Research finds 14% of mobile apps leave user data in unsecured servers
App developers rely on third-party servers to simplify data storage, but new research indicates that these servers are often left with little to no security over sensitive data.

Developers are leaving servers unsecured which makes user data vulnerable
Third-party servers from Amazon, Google, and Microsoft offer a simple way to store user data and system files without having to fuss with coding the server yourself. However, developers reportedly often forget to secure these servers and leave user data out in the open for anyone to find and steal.
New research from Zimperium indicates that this occurs across all app categories regardless of the provider. They found that 14% of iOS and Android apps that use cloud storage had unsecured configurations and were vulnerable to attack.
The research notes that the type of data available in these servers depends on the apps in question, but all data stored can be used by bad actors. The unsecured data covers everything from names and addresses to medical and financial data about each user.
Zimperium says that vulnerabilities and data left exposed can be used to gain access to even more sensitive data and operating processes. Some apps leaked entire cloud infrastructure scripts including SSH keys and passwords to payment kiosks.
Wired talked with the researchers about the report, citing that they had discovered 84,000 Android apps and 47,000 iOS apps using public cloud services. Of those using the services, 14% were exposing user data.
"It's a disturbing trend," Shridhar Mittal, Zimperium's CEO said to Wired. "A lot of these apps have cloud storage that was not configured properly by the developer or whoever set things up and, because of that, data is visible to just about anyone. And most of us have some of these apps right now."
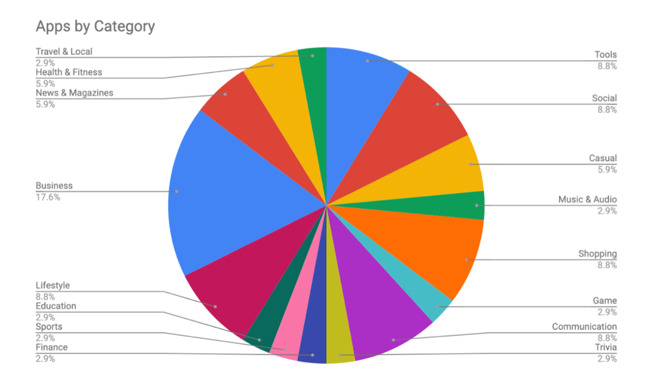
App categories with server permission and security issues. Image credit: Zimperium
The issue lies in developers who do not secure their server, so any and all app categories are affected. The largest affected categories discovered by the research include business, shopping, social, communications, and tools.
App users cannot affect this situation directly, but you can be aware of the apps you use and their reputation. If a data leak occurs on a popular app, it usually gets reported in popular news sources, however, not all leaks are reported to the public.
Apple uses third-party servers for iCloud and other portions of its business. Its systems have been attacked before, and even breached, but no user data has been stolen. The company utilizes the best security available for its AWS and Google Cloud instances.
Developers need to take note of this issue and act. Using third-party servers isn't an issue if proper security is set up for the server and data is protected. Zimperium hopes their research can prompt developers to take action and secure their data services.

Developers are leaving servers unsecured which makes user data vulnerable
Third-party servers from Amazon, Google, and Microsoft offer a simple way to store user data and system files without having to fuss with coding the server yourself. However, developers reportedly often forget to secure these servers and leave user data out in the open for anyone to find and steal.
New research from Zimperium indicates that this occurs across all app categories regardless of the provider. They found that 14% of iOS and Android apps that use cloud storage had unsecured configurations and were vulnerable to attack.
The research notes that the type of data available in these servers depends on the apps in question, but all data stored can be used by bad actors. The unsecured data covers everything from names and addresses to medical and financial data about each user.
Zimperium says that vulnerabilities and data left exposed can be used to gain access to even more sensitive data and operating processes. Some apps leaked entire cloud infrastructure scripts including SSH keys and passwords to payment kiosks.
Wired talked with the researchers about the report, citing that they had discovered 84,000 Android apps and 47,000 iOS apps using public cloud services. Of those using the services, 14% were exposing user data.
"It's a disturbing trend," Shridhar Mittal, Zimperium's CEO said to Wired. "A lot of these apps have cloud storage that was not configured properly by the developer or whoever set things up and, because of that, data is visible to just about anyone. And most of us have some of these apps right now."

App categories with server permission and security issues. Image credit: Zimperium
The issue lies in developers who do not secure their server, so any and all app categories are affected. The largest affected categories discovered by the research include business, shopping, social, communications, and tools.
App users cannot affect this situation directly, but you can be aware of the apps you use and their reputation. If a data leak occurs on a popular app, it usually gets reported in popular news sources, however, not all leaks are reported to the public.
Apple uses third-party servers for iCloud and other portions of its business. Its systems have been attacked before, and even breached, but no user data has been stolen. The company utilizes the best security available for its AWS and Google Cloud instances.
Developers need to take note of this issue and act. Using third-party servers isn't an issue if proper security is set up for the server and data is protected. Zimperium hopes their research can prompt developers to take action and secure their data services.

Comments
the best they could feasibly do, and probably do, is have the data encrypted at rest and require data to be sent over ssl/tls. Just about everything else would require some degree of intimate knowledge of the custom software running on the servers, and would require the cloud providers to audit these applications akin to what Apple does on the App Store, just vastly more difficult due to the range of software, operating systems, languages, and data storage options there are in the cloud.