A custom USB-C cable can jailbreak the T2 chip in a MacBook Pro
The security researchers that found a vulnerability in Apple's T2 chip have developed an exploit using a clone of an internal debugging cable that can hack a Mac without user action.

Credit: Apple
Earlier in October, the checkra1n team developed the unfixable vulnerability that essentially allows an attacker to jailbreak the T2 security chip in a Mac. Once they do, all types of malicious attacks can be carried out on an affected macOS device.
Now, the team has demoed a real-world attack that takes advantage of a technique similar to one leveraged by specialized USB-C cables used internally by Apple for debugging.
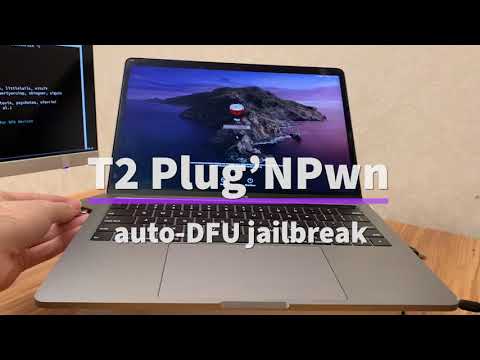
As depicted in a YouTube video, and accompanying blog post, the exploit causes a machine to shut down once the cable is plugged in. From there, it's placed into DFU mode and checkra1n is run to achieve a root SSH session. A second video posted to the team's YouTube account showed that the attack was successfully carried out by modifying the Apple logo at boot.
The attack is carried out by software reverse engineered from specialized debug probes, which are used by Apple and known under internal code names such as "Kong," "Kanzi," or "Chimp." These cables work by allowing access to special debug pins within a USB port for the CPU and other chips.
These "Chimp" or "Kanzi" cables have leaked from Cupertino and Apple retail in the past. Security researcher Ramtin Amin created an effective clone of the cable, dubbed a "Bonobo" and used in the video. Combined with the checkra1n team's exploits, it allows for this type of attack to be carried out.
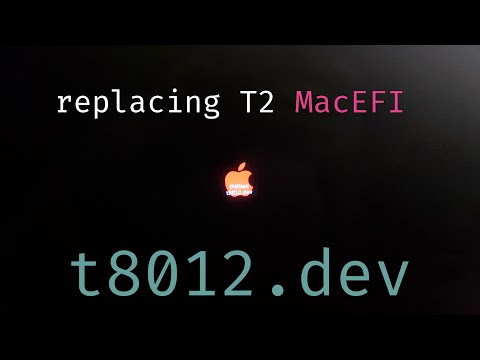
Although the video demonstration shows them modifying the Apple logo, the team notes that the same exploit can be used to replace a device's EFI and upload a keylogger. That's possible because a mobile Mac's keyboard is connected directly to the T2 chip.
The proof-of-concept exploit was disclosed by checkra1n security researchers Rick Mark, Mrarm, Aun-Ali Zaidi, and h0m3us3r. The team also announced that a version of the cable will soon be available for sale.
Of course, the attack requires direct physical access to a Mac, which rules out most types of scenarios for the average user.
However, users who may find themselves targeted by nation-states or cybercriminals should ensure that they have keep their Mac safe by maintaining physical security of the device.

Credit: Apple
Earlier in October, the checkra1n team developed the unfixable vulnerability that essentially allows an attacker to jailbreak the T2 security chip in a Mac. Once they do, all types of malicious attacks can be carried out on an affected macOS device.
Now, the team has demoed a real-world attack that takes advantage of a technique similar to one leveraged by specialized USB-C cables used internally by Apple for debugging.
As depicted in a YouTube video, and accompanying blog post, the exploit causes a machine to shut down once the cable is plugged in. From there, it's placed into DFU mode and checkra1n is run to achieve a root SSH session. A second video posted to the team's YouTube account showed that the attack was successfully carried out by modifying the Apple logo at boot.
The attack is carried out by software reverse engineered from specialized debug probes, which are used by Apple and known under internal code names such as "Kong," "Kanzi," or "Chimp." These cables work by allowing access to special debug pins within a USB port for the CPU and other chips.
These "Chimp" or "Kanzi" cables have leaked from Cupertino and Apple retail in the past. Security researcher Ramtin Amin created an effective clone of the cable, dubbed a "Bonobo" and used in the video. Combined with the checkra1n team's exploits, it allows for this type of attack to be carried out.
Although the video demonstration shows them modifying the Apple logo, the team notes that the same exploit can be used to replace a device's EFI and upload a keylogger. That's possible because a mobile Mac's keyboard is connected directly to the T2 chip.
The proof-of-concept exploit was disclosed by checkra1n security researchers Rick Mark, Mrarm, Aun-Ali Zaidi, and h0m3us3r. The team also announced that a version of the cable will soon be available for sale.
Who's at risk, and how to protect yourself
As noted earlier, these specialized debug cables can sometimes be found in the wild. With a commercial clone soon to be available, there's a good chance that most Mac models on the market with a T2 chip could be vulnerable.Of course, the attack requires direct physical access to a Mac, which rules out most types of scenarios for the average user.
However, users who may find themselves targeted by nation-states or cybercriminals should ensure that they have keep their Mac safe by maintaining physical security of the device.

Comments
https://blog.t8012.dev/plug-n-pwn/
Even though it requires physical access, it shouldn’t be possible to crack a computer’s chip focused on security so easily.
Or are you saying user authentication is required as well?
The continual axe grinding is predicable and rather boring. No one cares if you don’t like Apple stuff.