Proof of concept phishing attack mimics iOS popups to steal user passwords
Demonstrating a potentially glaring iOS security hole, developer Felix Krause created a proof of concept phishing attack that takes advantage of system popups, and the way users interact with these messages, to steal Apple ID credentials.
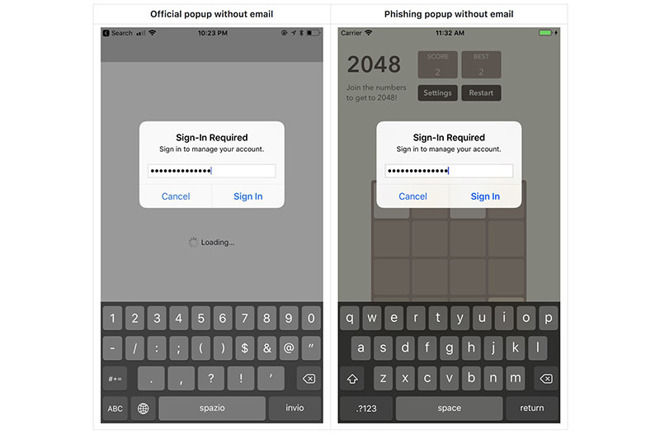
Detailing the method in a blog post on Tuesday, Krause notes Apple's iOS prompts users to enter their iTunes password, or Apple ID password, on a rather frequent basis. Whether it be an app download, firmware update or authentication for in-app purchases, the credential-seeking popups have for many become part of the iOS experience.
With requests pervading iOS, and an inherent trust that the requests are legitimate, Apple has inadvertently trained users to hand over their password without scrutiny. This behavior, combined with some handiwork on the part of malicious developers, presents a real security threat, Krause says.
The developer notes a simple UIAlertController, carefully crafted to mimic Apple's system dialog, can be employed in a successful phishing attack. As seen in the screenshot above, Krause was able to create a phony password request popup that would likely fool a large number of iOS users.
Further, while some alerts require an app to know a user's email address, others authorization popups do not.
Though the loophole has been a known problem for some time, Krause has decided not to reveal the source of his crafted popup. However, the developer said it was "shockingly easy" to replicate Apple's official dialog, noting the project comprised less than 30 lines of code.
Krause points out that an app containing such code is unlikely to make it through the App Store approval process, but developers can use a number of -- unsanctioned -- workarounds to execute malicious code after their title goes live.
While there is no surefire way to defend against the popup phishing attack, users can protect themselves by exercising caution when handing over sensitive information.
For example, users can test whether a dialog is legitimate by pressing the home button when presented with a suspicious app, Krause says. If the action closes the app and dialog, the popup can be determined to be a phishing attack and not a legitimate Apple system process.
Krause suggests users refrain from entering credentials into popups altogether. Instead, users should dismiss suspicious dialogs and enter password information in the Settings app. Two-factor authentication might protect against some attacks, but crafty developers can get around the password and code protocol using phishing methods similar to those described above.
In a radar filed to Apple, Krause proposes iOS should indicate whether a dialog originates from a system request or an app request. He also suggests all password requests be handled in the Settings app, not through direct popups.

Detailing the method in a blog post on Tuesday, Krause notes Apple's iOS prompts users to enter their iTunes password, or Apple ID password, on a rather frequent basis. Whether it be an app download, firmware update or authentication for in-app purchases, the credential-seeking popups have for many become part of the iOS experience.
With requests pervading iOS, and an inherent trust that the requests are legitimate, Apple has inadvertently trained users to hand over their password without scrutiny. This behavior, combined with some handiwork on the part of malicious developers, presents a real security threat, Krause says.
The developer notes a simple UIAlertController, carefully crafted to mimic Apple's system dialog, can be employed in a successful phishing attack. As seen in the screenshot above, Krause was able to create a phony password request popup that would likely fool a large number of iOS users.
Further, while some alerts require an app to know a user's email address, others authorization popups do not.
Though the loophole has been a known problem for some time, Krause has decided not to reveal the source of his crafted popup. However, the developer said it was "shockingly easy" to replicate Apple's official dialog, noting the project comprised less than 30 lines of code.
Krause points out that an app containing such code is unlikely to make it through the App Store approval process, but developers can use a number of -- unsanctioned -- workarounds to execute malicious code after their title goes live.
While there is no surefire way to defend against the popup phishing attack, users can protect themselves by exercising caution when handing over sensitive information.
For example, users can test whether a dialog is legitimate by pressing the home button when presented with a suspicious app, Krause says. If the action closes the app and dialog, the popup can be determined to be a phishing attack and not a legitimate Apple system process.
Krause suggests users refrain from entering credentials into popups altogether. Instead, users should dismiss suspicious dialogs and enter password information in the Settings app. Two-factor authentication might protect against some attacks, but crafty developers can get around the password and code protocol using phishing methods similar to those described above.
In a radar filed to Apple, Krause proposes iOS should indicate whether a dialog originates from a system request or an app request. He also suggests all password requests be handled in the Settings app, not through direct popups.

Comments
Just a thought.
This one is quite obviously a huge one that Apple needs to address... What good is password if a hacker can get it with just 30 lines of code?
You leaped to the wrong conclusion. The 3rd party app does not know your info. Look at the screen shot in the article. It does not mention their Apple ID nor does it validate the password when put in. It merely captures it. The hacker then logs into your iCloud account and locks the device with a message to email them. Once you do, they tell you to pay to unlock it.
Good article in that it announced a potential problem, listed how unlikely it is, and told how to best avoid it. Would only ask that the solution to avoid it paragraph be bolded or something for those of us that scan through these quickly.
Lesson to learn: always use the latest version of macOS, and enable 2-factor authentication in your AppleID account. 2-factor authentication will send a PIN code to one of your trusted devices as the second verification step after entering your correct password.
Apple ID authentication should be setup ONLY in the Settings, and then verified via Touch ID. All the Apple Apps should reference that or make the user go back there. There shouldn't be random Apple ID asking popups outside of that. It's just teaching the users to be phished.
(Another entry for my Apple bad design list.)
Whether it's possible for a nefarious developer to use that poor behavior on Apple's part to phish a user who isn't as highly aware as you, is kind of what this article is about.
Either way, it's sloppy development and design on Apple's part. And, when you get sloppy about security, you *train* the average user to fall prey to phishing schemes.