Two Apple Mail vulnerabilities being used to target iPhone, iPad users
Security researchers have discovered a pair of zero-day vulnerabilities in the Mail app for iPhone and iPad that they have found in the wild, and being used by attackers.

Researchers have found two zero-day vulnerabilities in Mail that were actively used to attack users. Credit: ZecOps
San Francisco-based cybersecurity firm ZecOps said that they came across the two flaws in the default iOS and iPadOS Mail app while running routine digital forensics on customer devices. After further investigation, they found evidence of targeted attacks, which they outlined in a report on Wednesday.
The vulnerabilities allow an attacker to run remote code by exploiting Apple's MobileMail and Mailid processes in iOS 12 and iOS 13, respectively, through the use of a specially crafted email. And, if triggered properly, a user wouldn't know that they were being hacked.
Variants of the flaw stretch back to at least iOS 6, the researchers said. Because the vulnerabilities were used to attack users before Apple could issue a patch, they're considered zero-day attacks, which is significant because iOS zero-days are extremely rare and often quite expensive.
By themselves, the flaws don't pose too much of a risk to users -- they only allow an attacker to leak, modify or delete emails. But combined with another kernel attack, such as the unpatchable Checkm8 exploit, the vulnerabilities could allow a bad actor root access to a specifically targeted device.
At least one of the flaws can be triggered remotely without any user interaction -- an attack known as a "zero-click." ZecOps added that the second vulnerability was likely discovered by accident while attempting to leverage the zero-click. The vulnerability impacting iOS 13 is the zero-click. While the iOS 12 flaw does require users to actually tap on an email, that requirement doesn't apply to attackers who send messages from a mail server that they control.
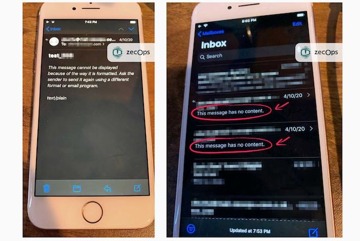
An example of a failed attack. Succesful ones wouldn't show an error message. Credit: ZecOps
In its report, ZecOps found that a number of its customers were targeted, including employees at a Fortune 500 company in North America, a journalist in Europe and a VIP in Germany. Interestingly, while there was evidence that the flaws were executed on targeted devices, the emails themselves weren't present. That suggests that the attackers deleted the emails to cover their tracks.
The researchers believe that the attackers were working for a nation-state that had purchased the attacks from a third party, adding that at least one "hacker-for-hire" organization was selling exploits that use email as the main vector.
On the other hand, security researchers who spoke to Motherboard said that the flaw was relatively unpolished compared to other hacks, meaning that sophisticated attackers would probably deem it too risky to use against "high value targets."
Still, ZecOps notes that attacks using the exploits are likely to increase in frequency since they're now publicly disclosed. The researchers said bad actors will "attack as many devices as possible," meaning that normal users could end up targeted. That becomes more dangerous if the exploits were leveraged by cybercriminals with access to additional vulnerabilities.
The vulnerabilities only impact the native Mail application, and not third-party apps. To mitigate the attacks, ZecOps recommends that users stop using Mail on iOS and iPadOS until a patch is issued. MacOS is unaffected.
ZecOps said it alerted Apple to the vulnerabilities in February. Both of the flaws have since been patched in the latest beta releases of iOS 13, and a fix is set to arrive in the next publicly available iOS update in iOS and iPadOS 13.4.5

Researchers have found two zero-day vulnerabilities in Mail that were actively used to attack users. Credit: ZecOps
San Francisco-based cybersecurity firm ZecOps said that they came across the two flaws in the default iOS and iPadOS Mail app while running routine digital forensics on customer devices. After further investigation, they found evidence of targeted attacks, which they outlined in a report on Wednesday.
The vulnerabilities allow an attacker to run remote code by exploiting Apple's MobileMail and Mailid processes in iOS 12 and iOS 13, respectively, through the use of a specially crafted email. And, if triggered properly, a user wouldn't know that they were being hacked.
Variants of the flaw stretch back to at least iOS 6, the researchers said. Because the vulnerabilities were used to attack users before Apple could issue a patch, they're considered zero-day attacks, which is significant because iOS zero-days are extremely rare and often quite expensive.
By themselves, the flaws don't pose too much of a risk to users -- they only allow an attacker to leak, modify or delete emails. But combined with another kernel attack, such as the unpatchable Checkm8 exploit, the vulnerabilities could allow a bad actor root access to a specifically targeted device.
At least one of the flaws can be triggered remotely without any user interaction -- an attack known as a "zero-click." ZecOps added that the second vulnerability was likely discovered by accident while attempting to leverage the zero-click. The vulnerability impacting iOS 13 is the zero-click. While the iOS 12 flaw does require users to actually tap on an email, that requirement doesn't apply to attackers who send messages from a mail server that they control.

An example of a failed attack. Succesful ones wouldn't show an error message. Credit: ZecOps
In its report, ZecOps found that a number of its customers were targeted, including employees at a Fortune 500 company in North America, a journalist in Europe and a VIP in Germany. Interestingly, while there was evidence that the flaws were executed on targeted devices, the emails themselves weren't present. That suggests that the attackers deleted the emails to cover their tracks.
The researchers believe that the attackers were working for a nation-state that had purchased the attacks from a third party, adding that at least one "hacker-for-hire" organization was selling exploits that use email as the main vector.
On the other hand, security researchers who spoke to Motherboard said that the flaw was relatively unpolished compared to other hacks, meaning that sophisticated attackers would probably deem it too risky to use against "high value targets."
Still, ZecOps notes that attacks using the exploits are likely to increase in frequency since they're now publicly disclosed. The researchers said bad actors will "attack as many devices as possible," meaning that normal users could end up targeted. That becomes more dangerous if the exploits were leveraged by cybercriminals with access to additional vulnerabilities.
The vulnerabilities only impact the native Mail application, and not third-party apps. To mitigate the attacks, ZecOps recommends that users stop using Mail on iOS and iPadOS until a patch is issued. MacOS is unaffected.
ZecOps said it alerted Apple to the vulnerabilities in February. Both of the flaws have since been patched in the latest beta releases of iOS 13, and a fix is set to arrive in the next publicly available iOS update in iOS and iPadOS 13.4.5

Comments
Just because it's never happened to you, doesn't mean it never happens... There are plenty of examples where things like this affected tens of thousands (or more) people/websites/systems.
ZecOps says Outlook and Gmail are not vulnerable. I'm on the patched 13.4.5 beta but would otherwise probably just hold out for the 13.4.5 final.
One day, it will.
You are wrong.
ZecOps discovered the flaw in a forensic analysis of actual recorded security incidents. This isn't a theoretical vulnerability.
They reported this vulnerability to Apple back in February. It is reasonable to believe that ongoing analysis since then continues to validate their findings. It also appears to be acknowledged by Apple as a legitimate threat based on Apple's fix in the most recent 13.4.5 beta.
Apple may have silently conceded this a few months ago when they incongruously numbered the next iOS beta as 13.4.5 instead of incrementally following with 13.4.2. There is a good chance that Apple will release 13.4.2 with this vulnerability patched in the upcoming days rather than wait for the normal beta cycle of 13.4.5 to finish along its normal release timeline.
It will be interesting to see if Apple releases security updates for previous iOS versions. I have two iDevices on iOS 12.4.1 since I refuse to upgrade to iOS 13. I have a third device on iOS 12.4.6 which is unable to upgrade to iOS 13.
And what can one do if one suspects they have already been targeted?
How does one go about clearing/protecting the device till the new ios is released?
I talked to Apple support ..
They said the only way to be sure that there is no infection already is to completely erase and reset..... And then restore from backup.
I did and went one step further and enrolled in beta and installed the ios 13.4.5 beta which addresses these vulnerabilities.
It took a couple hours to get it all done and restored.
Cheers🤙🏼