If both your iPhone and passcode get stolen, you're in deep trouble
A new report highlights that when a thief has both an iPhone and the corresponding passcode, a user's entire digital life is at risk. While this is in no way new, there are some simple steps to mitigate the risk.

iPhone passcode
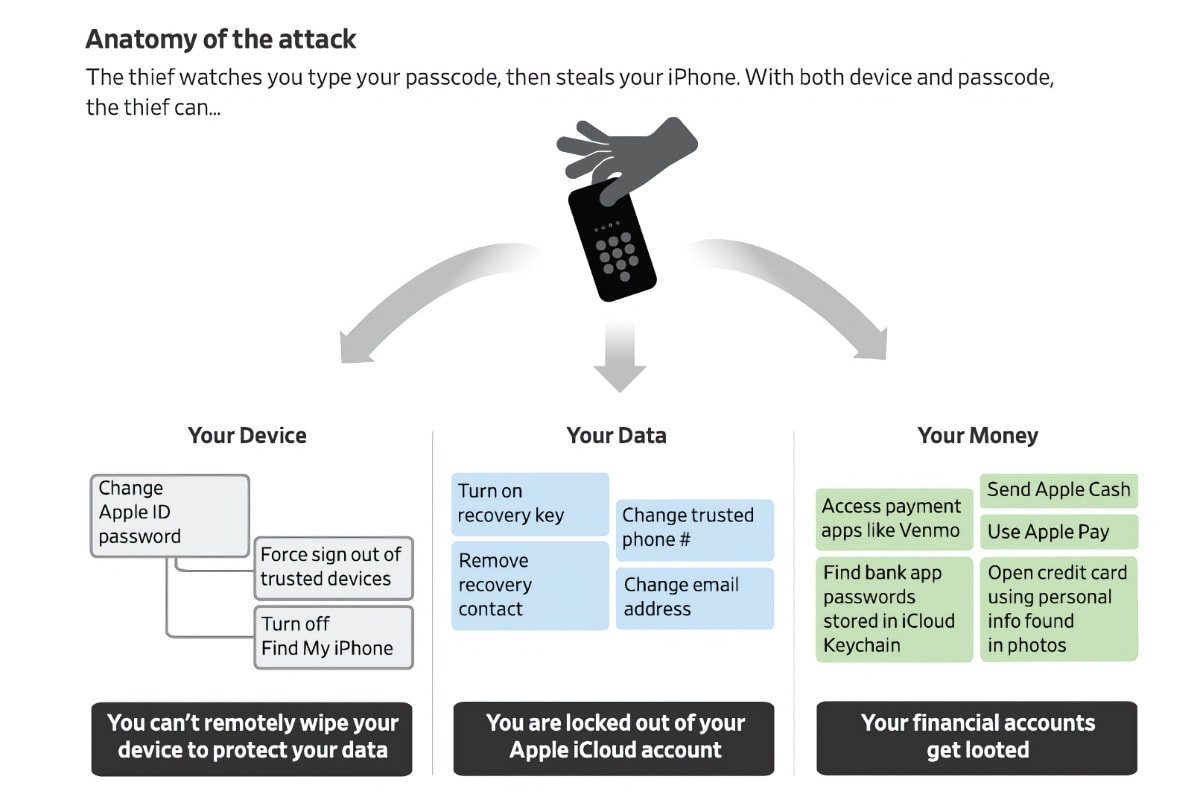
The "hack" involves the thief watching the victim type in their passcode, then steal the iPhone to access their data. In one case, a victim was locked out of her Apple account and lost about $10,000 from her bank account, according to The Wall Street Journal.
Because the login passcode offers access to most other apps -- and system settings -- a thief can use it to change the Apple ID password to lock victims out. "Once you get into the phone, it's like a treasure box," said Alex Argiro, who investigated a high-profile theft ring as a New York Police Department detective before retiring last fall.
The thief can also use the device passcode to access iCloud Keychain, which puts a person's entire online life at risk. Argiro said these opportunistic crimes have increased in the past two years in New York. "This is growing," he said. "It is such an opportunistic crime. Everyone has financial apps."
All victims The Wall Street Journal interviewed had their iPhones stolen while socializing in public in places like bars. In some cases, victims were physically assaulted and intimidated into handing over their phones and passcodes, and others believed they were drugged.
Sgt. Robert Illetschko, the lead investigator in one case, said groups of two or three thieves would go to a bar and befriend the victims to try and access their iPhones. If they couldn't watch the victim type in their passcode, the thieves might try to get them to open a social media app or have the victim hand over their phone for a picture.
Similar cases have been reported in Austin, Denver, Boston, and London.
In another case, a man had his identity stolen because he had saved photos of his passport, driver's license, paycheck direct-deposit form and health insurance paperwork in the Photos app. He was able to regain access to his Apple ID, but it's highly likely the thief kept the sensitive information.
Source: Elizaveta Galkina/The Wall Street Journal
Face ID or Touch ID can help prevent such attacks since people won't need to type in a passcode. But in New York, authorities have suggested Face ID as a possible entry point into iPhones.
Similar to a passcode, a thief could grab an iPhone after a victim logs in using biometrics, then prevent the iPhone from going into sleep mode. However, that access would be more limited since a passcode is needed to enter Face ID or Touch ID settings.
Apple users can turn on a feature called Attention Detection for Face ID in Settings > Face ID & Passcode. It requires a person to look at the iPhone before it authenticates the log in, meaning thieves who drug their victims can't log into the iPhone with this method.
As The Wall Street Journal noted, iOS doesn't require a person to enter an older password before setting a new one for Apple ID. Hardware security keys supported by iOS 16.3 didn't prevent account changes using only the passcode.
The passcode could even be used to remove security keys from the account.
An Apple spokeswoman did say that account recovery policies are in place to protect users from bad actors accessing their accounts.
"We sympathize with users who have had this experience and we take all attacks on our users very seriously, no matter how rare," she said, adding that Apple believes these crimes are uncommon because they require the theft of the device and the passcode. "We will continue to advance the protections to help keep user accounts secure."
Apple generally doesn't allow users to regain access to a stolen account, if a thief sets a recovery key on the Apple ID that the victim can't access.
In some of the cases, thieves were able to steal a victim's Social Security Number because of tax forms saved in iCloud Photos. Some Apple apps let users search for text, and searching for "SSN" or "TIN" (taxpayer identification number) in Apple Photos produced the document photo.
Although iCloud encryption can help prevent online hacking, it can't stop thieves from accessing sensitive information once they have iPhone access. So, storing such information in Apple Notes, Photos, or other apps is dangerous.
Next, Apple users should set their own Apple ID recovery key, which prevents anyone else from doing it.
Perhaps there is more the company could do to prevent such crimes. But, in the meantime, as it has always been, Apple users should be wary of typing their passcodes in public or handing their device to a stranger.
Read on AppleInsider

iPhone passcode
The "hack" involves the thief watching the victim type in their passcode, then steal the iPhone to access their data. In one case, a victim was locked out of her Apple account and lost about $10,000 from her bank account, according to The Wall Street Journal.
Because the login passcode offers access to most other apps -- and system settings -- a thief can use it to change the Apple ID password to lock victims out. "Once you get into the phone, it's like a treasure box," said Alex Argiro, who investigated a high-profile theft ring as a New York Police Department detective before retiring last fall.
The thief can also use the device passcode to access iCloud Keychain, which puts a person's entire online life at risk. Argiro said these opportunistic crimes have increased in the past two years in New York. "This is growing," he said. "It is such an opportunistic crime. Everyone has financial apps."
All victims The Wall Street Journal interviewed had their iPhones stolen while socializing in public in places like bars. In some cases, victims were physically assaulted and intimidated into handing over their phones and passcodes, and others believed they were drugged.
Sgt. Robert Illetschko, the lead investigator in one case, said groups of two or three thieves would go to a bar and befriend the victims to try and access their iPhones. If they couldn't watch the victim type in their passcode, the thieves might try to get them to open a social media app or have the victim hand over their phone for a picture.
Similar cases have been reported in Austin, Denver, Boston, and London.
In another case, a man had his identity stolen because he had saved photos of his passport, driver's license, paycheck direct-deposit form and health insurance paperwork in the Photos app. He was able to regain access to his Apple ID, but it's highly likely the thief kept the sensitive information.

Source: Elizaveta Galkina/The Wall Street Journal
Face ID or Touch ID can help prevent such attacks since people won't need to type in a passcode. But in New York, authorities have suggested Face ID as a possible entry point into iPhones.
Similar to a passcode, a thief could grab an iPhone after a victim logs in using biometrics, then prevent the iPhone from going into sleep mode. However, that access would be more limited since a passcode is needed to enter Face ID or Touch ID settings.
Apple users can turn on a feature called Attention Detection for Face ID in Settings > Face ID & Passcode. It requires a person to look at the iPhone before it authenticates the log in, meaning thieves who drug their victims can't log into the iPhone with this method.
As The Wall Street Journal noted, iOS doesn't require a person to enter an older password before setting a new one for Apple ID. Hardware security keys supported by iOS 16.3 didn't prevent account changes using only the passcode.
The passcode could even be used to remove security keys from the account.
An Apple spokeswoman did say that account recovery policies are in place to protect users from bad actors accessing their accounts.
"We sympathize with users who have had this experience and we take all attacks on our users very seriously, no matter how rare," she said, adding that Apple believes these crimes are uncommon because they require the theft of the device and the passcode. "We will continue to advance the protections to help keep user accounts secure."
Apple generally doesn't allow users to regain access to a stolen account, if a thief sets a recovery key on the Apple ID that the victim can't access.
How to protect yourself
It's not certain why the Wall Street Journal is treated this like a new emergency, or an emergent vector of attack. Passcode theft has always been at some level a concern for users, and it has always been good advice to secure that code.In some of the cases, thieves were able to steal a victim's Social Security Number because of tax forms saved in iCloud Photos. Some Apple apps let users search for text, and searching for "SSN" or "TIN" (taxpayer identification number) in Apple Photos produced the document photo.
Although iCloud encryption can help prevent online hacking, it can't stop thieves from accessing sensitive information once they have iPhone access. So, storing such information in Apple Notes, Photos, or other apps is dangerous.
Next, Apple users should set their own Apple ID recovery key, which prevents anyone else from doing it.
- On an iPhone or Mac, go to Settings > Your Name > Password & Security.
- Tap Recovery Key, then slide to enable it. On a Mac, click Manage next to Account Recovery.
- Tap Use Recovery Key and enter the device passcode.
- Write it down and store it in a safe place, then confirm it on the next screen.
Perhaps there is more the company could do to prevent such crimes. But, in the meantime, as it has always been, Apple users should be wary of typing their passcodes in public or handing their device to a stranger.
Read on AppleInsider


Comments
Personally, if I'm home I'm using my Mac. Despite the displays being much larger than the original iPhone it's still very small and limited in scope for my needs so it's a proper PC with a standard physical keyboard for me.
To help with security on the device I limit what can be seen on the device before my alphanumeric+special characters+long-press character passcode or face authentic the user. Even if something like GreyKey could test all 220-something characters to get in—which I highly doubt—the number of possibilities is too large to crack with current technique and computing power.
Even if it comes in gold, it's a mass-market product now, the most popular phone in the country. Can we leave the class warfare out of it?
if someone holds a gun to your head there’s not much you can do, but that’s an extreme situation. People living in areas where this is likely probably already pay attention to what’s on their iPhone.
if you say “Hey Siri? Whose phone is this” it’ll lock biometrics and require a PIN. Apple could change it so instead of needing a PIN it needs your Apple ID password. Then again, that person with a gun could then demand your Apple ID so it’s not much use.
I just don’t see why it’s the responsibility of Apple to deal with such an obscure problem. Better to teach people how to be responsible as any method Apple uses can still be overcome with violence.
It's not irrelevant because all the biometric options are security convenience with your passcode being both the fallback when your biometirc doesn't work x-number of times, you restart the device.
That means a 6-character passcode would be 107^6 for a total of 1.5 TRILLION possible combinations compared to a 6-digit PIN which is 10^6 for a total of 1 MILLION options. It really doesn't take much longer to input and because of Touch ID and Face ID not requiring you to unlock with your passcode constantly there's no reason not to have a more secure one.
If non-alphanumerics for passwords, like punctuation and other non-alphanumeric characters, are referred to as "special characters" I've deemed the much richer palette of characters available for the long-hold on the iOS virtual keyboard as "very special characters."
By my last count of the American English iOS keyboard there are 210 options. That means that a 4-character passcode would be 1.944 BILLION options. Moving to 6-characters it's now 85.8 TRILLION. Your 13 character passcode will have 1.54 nonillion possibilities (1,540,000,000,000,000,000,000,000,000,000) if you were to include just at least one "extra special character" into the mix.
Another scenario that comes up is taking devices in for repair. Generally main stores can be trusted but they often ask for unlock passwords to verify the repair went ok and you don't know what they are accessing on the phone.
https://discussions.apple.com/thread/6762585
It negates a lot of the benefit of biometrics when the passcode is the weak point, especially when they get tedious to enter and people end up choosing weak passcodes:
https://www.macobserver.com/news/top-20-iphone-passcodes/
Someone else lost a lot of money due to a stolen phone:
https://www.birminghammail.co.uk/news/midlands-news/man-loses-22500-life-savings-26085227
What would be nice to have is a second layer of security that people can put sensitive apps behind like photos, banking apps, browser sessions. This layer should require biometric id by the person who set it up and possibly an optional passcode in addition to that. This mode shouldn't allow new fingerprints/face added via passcode to unlock it.
This way, the main unlock is like a guest mode with restricted access. There really should be multiple modes on iOS. The lowest would be for device repairs or someone borrowing the phone to make a call like guest mode with access to settings and an empty browser. Next mode would be normal access mode. Restricted mode would secure sensitive apps/content behind a further series of unlocks.
Individual apps can be password protected but I think that is an Android thing in general.
Prior to any kind of service, the phone can be put into maintenance mode which requires a new password to lock things away without impacting the software tools which are required for testing etc.
The one caveat here is that your phone has to be minimally functional to put it into maintenance mode.
If absolutely necessary, and you have a Huawei store nearby, you can request to be present during the repair.
I thought Apple already had some of those options available to users.