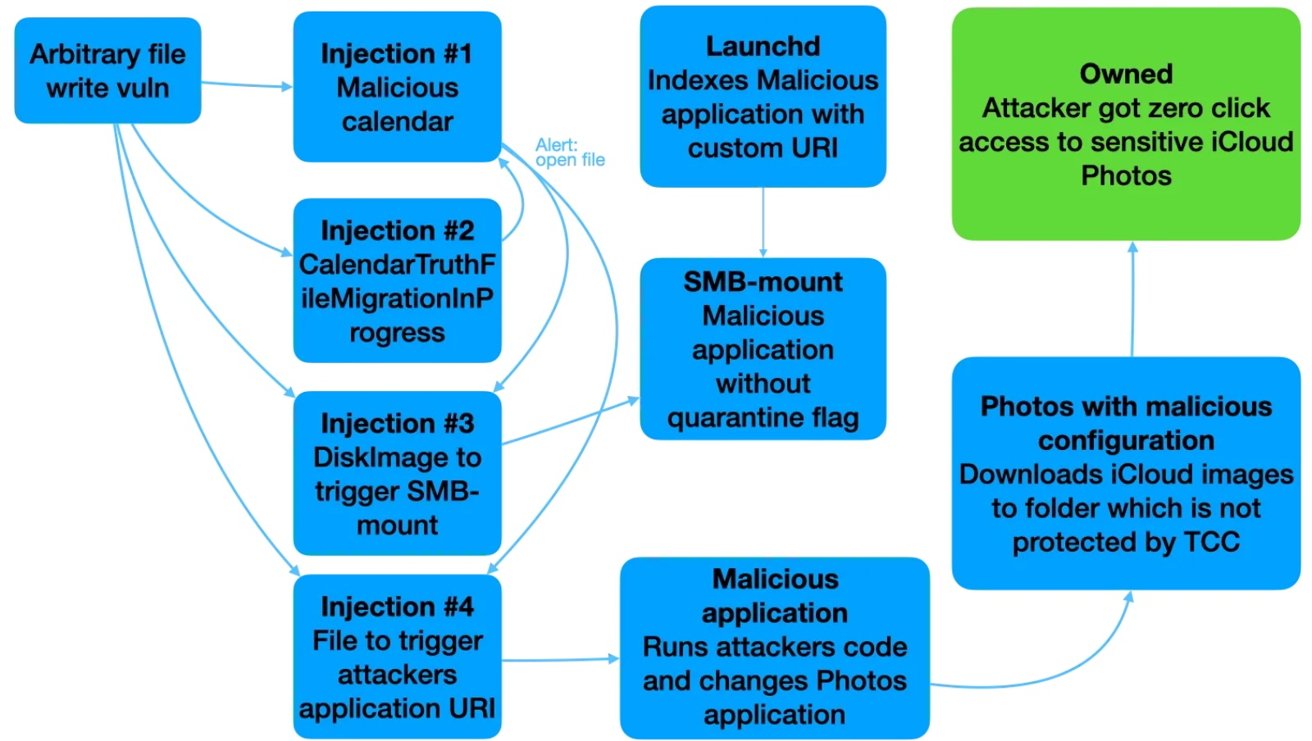
The full exploit chain
These files included events with alert functionalities that triggered when the system processed calendar data. Injected files would contain code to automatically launch files like .dmg images and .url shortcuts, eventually leading to remote code execution (RCE).
Eventually, the attacker could completely take over the Mac without the user's knowledge or interaction.
Fortunately, the hack isn't new. Apple patched it over several updates from October 2022 to September 2023. These fixes involved tightening file permissions within the Calendar app and adding additional security layers to prevent the directory traversal exploit.
How to stay safe from zero-click attacks
To stay safe from zero-click vulnerabilities like the one discovered in macOS Calendar, it's crucial to follow a few protective measures. First and foremost, always keep your software up to date.
Apple frequently releases patches that address security flaws, and enabling automatic updates ensures you'll get critical fixes. Finally, strengthen your device's security settings by restricting apps' access to sensitive data, such as your calendar, photos, and files.
Read on AppleInsider

Comments
Variation on hidden malicious code in graphical files (some years ago on both Windows and macOS). Here, malicious code is contained in calendar data that is executed when adding invite to your calendar. The malicious code may setup a future exploit, then be executed at a future time (during an OS update). If you build a better mouse trap, bad actors will build a better mouse. Suspect multiple other possible exploits using code injection and variations of this method.
Probably safe to add invite if you know the sender. UNLESS the sender received the invite from a questionable source or someone falsely claiming to be a trusted source, such as your bank or an executive at your employer. Basically, could be a social engineering attack.