'Severe' AirDrop exploit could expose email and phone number in highly specific circumstan...
Researchers have demonstrated a theoretical risk of AirDrop sharing an iPhone user's phone number and email address with strangers.
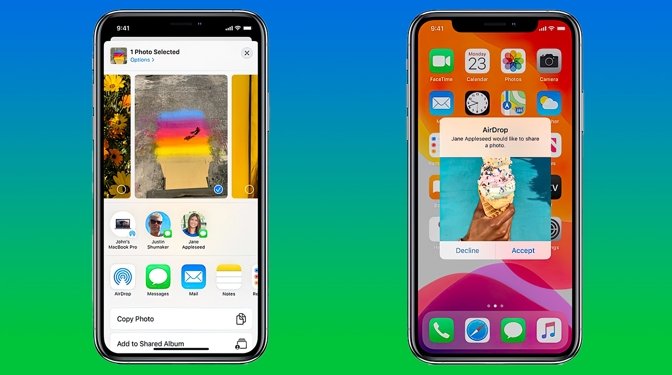
Researchers at Germany's Technische Universitat Darmstadt say AirDrop can reveal a user's phone number and email address to strangers
For hackers to steal this private information, they would need to perform a brute-force attack or another "simple technique," however. They would need to do this while being in physical proximity to a user with an open share sheet on an AirDrop-enabled Apple device.
While those are highly particular conditions, the researchers at Germany's Technische Universitat Darmstadt believe this vulnerability poses a "severe privacy leak."
"To determine whether the other party is a contact," the researchers wrote, "AirDrop uses a mutual authentication mechanism that compares a user's phone number and email address with entries in the other user's address book."
Although Apple encrypts that information, the researchers say the iPhone maker's hashing technique "fails to provide privacy-preserving contact discovery as so-called hash values can be quickly reversed using simple techniques such as brute-force attacks."
The security analysts found the AirDrop flaw in 2019. They reported it to Apple that May but never received any confirmation from the Cupertino company.
"So far," said the researchers, "Apple has neither acknowledged the problem nor indicated that they are working on a solution. This means that the users of more than 1.5 billion Apple devices are still vulnerable to the outlined privacy attacks. Users can only protect themselves by disabling AirDrop discovery in the system settings and by refraining from opening the sharing menu."
The researchers published a public warning for the first time on Wednesday.
AirDrop is often the quickest way to transfer content between iPhone, iPad, iPod touch, and Mac. The service debuted on the Mac in 2011 with OS X Lion and on iOS in 2013.
Stay on top of all Apple news right from your HomePod. Say, "Hey, Siri, play AppleInsider," and you'll get latest AppleInsider Podcast. Or ask your HomePod mini for "AppleInsider Daily" instead and you'll hear a fast update direct from our news team. And, if you're interested in Apple-centric home automation, say "Hey, Siri, play HomeKit Insider," and you'll be listening to our newest specialized podcast in moments.

Researchers at Germany's Technische Universitat Darmstadt say AirDrop can reveal a user's phone number and email address to strangers
For hackers to steal this private information, they would need to perform a brute-force attack or another "simple technique," however. They would need to do this while being in physical proximity to a user with an open share sheet on an AirDrop-enabled Apple device.
While those are highly particular conditions, the researchers at Germany's Technische Universitat Darmstadt believe this vulnerability poses a "severe privacy leak."
"To determine whether the other party is a contact," the researchers wrote, "AirDrop uses a mutual authentication mechanism that compares a user's phone number and email address with entries in the other user's address book."
Although Apple encrypts that information, the researchers say the iPhone maker's hashing technique "fails to provide privacy-preserving contact discovery as so-called hash values can be quickly reversed using simple techniques such as brute-force attacks."
The security analysts found the AirDrop flaw in 2019. They reported it to Apple that May but never received any confirmation from the Cupertino company.
"So far," said the researchers, "Apple has neither acknowledged the problem nor indicated that they are working on a solution. This means that the users of more than 1.5 billion Apple devices are still vulnerable to the outlined privacy attacks. Users can only protect themselves by disabling AirDrop discovery in the system settings and by refraining from opening the sharing menu."
The researchers published a public warning for the first time on Wednesday.
AirDrop is often the quickest way to transfer content between iPhone, iPad, iPod touch, and Mac. The service debuted on the Mac in 2011 with OS X Lion and on iOS in 2013.
Stay on top of all Apple news right from your HomePod. Say, "Hey, Siri, play AppleInsider," and you'll get latest AppleInsider Podcast. Or ask your HomePod mini for "AppleInsider Daily" instead and you'll hear a fast update direct from our news team. And, if you're interested in Apple-centric home automation, say "Hey, Siri, play HomeKit Insider," and you'll be listening to our newest specialized podcast in moments.

Comments
If you have to linger around people for so long that they start airdropping stuff to each other, and manage to hit the short second the sharing dialogue is open, without first being reported as a stalker, you probably know these people well enough to already know their name and phone number…
…and names and phone numbers used to be in public phone books without significant ill effect.
So, yeah, nice you found something, but no, it’s nothing to worry about, unless there’s significant more to it than is being reported.
They can then perform the "brute-force" part in their own time.
Even the ARS article goes off the deep tech end you really think some self respecting hacker is going sit around and monitor for the this to happen top get a name and email address maybe? Plus Airdrop needs to be on and they already need in some cases to know who the hacker is (ie a valid contact on their device) for it work. Eventually Apple might fix this if someone actually gets hacked this way in reality and knew about it to care.