New 'EvilQuest' ransomware is actively targeting macOS users in the wild
A new piece of Mac ransomware distributed via pirated software, dubbed "EvilQuest," is actively targeting macOS users in the wild.

EvilQuest is a new piece of Mac ransomware, but also has capabilities that could allow attackers full access of infected Macs.
Although ransomware specifically aimed at Mac users are particularly rare, new instances of malicious software that encrypt user files and demands a ransom to unlock them do surface from time to time.
On Tuesday, several security researchers published analysis and reports of the newly discovered "OSX.EvilQuest" ransomware. First spotted by independent malware researcher Dinesh Devadoss, EvilQuest is said to have been circulating in the wild since the start of June 2020, ZDNet reported.
EvilQuest has a few nefarious additions that make it unique among ransomware examples. In addition to maliciously encrypting a user's files and charging money to unlock them, EvilQuest also installs a keylogger and a reverse shell on a system, along with code that steals cryptocurrency wallet files.
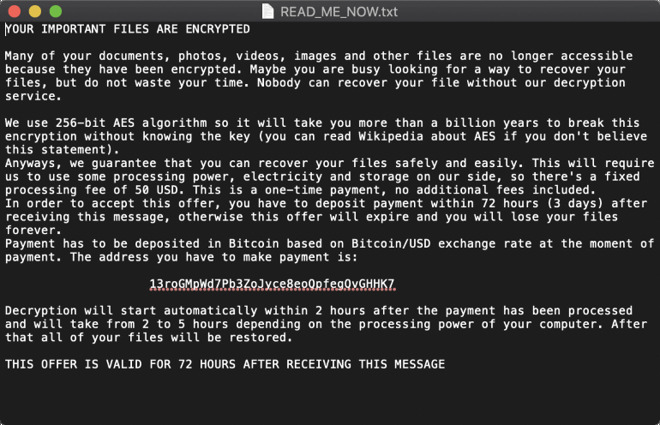
The EvilQuest ransom note. Credit: Patrick Wardle
According to former NSA hacker and Jamf macOS security researcher Patrick Wardle, those capabilities could allow attackers "full control over an infected host."
As with previous pieces of Mac ransomware, it appears that EvilQuest is distributed via pirated software. Researchers have found it bundled in a package called Google Software Update, while others have seen it hidden in pirated versions of DJ app Mixed In Key and security tool Little Snitch.
According to Malwarebytes Mac & Mobile chief Thomas Reed, the ransomware also attempts to modify files in Google Chrome's update mechanism in an effort to gain persistence on an infected machine.
This the third instance of a piece of ransomware surfacing that specifically targets macOS users, following the discovery of Patcher in 2017 and KeRanger in 2016.
There are also two apps that can mitigate the risks of EvilQuest for users.
Wardle's free and open-source RansomWhere? app can generically detect and stop ransomware on macOS. The latest version of Malwarebytes can also detect and mitigate EvilQuest before it does any damage.

EvilQuest is a new piece of Mac ransomware, but also has capabilities that could allow attackers full access of infected Macs.
Although ransomware specifically aimed at Mac users are particularly rare, new instances of malicious software that encrypt user files and demands a ransom to unlock them do surface from time to time.
On Tuesday, several security researchers published analysis and reports of the newly discovered "OSX.EvilQuest" ransomware. First spotted by independent malware researcher Dinesh Devadoss, EvilQuest is said to have been circulating in the wild since the start of June 2020, ZDNet reported.
EvilQuest has a few nefarious additions that make it unique among ransomware examples. In addition to maliciously encrypting a user's files and charging money to unlock them, EvilQuest also installs a keylogger and a reverse shell on a system, along with code that steals cryptocurrency wallet files.

The EvilQuest ransom note. Credit: Patrick Wardle
According to former NSA hacker and Jamf macOS security researcher Patrick Wardle, those capabilities could allow attackers "full control over an infected host."
As with previous pieces of Mac ransomware, it appears that EvilQuest is distributed via pirated software. Researchers have found it bundled in a package called Google Software Update, while others have seen it hidden in pirated versions of DJ app Mixed In Key and security tool Little Snitch.
According to Malwarebytes Mac & Mobile chief Thomas Reed, the ransomware also attempts to modify files in Google Chrome's update mechanism in an effort to gain persistence on an infected machine.
This the third instance of a piece of ransomware surfacing that specifically targets macOS users, following the discovery of Patcher in 2017 and KeRanger in 2016.
How to avoid or mitigate the EvilQuest ransomware
At this point, it appears that EvilQuest is solely being distributed through torrenting websites and pirated software. So if you stick to the Mac App Store or third-party developers that you trust, you should be able to avoid getting it.There are also two apps that can mitigate the risks of EvilQuest for users.
Wardle's free and open-source RansomWhere? app can generically detect and stop ransomware on macOS. The latest version of Malwarebytes can also detect and mitigate EvilQuest before it does any damage.

Comments
I don't have the time to research at the moment, but does iCloud Drive provide any ransomware protection?
OTOH I keep a lot of my files only on iCloud. I don’t know if they would be isolated enough.
Wow, imagine that. Stupid is as stupid does. Between fake Flash installers and pirate sites I guess those who get nailed deserve it.
So you’re pissed that your pirated version of Office is 32 bit so you go to a torrent to download another pirated copy of Office and wind up with ransomware. Too bad, so sad.
The Google Updater that comes with it, seems to me to be a pretty invasive piece of software.
It "phones home" to some Google server every 10-15 minutes and is quite hard to get rid of, even if you uninstall Chrome.
No wonder that hackers hook into this for their uses.
But as others have said, backups are crucial (anyway!). A couple different forms, too.
Does anyone happen to know how these things get triggered? Are they typically manually triggered? Or, do they wait for so long after being 'installed' to trigger? (I'd assume the strategy is to wait a while, or people would more likely have unaffected backups. On the other hand, if they wait too long, they are more likely to be detected.)
https://www.bleepingcomputer.com/news/security/evilquest-wiper-uses-ransomware-cover-to-steal-files-from-macs/
It says its starts automatically once the installer is run using a post-install script. It adds files to LaunchAgents too in order to launch beyond reboots. I really wish Apple would lock down the LaunchAgents feature. So few legitimate apps use it but so much malware does. That allows malware to start running again if it's stopped.
It can be something as simple as having a system watcher on the LaunchAgents folders and popping up a dialog saying something modified a secure folder. For legitimate apps, the user can type in a password to verify and it would be a quick warning when something is wrong. There's a Mac app that does this by creating a safe profile and then comparing when new files appear in dangerous locations:
https://sqwarq.com/detectx/
It would also be useful to have something that verifies the process lists on a computer, which should be quite fast. So when a process starts from a path that is unusual and with other identifying features like a small executable or is trying to do something with a lot of files, the system can also flag up a warning. If a process that is new to the system starts deleting thousands of files, that's a pretty big red flag for malware and the system can stop the executable from doing this.
I think new processes on a system should by default have only read access to the filesystem. The only time they need delete/write permissions is when the user explicitly interacts with them to save files.
I agree the alert on thee launch agent folder would be a good idea; treat it as a protected folder that requires authentication to modify, just like adding an application.
Not sure, but the article lists a few ways to check for it at the end. I just fire up Malwarebytes once in a while.
(As an aside, I almost feel bad just running the free mode, as they provide a useful service - though I've never found anything, nor with A/V since like back in OS7 days - but their subscription adds features I don't want and is kind of pricy, IMO. I'd be more likely to just buy a new version of it for $5-10 each time, or maybe $5-10/year. Do they actually get many buyers at $50+/yr?)