Most older iPhones, Macs, and iPads are vulnerable to a new GPU security flaw
A security flaw named LeftoverLocals lets attackers access data that has been processed in a device's GPU, and while Apple says A17 iPhone and M3 Macs have fixes, older models do not.

Researchers show how a GPU vulnerability could be exploited
The report, and the naming of LeftoverLocals, comes from Trail of Bits, which previously demonstrated how Apple's walled garden iPhone security can benefit hackers. The organization now says it has found "vulnerability that allows recovery of data from GPU local memory created by another process on Apple, Qualcomm, AMD, and Imagination GPUs."
It's a particularly significant vulnerability both because of the volume of data that may be read, and also because GPUs are being increasingly used in AI for processing of Large Language Models (LLMs.)
"By recovering local memory -- an optimized GPU memory region," wrote Trail of Bits in a blog post, "we were able to build a PoC [Proof of Concept] where an attacker can listen into another user's interactive LLM session (e.g., llama.cpp) across process or container boundaries."
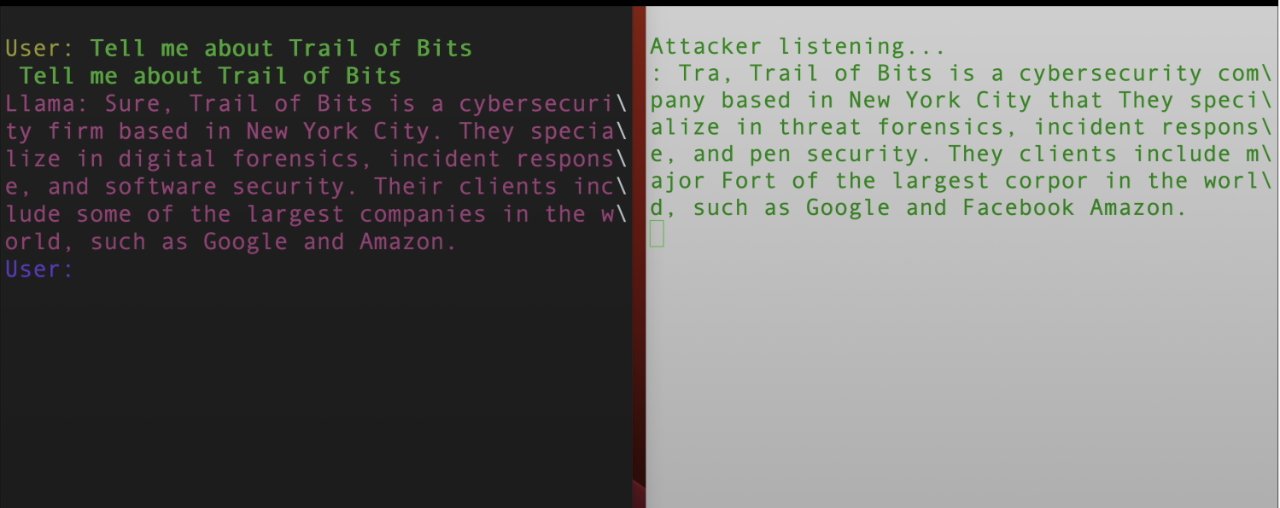
Left: a user's typing into AI. Right: how much an attacker can receive
While Apple was reportedly slow to respond to information from the researchers, it did patch certain devices. "We re-tested the vulnerability on January 10," said the researchers, "where it appears that some devices have been patched, i.e., Apple iPad Air 3 (A12)."
"However, the issue still appears to be present on the Apple MacBook Air (M2)," they continue. "Furthermore, the recently released Apple iPhone 15 does not appear to be impacted as previous versions have been."
Apple has told Wired that fixes had been shipped for the latest iPhones and Macs with A17 and M3 devices,
How to protect yourself from LeftoverLocals
The vulnerability requires access to a user's device, it can't be done remotely. For now, for users with a vulnerable device, the best way to protect themselves is to never give a third party access to their devices. Also, users should also always install the latest security updates from Apple.
It's not clear if Apple has patch plans going forward for impacted devices.
Read on AppleInsider

Comments
Should have been in the first sentence so I could stop reading there.
The vast majority of M1 and M2 users won't be affected by this bug even if Apple doesn't patch all models. Requires physical access, is only useful for pulling info from LLM (and if you look at the screenshots it isn't even reliable at that), and it's present in Qualcomm, AMD, and Imagination GPUs (It's a conspiracy I tells ya!).
It doesn't require access to the device. The attack can be executed from a malicious app. The blog post states:
It is still not trivial to exploit (apps need to be run at the same time), but certainly doesn't require physical access.