Leak: what law enforcement can unlock with the 'Graykey' iPhone hacking tool
Leaked documents reveal the secrets behind Graykey, the covert forensic tool used to unlock modern smartphones, exposing its struggles with Apple's latest iOS updates.

iPhone 15
Graykey is a forensic tool designed to unlock mobile devices and extract data, primarily used by law enforcement agencies and digital forensics experts. Developed by the secretive company Grayshift -- now owned by Magnet Forensics -- Graykey has earned a reputation for its ability to bypass smartphone security measures.
The tool helps law enforcement and forensic professionals in accessing locked mobile devices during criminal investigations. It breaks device encryption and security features to retrieve personal data like messages, photos, app data, and metadata.
Graykey supports Apple and Android devices, though its effectiveness varies depending on the specific hardware and software involved. Graykey's capabilities and limitations, however, are rarely disclosed.
However, a leak of some Grayshift's internal documents was recently reported on by 404 Media. According to the data, Graykey can only perform "partial" data retrieval from iPhones running iOS 18 and iOS 18.0.1.
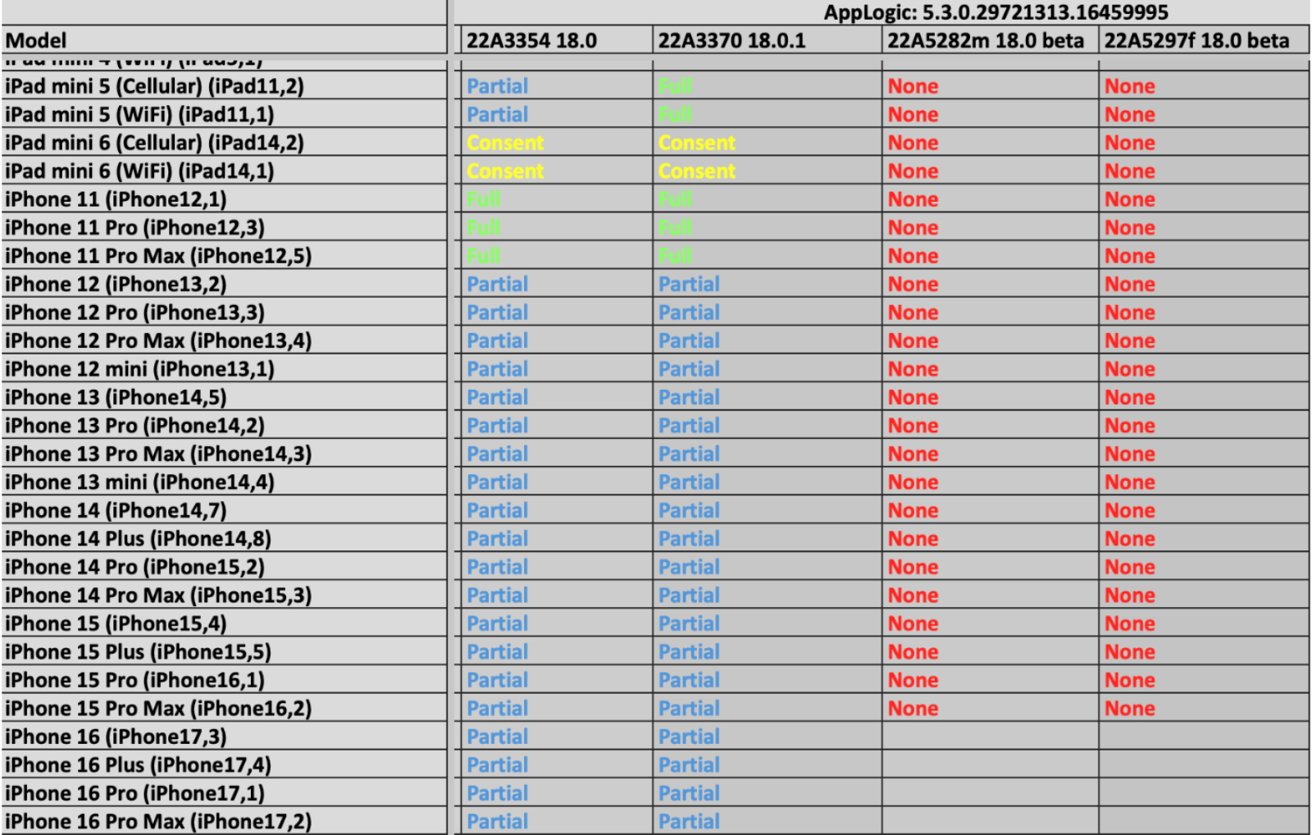
An image of a document detailing Graykey's functionality with iPhones operating on iOS 18.0 and 18.0.1. Image credit: 404 Media
These versions were released in September and early October, respectively. A partial extraction likely includes unencrypted files and metadata, such as folder structures and file sizes, according to past reports.
Notably, Graykey struggles with beta versions of iOS 18.1. Under the latest update, the tool fails to extract any data, as per the documents.
Meanwhile, Graykey's performance with Android phones varies, largely due to the diversity of devices and manufacturers. On Google's Pixel lineup, Graykey can only partially access data from the latest Pixel 9 when in an "After First Unlock" (AFU) state -- where the phone has been unlocked at least once since being powered on.
Andrew Garrett, CEO of Garrett Discovery, confirmed that the leaked documents align with Graykey's known capabilities. Meanwhile, Magnet Forensics and Apple declined to comment on the leak.
Cat and mouse game
The leaked documents shed light on the ongoing battle between tech companies like Apple and forensic firms. Apple's frequent security updates and features, including USB Restricted Mode and iPhone rebooting after inactivity, have made unauthorized access increasingly difficult.
In response, companies like Grayshift and Cellebrite continue to develop new exploits to bypass these safeguards. While tools like Graykey may lag behind new OS releases, historical trends suggest they often catch up eventually.
Forensic experts expect the cycle of vulnerabilities and patches to persist as Apple and Google continue fortifying their systems against unauthorized access.
Read on AppleInsider

Comments
Trump doesn't have the constitutional authority to create any law. Maybe you know that, but the way you worded it sounded like he has some degree of law-making authority.
yes about your trump statement, but unlike other presidents, no one says no to him. no republican senator or member of the house dares say no to him. or he will get negative tweets that night around 2-3am from trump. and he'll get a moderately funny schoolkid nickname.
he has close to absolute power
presidency
senate
house
and supreme court
Second, back doors are always bad. Trying to restrict them to just this or that group is a minefield that is doomed to failure. Security for the law abiding will be compromised, police and security will abuse the power, the keys to the ‘secret’ opening will get into the hands of criminals. That is an absolute gold plated certainty. Meanwhile groups like Hamas will just use alternative software options and systems to render their communications immune to spying and the back door. So no, any back door is a bad idea.
The iPhone gets a lot of security from the fact that the hardware/software architecture is designed to not allow backdoors. If you change the underlying architecture to allow backdoors, then American phones will essentially have backdoors, we will just have to live with the promise that they won't be opened.
We know from experience, that US law allows the government to obtain search warrants without the subject knowing he is being surveilled. We also know that Apple is a US based company and subject to US law. Should Apple be presented with such a warrant they would be obligated to open the backdoor.
Thus, in practice, you can't have backdoors that apply only to non-US phones.
Now whether or not you think that Apple's level of privacy is a good or bad thing, is a different topic.
This is why the Israeli government is using exploding pagers to attack Hezbollah and civilians in Lebanon.
While presidents currently do not have the constitutional authority to create laws, a large part of the platform that he campaigned on is consolidating powers into the executive branch. All he would need to enact those changes is a supportive house, senate, and judiciary… and a removal of the filibuster.
Let me give an example of the police searching soemone's home with a warrant. Armed with the warrant, the police can show up at someone's home and search it. The homeowner can't resist or obstruct the police in performance of their duties. If the door is locked, the police will ask the homeowner to open the door or the police will break down the door. But if the police can't break down the door, the homeowner can't be held criminally liable.
If there is a back door, then the police are able to open the phone and get the data.
Whether or not this is a good thing is a separate issue.
But even though cloud data can be unlocked with a warrant, that does not mean that data protections are completely useless.
For instance, suppose your phone is stolen. A hacker is unlikely to be able to obtain a warrant to compel Apple to unlock the phone. However, a hacker might be able to access the "back door" in order to get at your data. Depending on what you have on your phone, that might give the hacker access to bank accounts, investment accounts, etc.
I have a lock on the front door to my house. Someone who knows how to pick locks likely can get through the lock in under a minute. This doesn't mean I shouldn't bother with a lock. The fact that it is possible to bypass protection doesn't make the protection useless. It limits the number of actors who can gain access, and it can slow down access for those who can ultimately bypass the protection.
But even if people have full access, one can always obfuscate the nature of communications by using code words. An easy thing is to use private nick names for people / events, and euphemisms for actions. Sending "Peter is taking Sally to the club" could mean that a hitman has been hired to eliminate a senator, or that the sender is planning to have sex with his wife.
To clear things up an executive order is issued by the president to set policy for things within control of the executive branch. An executive order is not a law, it has the “force of law” when there is no existing law or to further clarification of an existing law, because congress did not account for every aspect of the law. A law is something that is passed by both houses of congress and signed into law by the president.
As for the political realities that an adjudicated sexual assailant, who pals around with dictators, war criminals, pedophiles, sex traffickers, murders, fraudsters, and neo-nazis is in a unique position as an incoming president. Members of his party in the house and senate are publicly threatening other members in their own caucus to push through anything he wants any way possible. He personally nominated 3 Supreme Court justices and has at least 2 other justices that have been wrapped in controversy, and have a history of right wing activism on and off the bench.
One issue is that many people are worried that the judicial branch (including the Supreme Court) has more loyalty to Trump than they do the country/Constitution. There have certainly been some recent rulings that are pro-Trump, and contrary to well established historical precedent.
Similarly, Trump seems to have that same level of loyalty from the Republican party, which controls the House and Senate. This combination appears to short circuit the checks and balances that we would get from three branches independent of government.
If these fears are correct, then Trump can issue whatever executive orders he likes. If Congress doesn't object and the courts allow it, then it really doesn't matter what the law says.
It is clear that many people share this sort of fear. As to whether or not the fears are justified, that's another matter entirely.
Even if Trump is able to use executive orders in this fashion, many are OK with this, as they expect to agree with whatever orders he issues. Others prefer a system of checks and balances, even if that results in blocking some rules they would like to see.