How Apple iCloud Private Relay works
In a WWDC developer video, Apple has further explained what protection its iCloud Private Relay will give users, plus how exactly it works to increase privacy.

The new iCloud Private Relay will protect users who have an iCloud+ subscription
Announced at the WWDC 2021 Keynote, iCloud Private Relay is a new feature for Apple users which will prevent third-party companies determining web-browsing habits. It's not going to be available in all countries, but for those that it is, Apple has produced a system that it claims will greatly protect users, yet not also slow down their internet.
"When someone accesses the internet, anyone on their local network can see the names of all of the websites they access based on inspecting DNS queries," says Tommy Pauly of Apple's Internet Technologies group, in a new video for developers.
"This information can be used to fingerprint a user and build a history of their activity over time," he continues. "No one should be able to silently collect all of this information, whether it's a public Wi-Fi operator, another user on the network, or an internet service provider."
Pauly also describes how servers can see a user's IP address when they access a site, and says that "even worse," those servers can "fingerprint user identity" across different sites.
"These are big problems for user privacy, and in order to fix them, we need a new approach that has privacy built in by design," he says. "iCloud Private Relay adds multiple secure proxies to help route user traffic and keep it private."
"The proxies are run by separate entities," continues Pauly. "One is Apple, and one is a content provider."
Apple does not say which firm, or firms, are the other entity. Delziel Fernandes, also from Apple's Internet Technologies group, refers instead solely to what he calls ingress servers, run by Apple, and egress servers, run by other firms.
"When a device tries to access a server, it first sets up a network connection to the ingress proxy," says Fernandes. "This connection is set up using an IP address assigned by the network provider... [and the] egress proxy then forwards these requests to the destination servers by choosing an IP address that maps to the device's city or region."
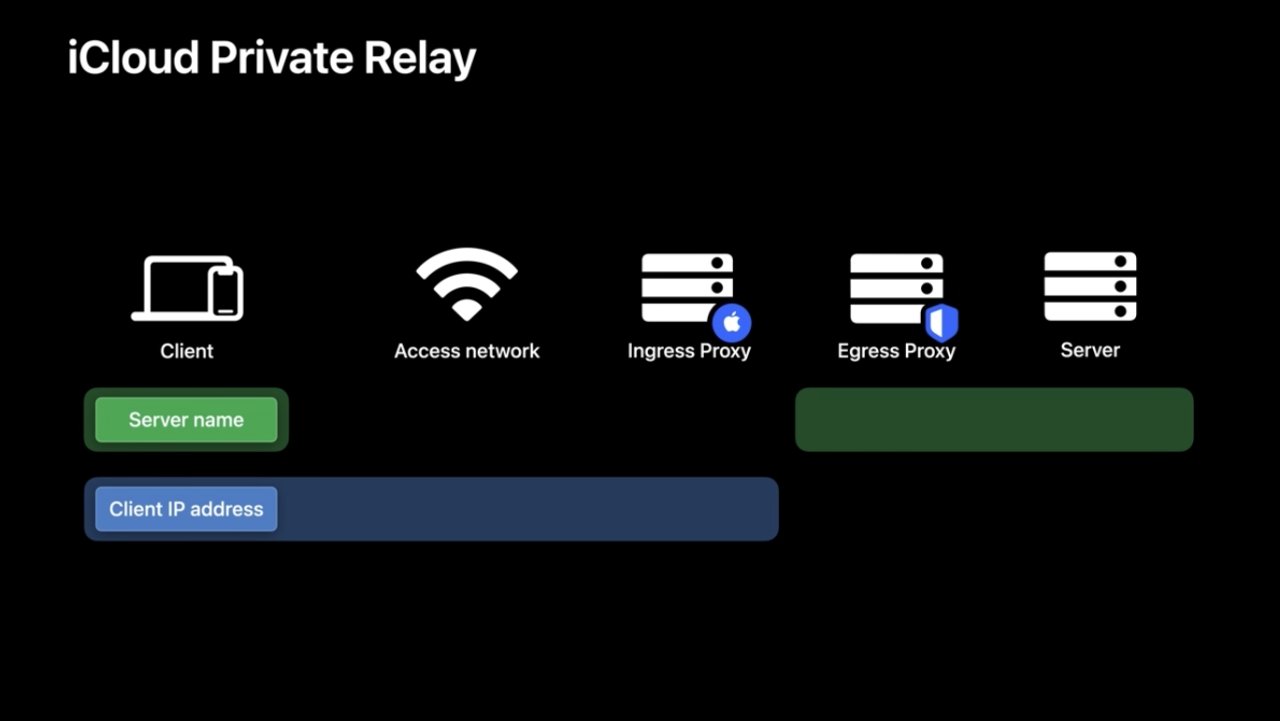
Apple's illustrative diagram of how iCloud Private Relay works
What this means for the user is that Apple doesn't track which websites they're accessing. And neither the egress server company nor the destination website can track their identities in any way.
There are features developers can access within iCloud Private Relay that mean they can ask for a user's specific location -- if the user allows, and if the app requires it. But otherwise location data is set by the egress server. That third-party and presumably trusted company adds an IP address "that maps to the device's city or region."
So a site or a service gets some location data and it's broadly right, it's correct enough to be useful for, say, a store showing its prices in the right currency or content-gating by geography.
The new iCloud Private Relay is to be introduced alongside macOS Monterey, iOS 15, and iPadOS 15 when they launch later in the year. It will require an iCloud+ subscription, and users will have to choose to turn on Private Relay -- though it is likely to default to on.
"Private Relay is built into iOS and macOS, so you don't need to do anything to adopt it from your app," Pauly told developers. "It's also important to understand that it won't always be affecting your app. It will only apply when a user is an iCloud+ subscriber and has Private Relay enabled."
Follow all the details of WWDC 2021 with the comprehensive AppleInsider coverage of the whole week-long event from June 7 through June 11, including details of all the new launches and updates.
Stay on top of all Apple news right from your HomePod. Say, "Hey, Siri, play AppleInsider," and you'll get latest AppleInsider Podcast. Or ask your HomePod mini for "AppleInsider Daily" instead and you'll hear a fast update direct from our news team. And, if you're interested in Apple-centric home automation, say "Hey, Siri, play HomeKit Insider," and you'll be listening to our newest specialized podcast in moments.

The new iCloud Private Relay will protect users who have an iCloud+ subscription
Announced at the WWDC 2021 Keynote, iCloud Private Relay is a new feature for Apple users which will prevent third-party companies determining web-browsing habits. It's not going to be available in all countries, but for those that it is, Apple has produced a system that it claims will greatly protect users, yet not also slow down their internet.
"When someone accesses the internet, anyone on their local network can see the names of all of the websites they access based on inspecting DNS queries," says Tommy Pauly of Apple's Internet Technologies group, in a new video for developers.
"This information can be used to fingerprint a user and build a history of their activity over time," he continues. "No one should be able to silently collect all of this information, whether it's a public Wi-Fi operator, another user on the network, or an internet service provider."
Pauly also describes how servers can see a user's IP address when they access a site, and says that "even worse," those servers can "fingerprint user identity" across different sites.
"These are big problems for user privacy, and in order to fix them, we need a new approach that has privacy built in by design," he says. "iCloud Private Relay adds multiple secure proxies to help route user traffic and keep it private."
"The proxies are run by separate entities," continues Pauly. "One is Apple, and one is a content provider."
Apple does not say which firm, or firms, are the other entity. Delziel Fernandes, also from Apple's Internet Technologies group, refers instead solely to what he calls ingress servers, run by Apple, and egress servers, run by other firms.
"When a device tries to access a server, it first sets up a network connection to the ingress proxy," says Fernandes. "This connection is set up using an IP address assigned by the network provider... [and the] egress proxy then forwards these requests to the destination servers by choosing an IP address that maps to the device's city or region."

Apple's illustrative diagram of how iCloud Private Relay works
What this means for the user is that Apple doesn't track which websites they're accessing. And neither the egress server company nor the destination website can track their identities in any way.
What web and network traffic will be protected by iCloud Private Relay
It does not cover all internet traffic, however. Apple says that iCloud Private Relay will apply to:- All Safari web browsing
- All DNS queries as users enter site names
- All insecure HTTP traffic
What web and network traffic will not be protected by iCloud Private Relay
Apple says that it will also apply to "a small subset of traffic from apps." However, it also listed multiple categories of internet traffic that will not be protected by iCloud Private Relay:- Local network connections
- Private domain name queries
- Traffic using a regular VPN
- Internet traffic using a proxy
There are features developers can access within iCloud Private Relay that mean they can ask for a user's specific location -- if the user allows, and if the app requires it. But otherwise location data is set by the egress server. That third-party and presumably trusted company adds an IP address "that maps to the device's city or region."
So a site or a service gets some location data and it's broadly right, it's correct enough to be useful for, say, a store showing its prices in the right currency or content-gating by geography.
The new iCloud Private Relay is to be introduced alongside macOS Monterey, iOS 15, and iPadOS 15 when they launch later in the year. It will require an iCloud+ subscription, and users will have to choose to turn on Private Relay -- though it is likely to default to on.
"Private Relay is built into iOS and macOS, so you don't need to do anything to adopt it from your app," Pauly told developers. "It's also important to understand that it won't always be affecting your app. It will only apply when a user is an iCloud+ subscriber and has Private Relay enabled."
Follow all the details of WWDC 2021 with the comprehensive AppleInsider coverage of the whole week-long event from June 7 through June 11, including details of all the new launches and updates.
Stay on top of all Apple news right from your HomePod. Say, "Hey, Siri, play AppleInsider," and you'll get latest AppleInsider Podcast. Or ask your HomePod mini for "AppleInsider Daily" instead and you'll hear a fast update direct from our news team. And, if you're interested in Apple-centric home automation, say "Hey, Siri, play HomeKit Insider," and you'll be listening to our newest specialized podcast in moments.

Comments
I think they've realized they have an open lane to the finish line here, a set of features they can release with zero competition. Because they have the only business model that allows this type of innovation.
But, still, I think Google and others will follow. Just more slowly and cautiously. And that's the reason I love it, it's going to make privacy more asked about, a more main stream and desirable feature. Companies will start competing on privacy, not wanting to be the most egregious offender. And I do think you'll see die hard Android geeks switching over, noticeable amounts.
In the past, it almost seemed like companies were competing to have the most violations of privacy. Facebook is obviously a troll in this area, but what really upset me was how they bought Oculus and then recently required a FB login to even use your Oculus headset. They did this around the time they started banning FB users for sharing any Hunter Biden stories. And at the same time, they started saying that you have to have a FB login in 'good standing' to use your Oculus headsets. What's the worst thing that could happen, if my social media site has complete control over whether I use my entire OS or not?
Yes Virginia, there IS a deliberate and coordinated war on the right to privacy.
One important note: While your internet and cell provider and any third parties will no longer be able to track you, Google themselves will continue to receive account data unless you turn off syncing for their services. Definitely extra steps to take if your privacy from everyone is important. AFAICT they offer the same level of privacy but don't make it clear and easy to do so.
Apple apparently turns syncing off automatically with theirs?
EDIT: Perhaps not entirely?
I've used Google's VPN on my smartphones and Pixelbooks for some time now, and one minor plus is quickly toggling the VPN off if it interferes with a particular service I want to connect to, and it does happen. I also use Google Fi on one smartphone which offers major privacy protection over a typical cell provider and defaults to Google's VPN.
There's very little to read about it on Wikipedia here: https://en.wikipedia.org/wiki/Google_One#Google_One_VPN
When you say "domestic terrorists", I presume you are alluding to Antifa and BLM who assault innocent people and violently invade police stations and burn down entire city blocks. Cause I can't think of any other active domestic terrorists. And for me those are foreign terrorists since I'm not American.
apple states proxies, either I’m being ssl bridged across both relay proxies or the proxies are serving their own certs to safari.
inspecting the cert served to safari would be a good clue.
The third-party companies are clearly operating as proxies which don't require authentication. The point of the service is Apple authenticates the user for billing purposes, then they hide the identity of the traffic's source. The third-party can see where you're going, but as long as you're using TLS to the destination, that's all they can see.
Yes, a warrant to both companies could correlate user identities with the sites they are visiting, assuming the information is logged, and assuming the logging has enough specificity. Since they're operated by separate companies, they are unlikely to have their clocks synchronized well enough for timestamp-based correlation.