Apple's Advanced Data Protection feature is here - what you need to know
Apple has rolled out Advanced Data Protection, which means even more of your iCloud data can be end-to-end encrypted. Here's why you may want to toggle this feature on, and what it means for your privacy.
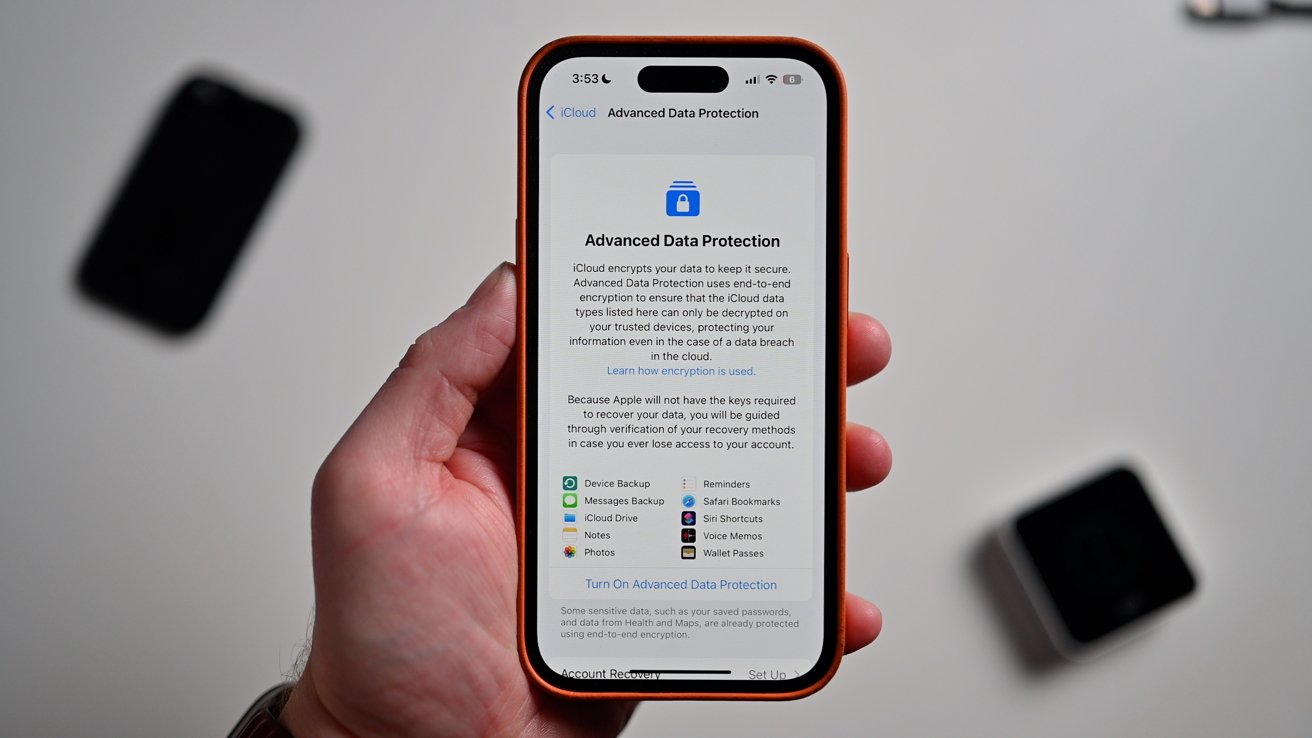
Advanced Data Protection
If you're reasing this, you probably know how end-to-end encryption works. For those of you who don't, here's a short analogy to help you understand why it's important.
Say you write a very personal letter to a friend and send it to them via the mail. There's nothing stopping someone from stealing the letter in transit to read what you wrote, aside from the very real threat of tampering with the mail.
Sure, an envelope prevents people from being able to see what you wrote at a glance. Like locks, envelopes primarily keep honest people honest.
Now, instead of just sending a letter to your friend, say you used a secret code only you and your friend know to obscure the information inside. That way, while in transit, the data is effectively useless to prying eyes.
Sure, someone could open your letter and look at it, but without knowing how to decode what was written, it's not terribly useful to the average ne'er do well.
While that is a very simple explanation, end-to-end encryption, or E2EE, works similarly. Apple encrypts plenty of your iCloud data already, like your text messages and health data.
Most of it, minus payment data, is stored in iCloud backups which are stored encrypted -- but Apple has the key. So, some of it can be retrieved by Apple if they are served a subpoena.
But, there is now a way to hide your data from nearly everyone -- including Apple.
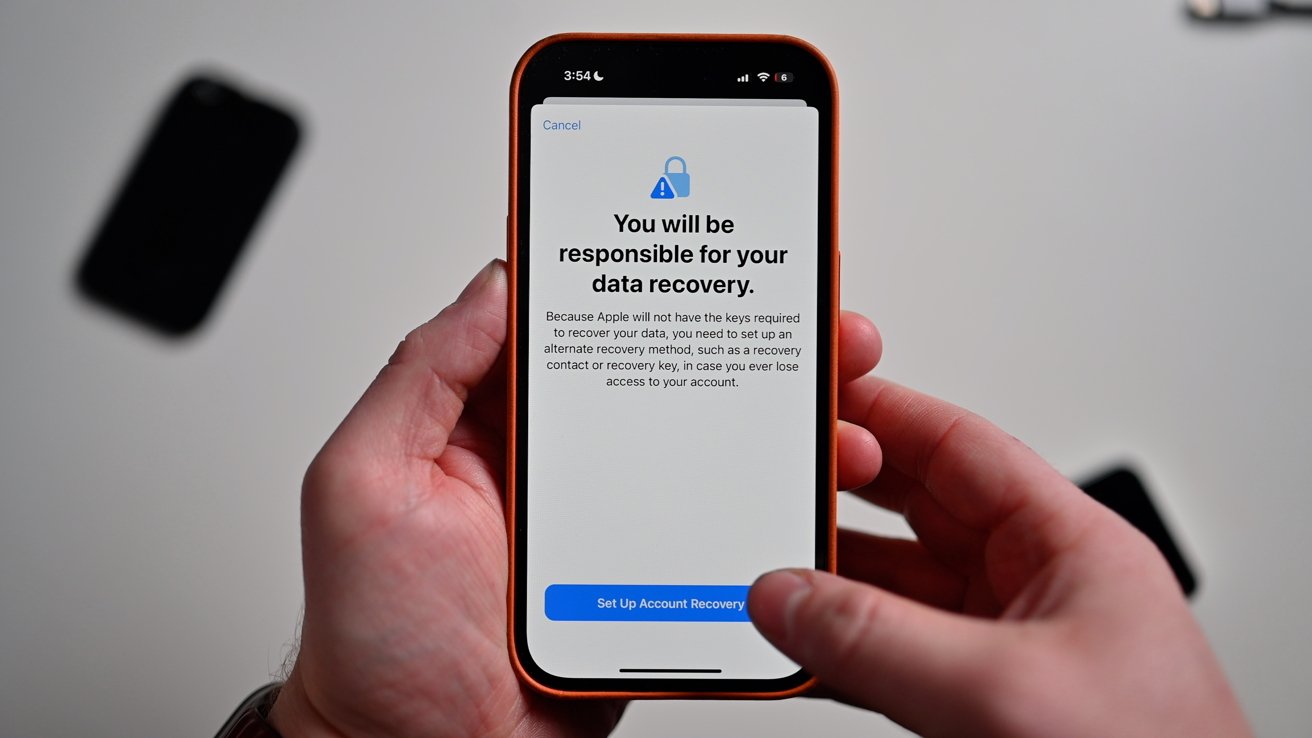
Data responsibility warning
As a reminder, this is an opt-in feature and not done automatically. This is an accountability issue -- if you lose access to your account and can't access it with a recovery method, your information is effectively locked away forever.
Everyday, everybody discloses a lot of personal information about ourselves to others -- our phone numbers, our birthdays, our locations when we will and won't be home.
And, if you're like many people, you may have a Notes file with particularly sensitive information sitting around on your iPhone. Imagine how dangerous that could be if a third party could easily read that information.
We take pictures of our possessions, of our family members, of our homes -- things that you may not want a stranger to casually thumb through.
And it isn't just identity thieves who want your data, either. Plenty of data brokers would love to have unrestricted access to your most personal information to better build their digital profile of you.
Then, they can sell that data -- without cutting you in, of course -- to ad agencies who might deem you an easy mark for a quick sale.
Encryption may not fully stop them from being able to track you, but it certainly can prevent them from knowing plenty of things they shouldn't.
This means that it is critical that you keep everything updated. Your iPhone, iPad, Apple Watch, and Apple TV -- everything.
This also means that if you've got unsupported devices, they may lose access to anything encrypted in your iCloud account.
You'll also want to be prepared in the event that you lose access to your iCloud account. Apple will automatically prompt you to set up a recovery person or recovery phrase. So make sure you choose someone trustworthy, or something easy to remember.
Once you're ready to take the leap, here's how you can start making your account extra secure.
Read on AppleInsider

Advanced Data Protection
If you're reasing this, you probably know how end-to-end encryption works. For those of you who don't, here's a short analogy to help you understand why it's important.
Say you write a very personal letter to a friend and send it to them via the mail. There's nothing stopping someone from stealing the letter in transit to read what you wrote, aside from the very real threat of tampering with the mail.
Sure, an envelope prevents people from being able to see what you wrote at a glance. Like locks, envelopes primarily keep honest people honest.
Now, instead of just sending a letter to your friend, say you used a secret code only you and your friend know to obscure the information inside. That way, while in transit, the data is effectively useless to prying eyes.
Sure, someone could open your letter and look at it, but without knowing how to decode what was written, it's not terribly useful to the average ne'er do well.
While that is a very simple explanation, end-to-end encryption, or E2EE, works similarly. Apple encrypts plenty of your iCloud data already, like your text messages and health data.
What iCloud data Apple automatically encrypted
Apple already has a great deal of data that is encrypted by default.- Health data
- iCloud Keychain
- Wi-Fi and Cellular credentials
- Home data
- Payment information
- Siri information
- iMessage and FaceTime content

Most of it, minus payment data, is stored in iCloud backups which are stored encrypted -- but Apple has the key. So, some of it can be retrieved by Apple if they are served a subpoena.
But, there is now a way to hide your data from nearly everyone -- including Apple.
What data Advanced Data Protection encrypts
Apple's new Advanced Data Protection feature goes a step further and allows you to encrypt additional information in iCloud with a few new layers of security.Data encrypted by enabling Advanced Data Protection
- Device backups
- Messages backups
- iCloud Drive
- Notes
- Photos
- Reminders
- Safari Bookmarks
- Voice Memos
- Wallet passes

Data responsibility warning
As a reminder, this is an opt-in feature and not done automatically. This is an accountability issue -- if you lose access to your account and can't access it with a recovery method, your information is effectively locked away forever.
Why you should enable Advanced Data Protection
Encryption protects you from being targeted by all sorts of people who would want nothing more than to snoop through your data. That encryption of your data is crucial to keep yourself safe -- even if you think you don't have anything to hide.Everyday, everybody discloses a lot of personal information about ourselves to others -- our phone numbers, our birthdays, our locations when we will and won't be home.
And, if you're like many people, you may have a Notes file with particularly sensitive information sitting around on your iPhone. Imagine how dangerous that could be if a third party could easily read that information.
We take pictures of our possessions, of our family members, of our homes -- things that you may not want a stranger to casually thumb through.
And it isn't just identity thieves who want your data, either. Plenty of data brokers would love to have unrestricted access to your most personal information to better build their digital profile of you.
Then, they can sell that data -- without cutting you in, of course -- to ad agencies who might deem you an easy mark for a quick sale.
Encryption may not fully stop them from being able to track you, but it certainly can prevent them from knowing plenty of things they shouldn't.
Keeping your data accessible
Of course, you're going to want to make sure that you can still access your data across all your devices associated with your Apple ID.This means that it is critical that you keep everything updated. Your iPhone, iPad, Apple Watch, and Apple TV -- everything.
This also means that if you've got unsupported devices, they may lose access to anything encrypted in your iCloud account.
You'll also want to be prepared in the event that you lose access to your iCloud account. Apple will automatically prompt you to set up a recovery person or recovery phrase. So make sure you choose someone trustworthy, or something easy to remember.
Once you're ready to take the leap, here's how you can start making your account extra secure.
How to enable Advanced Data Protection
- On your iPhone, open Settings
- Tap Apple ID
- Tap iCloud
- Scroll down and toggle on Advanced Data Protection
Read on AppleInsider

Comments
Adding a Recovery Contact is recommended.
Not currently available in the UK either. Would have been nice to have known before attempting to activate it.