The top malware threat for macOS infects one in 10 users
Security firm Kaspersky says that in 2019 the Shlayer Trojan infected one in ten Mac users, opening the door to malicious apps that hide behind fake error messages about users needing to update Flash.

Kaspersky claims that the Mac is proving to be profitable for cyber criminals
According to security firm Kapersky, Macs have been the frequent target of what's called the Shlayer Trojan. The company reports that this has been active since at least early 2018, but in 2019 specifically it was the most common threat to macOS. Around 10% of all Macs were attacked with it, and by itself, Shlayer represents 30% of all the Trojans detected on macOS.
The Shlayer Trojan is a delivery mechanism for a variety of malware payloads. It gets onto a Mac and then while not specifically harming the machine itself, it fetches other malicious code, typically adware.
From the user's perspective, there are three stages to what happens. The first is that they click on a link to a site which initiates a download of the Shlayer Trojan to the user's Mac. Kaspersky's report says that "thousands of websites" include this download, typically because the sites partner with cyber criminals.
However, legitimate sites could have this added, too.
"[These include] YouTube, where links to the malicious website were included in video descriptions," says Kaspersky in its report, "and Wikipedia, where such links were hidden in the articles' references."
Typically links take users to advertising pages which try to persuade them to download software. According to Kaspersky, a common method is to display faked messages about Adobe Flash being out of date. The "Download Flash" button actually downloads the Trojan.

A fake Flash update notification on a site. (Source: Kaspersky)
Once downloaded, the user is prompted to install an application. It doesn't follow macOS's regular installation procedure though. Rather than double-clicking to install, the user is directed to first right-click and choose Open Package.
Then when it has been installed, the Shlayer Trojan itself downloads adware or other such malicious apps. These are still new apps being downloaded onto a Mac and so in theory they cannot be installed without the user's permission -- but there is a way around it.
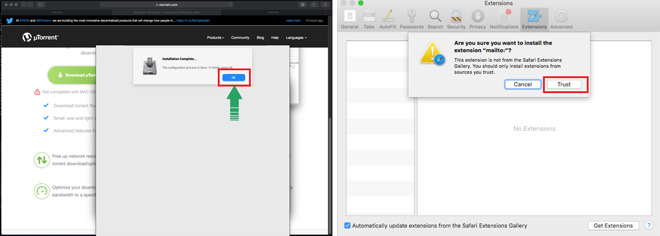
One type of malware that the Shlayer Trojan installs is a Safari Extension and the Mac does ask if you are sure that you want to use it. However, while macOS is warning that this is an unrecognized extension, Shlayer is overlaying that message with a fake dialog box saying that the installation is complete.
Users see an "Okay" button and click it, but in reality they are clicking a Trust button that macOS was actually displaying. They are telling the Mac that it is okay to install this software, so it does.
The final stage is that, at present, the Mac user can be bombarded with ads. Any browsing can also be affected by targeted ads being presented.
"[Since February 2018] we have collected almost 32,000 different malicious samples of the Trojan," says Kaspersky. "Having studied the Shlayer family, we can conclude that the macOS platform is a good source of revenue for cybercriminals."
Left: what the user sees. Right: what the Mac is actually displaying (Source: Kaspersky)
Significantly, Kaspersky says that even though the Trojan was detected almost two years ago, it is still prevalent.
"The operation algorithm has changed little since Shlayer was first discovered, nor has its activity decreased much," the company continues. "[The] number of detections remains at the same level as in the first months after the malware was uncovered."
While Kaspersky reports that this particular Trojan is operating at around the same level as it always has, a separate report from Malwarebytes in April 2019 claims that Mac malware overall has grown enormously.

Kaspersky claims that the Mac is proving to be profitable for cyber criminals
According to security firm Kapersky, Macs have been the frequent target of what's called the Shlayer Trojan. The company reports that this has been active since at least early 2018, but in 2019 specifically it was the most common threat to macOS. Around 10% of all Macs were attacked with it, and by itself, Shlayer represents 30% of all the Trojans detected on macOS.
The Shlayer Trojan is a delivery mechanism for a variety of malware payloads. It gets onto a Mac and then while not specifically harming the machine itself, it fetches other malicious code, typically adware.
From the user's perspective, there are three stages to what happens. The first is that they click on a link to a site which initiates a download of the Shlayer Trojan to the user's Mac. Kaspersky's report says that "thousands of websites" include this download, typically because the sites partner with cyber criminals.
However, legitimate sites could have this added, too.
"[These include] YouTube, where links to the malicious website were included in video descriptions," says Kaspersky in its report, "and Wikipedia, where such links were hidden in the articles' references."
Typically links take users to advertising pages which try to persuade them to download software. According to Kaspersky, a common method is to display faked messages about Adobe Flash being out of date. The "Download Flash" button actually downloads the Trojan.

A fake Flash update notification on a site. (Source: Kaspersky)
Once downloaded, the user is prompted to install an application. It doesn't follow macOS's regular installation procedure though. Rather than double-clicking to install, the user is directed to first right-click and choose Open Package.
Then when it has been installed, the Shlayer Trojan itself downloads adware or other such malicious apps. These are still new apps being downloaded onto a Mac and so in theory they cannot be installed without the user's permission -- but there is a way around it.
One type of malware that the Shlayer Trojan installs is a Safari Extension and the Mac does ask if you are sure that you want to use it. However, while macOS is warning that this is an unrecognized extension, Shlayer is overlaying that message with a fake dialog box saying that the installation is complete.
Users see an "Okay" button and click it, but in reality they are clicking a Trust button that macOS was actually displaying. They are telling the Mac that it is okay to install this software, so it does.
The final stage is that, at present, the Mac user can be bombarded with ads. Any browsing can also be affected by targeted ads being presented.
"[Since February 2018] we have collected almost 32,000 different malicious samples of the Trojan," says Kaspersky. "Having studied the Shlayer family, we can conclude that the macOS platform is a good source of revenue for cybercriminals."

Left: what the user sees. Right: what the Mac is actually displaying (Source: Kaspersky)
Significantly, Kaspersky says that even though the Trojan was detected almost two years ago, it is still prevalent.
"The operation algorithm has changed little since Shlayer was first discovered, nor has its activity decreased much," the company continues. "[The] number of detections remains at the same level as in the first months after the malware was uncovered."
While Kaspersky reports that this particular Trojan is operating at around the same level as it always has, a separate report from Malwarebytes in April 2019 claims that Mac malware overall has grown enormously.

Comments
It makes me totally understand why Apple wants to clamp down as much as possible on their platforms. It’s in their best interest for customers to feel safe buying computers. As a support person, it wasn’t within my ability to control the world or what people do with their computers, but I still had to witness constant abuse of end users, including by legit developers and product-makers. Adding scammers on top... What a hellscape this industry can seem.
"Flash might not work be used until you download an update from Adobe."
Note that:
1. Adobe has its faults, but their employees aren't illiterate.
2. If you really do need to update Flash, then yes, download it from Adobe, and not from some random pop-up link.
3. Almost nobody needs to have Flash.
Meanwhile, scan with a malware program such as MalwareBytes. The free version works fine.
Periodically I reread Steve Jobs' famous letter about Flash, just to remind myself how smart the guy was and how right on this subject.
It says "one in ten of our Mac security solutions encountered this malware at least once".
If their "Mac security solutions" are installed on 1/100,000 of total active Macs, the one tenth of that makes 1/1,000,000 of total active Macs.
I got one from "Facebook" the other day.
Unfortunately for the scumbags, I've never even had a Facebook account.
A lot of the malware or scams seem to be coming from illiterate people who are not very bright and also not very fluent in English.
A friend of mine got an email from "Apple" last year, telling them to reset their password, and they asked me to take a look at the email, and the grammar was a total joke.
(1) Apple would never send out any emails asking people to reset their password
(2) Apple would never hire monkeys who can't even write in English