Apple seeks to simplify two-step verifications with standard SMS format
Apple's WebKit engineers are working on a standardized format for SMS messages containing one-time passcodes, an initiative that could one day better protect users by streamlining two-step authentication logins.
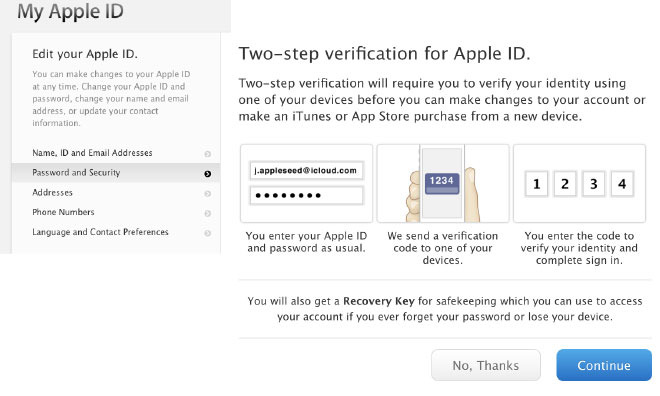
Apple previously relied on two-step verification for Apple ID.
Posted to GitHub on Thursday, the proposal from Apple seeks to simplify the OTP SMS mechanism commonly used by websites, businesses and other entities to confirm login credentials as part of two-step authentication systems, reports ZDNet.
Two-step solutions require a user's password and another element, in this case a one-time code sent over SMS, to gain access to a target account. Currently, it is difficult to impossible for software to automatically extract the necessary information from an OTP SMS message, as they can arrive in a range of text formats. This means users must manually enter the provided code into an input box.
Apple's proposal seeks to eliminate user intervention in the OTP SMS process, namely copy-and-pasting one-time codes from messages into a browser. It also states that a more refined solution would ensure that one-time codes sent over SMS are used only on originating sites.
Using a "lightweight text format," the proposed format embeds an actionable one-time code in an SMS message and links that code to a particular originating URL. Doing so allows recipient systems to automatically extract the code and log in to an associated website.
Apple provides an example SMS:
Apple and Google have signed on to the proposal, while Mozilla has not made an official statement on the standard, the report said.
For its part, Apple has moved its products from two-step verification to more secure two-factor authentication methods that rely on passcodes sent to pre-enrolled trusted devices.

Apple previously relied on two-step verification for Apple ID.
Posted to GitHub on Thursday, the proposal from Apple seeks to simplify the OTP SMS mechanism commonly used by websites, businesses and other entities to confirm login credentials as part of two-step authentication systems, reports ZDNet.
Two-step solutions require a user's password and another element, in this case a one-time code sent over SMS, to gain access to a target account. Currently, it is difficult to impossible for software to automatically extract the necessary information from an OTP SMS message, as they can arrive in a range of text formats. This means users must manually enter the provided code into an input box.
Apple's proposal seeks to eliminate user intervention in the OTP SMS process, namely copy-and-pasting one-time codes from messages into a browser. It also states that a more refined solution would ensure that one-time codes sent over SMS are used only on originating sites.
Using a "lightweight text format," the proposed format embeds an actionable one-time code in an SMS message and links that code to a particular originating URL. Doing so allows recipient systems to automatically extract the code and log in to an associated website.
Apple provides an example SMS:
The first line in the message above is optional human-readable text to explain the incoming message, while the second line contains information for programmatic use. Special characters are employed to denote the one-time code and originating URL, which in this case is "747723" and "website.com," respectively.
Apple and Google have signed on to the proposal, while Mozilla has not made an official statement on the standard, the report said.
For its part, Apple has moved its products from two-step verification to more secure two-factor authentication methods that rely on passcodes sent to pre-enrolled trusted devices.

Comments
I'm not so sure about Apple re-enforcing SMS as a multi-factor standard, though. SIM-jacking is real, the security standards of AT&T Verizon and Tmobile are laughable.
Yes
Oh god
Yes
For most people 2FA is a significant upgrade because they frequently reuse passwords, parts of passwords, or use things like birthdays in their passwords. Even if it’s on the same device it’s an improvement. If a website login is being accessed from an Apple iPad (for example) you’d need your biometric to auto fill the credentials from keychain then OTP SMS.
You're correct though SMS isn’t the best, a hardware key would be better, but it’s more complicated for the end user to use.
This I don't understand. I love how my password manager handles OTP.
I can't imagine an easier system. As for a password not working when you log in a month later I also log out and then log back in to make sure the saved password will work again. Sometimes, websites will truncate a long password you've created so something shorter when somewhere between the time you hit submit and it gets to the database to be saved. This will usually happen on websites that list a minimum length but not a maximum length so you could think that 16 characters is perfectly reasonable but their system only allows for 15 characters. They oddly don't look at this when you create the password, but will reject you when you submit as a login. if you know this going in and you're sure it's "correct" because you just created it you can retry your login by removing a character off the end until it works, and then save the truncated password.
I don't know if there is a potential bug with Safari's password manager as I don't use it. It's never been robust enough for my needs. My secret questions have characters letters for answers, I put all sorts of website and app specific info in each login file, and even my emails for accounts can vary and will often have aliases to make the potential for cross hacking as seen with accounts found on dark web websites. (e.g. For AppleInsider I might use soli+ random112358@mac.com as my login email but for World Bank I might use soli+random132134@mac.com so that even the username isn't able to knock on the door of my account).
I don't think I fully understand your use case either. The only time I get a message from Apple on all my connected devices is when I sign on to iCloud; that's when it let's all my connected devices know that I've added a new device. When it comes to 2FA for logins it's usually an OTP from my password manager (which 1Password does so well that you just have to have hit paste as it saves it to the clipboard for 60 seconds) or an SMS or email if the system doesn't support saving the OTP link.
That is true -- and an excellent point.
It's an argument for having passcode on the phone with the 10 try limit, always keeping track of it and putting it into lost mode the moment you don't know where it it.