Apple being sued because two-factor authentication on an iPhone or Mac takes too much time...
A class action suit has been filed that accuses Apple's two-factor authentication of being too disruptive to users, taking too much time out of a user's day when it is needed, and abusive since it can't be rolled back to a less safe login method after 14 days.
Two-factor authentication on an iPad and iPhone
The suit, filed by Jay Brodsky in California alleges that Apple doesn't get user consent to enable two-factor authentication. Furthermore, once enabled, two-factor authentication "imposes an extraneous logging in procedure that requires a user to both remember password; and have access to a trusted device or trusted phone number" when a device is enabled.
Filing paperwork associated with the suit also alleges that harm is being done, and potential class members "have been and continue to suffer harm" including economic losses, based on a waste of personal time for an extended login process that has become a multiple-step process.
The filer alleges that a software update enabled two factor authentication on or around September 2015. However, neither macOS El Capitan nor iOS 9 released in the timeframe put forth by the filer mandated two-factor authentication, nor implemented it without an explicit and multiple-step opt-in procedure requiring the user to consent. It is required to take advantage of some of Apple's services, like Home Sharing and HomeKit Hubs, however.
Brodsky alleges that the email that Apple sends after two-factor authentication is enabled is insufficient to warn the user that the setting is irrevocable. The filing calls a link in an email to a page to reset the configuration "unobtrusive" but does not specify what would have been sufficiently noticeable in a three-paragraph email.
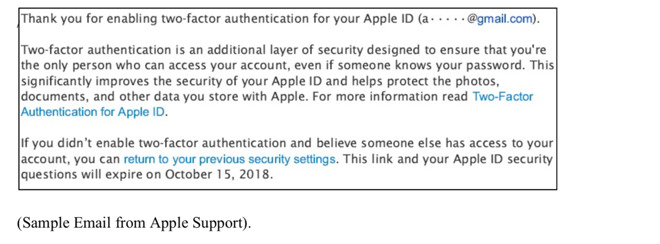
Email sent to user after two-factor authentication is activated on an iCloud account
According to the suit, when two-factor authentication is demanded, the process as follows takes between two and five minutes.
The filer believes that Apple has interfered with the use of the device with the "extraneous login process through two-factor authentication" that has been "imposed" on the class. The time it takes to execute the extra login data is said to be "continuous, systematic and ongoing" and Apple has "caused injury to Plaintiff and Class Members' rights to choose the level of security for Plaintiff and Class Member owned devices."
The suit is demanding injunctive relief, fines and penalties assessed on Apple in accordance with the Computer Fraud and Abuse Act, and is seeking "all funds, revenues, and benefits" that Apple has "unjustly received" from the action, but what precisely that entails isn't listed in the filing documents. The filer is also asserting that Apple is violating California's Invasion of Privacy act, but how that applies also isn't immediately clear.

Two-factor authentication on an iPad and iPhone
The suit, filed by Jay Brodsky in California alleges that Apple doesn't get user consent to enable two-factor authentication. Furthermore, once enabled, two-factor authentication "imposes an extraneous logging in procedure that requires a user to both remember password; and have access to a trusted device or trusted phone number" when a device is enabled.
Filing paperwork associated with the suit also alleges that harm is being done, and potential class members "have been and continue to suffer harm" including economic losses, based on a waste of personal time for an extended login process that has become a multiple-step process.
The filer alleges that a software update enabled two factor authentication on or around September 2015. However, neither macOS El Capitan nor iOS 9 released in the timeframe put forth by the filer mandated two-factor authentication, nor implemented it without an explicit and multiple-step opt-in procedure requiring the user to consent. It is required to take advantage of some of Apple's services, like Home Sharing and HomeKit Hubs, however.
Brodsky alleges that the email that Apple sends after two-factor authentication is enabled is insufficient to warn the user that the setting is irrevocable. The filing calls a link in an email to a page to reset the configuration "unobtrusive" but does not specify what would have been sufficiently noticeable in a three-paragraph email.

Email sent to user after two-factor authentication is activated on an iCloud account
According to the suit, when two-factor authentication is demanded, the process as follows takes between two and five minutes.
AppleInsider hasn't been randomly presented with any two-factor authentications on Saturday even following OS updates to an iPhone XS Max, an iPhone X, and two sixth-generation iPads, but was able to force the issue on a new device. The process took 22 seconds in total to accomplish.First, Plaintiff has to enter his selected password on the device he is interested in logging in. Second, Plaintiff has to enter password on another trusted device to login. Third, optionally, Plaintiff has to select a Trust or Don't Trust pop-up message response. Fourth, Plaintiff then has to wait to receive a six-digit verification code on that second device that is sent by an Apple Server on the internet. Finally, Plaintiff has to input the received six-digit verification code on the first device he is trying to log into. Each login process takes an additional estimated 2-5 or more minutes with 2FA."
The filer believes that Apple has interfered with the use of the device with the "extraneous login process through two-factor authentication" that has been "imposed" on the class. The time it takes to execute the extra login data is said to be "continuous, systematic and ongoing" and Apple has "caused injury to Plaintiff and Class Members' rights to choose the level of security for Plaintiff and Class Member owned devices."
The suit is demanding injunctive relief, fines and penalties assessed on Apple in accordance with the Computer Fraud and Abuse Act, and is seeking "all funds, revenues, and benefits" that Apple has "unjustly received" from the action, but what precisely that entails isn't listed in the filing documents. The filer is also asserting that Apple is violating California's Invasion of Privacy act, but how that applies also isn't immediately clear.
Brodsky versus Apple, alleg... by on Scribd


Comments
Apple should work on another way to strengthen security. What happened to simple and intuitive philosophy of Apple’s?
For one, they could get rid of the ridiculous in-security questions, which defeat the purpose of any real security they implement. It's hard to take anyone who uses those seriously.
I suppose a properly implemented 2FA is better than not, in terms of security. But, like many things, it's a tradeoff.
1. I sent my iPhone 6s in for a battery replacement.
2. One day, I woke up and thought “I’m going to wipe my IPad clean”
- Background: I actually do this several times a year, usually after a significant OS upgrade. It also cleans of any games, junk, etc. that I don’t really need. I do this with the knowledge that I don’t use backup, but my contacts, calendar, shortcuts, passwords will sync back.
I think you can see my problem. My 6s has been gone 10 days at this point, and it took a full 2 weeks to get my phone back (bad Apple).
Anyways, my wiped iPad boots up but I run into 2FA to set up the iPad. I know everything I need to know (password to AppleID) but what I don’t have is my 6s. (Apple sends the code to the 6s and there’s no alternative).
I also don’t know my email password because it’s saved in Keychain.
At this point, I also don’t know what happened to my phone. It should be fixed (it was just a freakin battery) and as of the previous day I’d already reached the highest level of support. (There was no update on Apple’s site that they even received it). The nice support lady, wanted to call me with an update... no phone. So, we agreed on email... now no email.
Fortunately, I remembered that I removed the SIM card. So, I went to my T-mobile store and used a display phone to authenticate. Got my IPad up and running and found my iPhone was found/done and being shipped back.
Moral of the story is 2FA is great, but I really want it tied to something other than Idevice, like a YubiKey.
So, the lawsuit isn’t entirely frivolous. I also didn’t enable 2FA for my AppleID... I do want 2FA to log into my devices, but that’s not currently an option. I don’t care as much about my AppleID password it’s really really complex... as in come back in a few 100 million years (cracking it with today’s tech).
So while agreed that we need a better way, this method moves the bar above guessing passwords, and that is a good thing.
I often have to run stairs up and down to be able to do what I could do with a simple mouse click.
Its also very inconvenient when using another account.
I remember a very good Apple commercial which was completely right about PC’s, but now sadly also a Mac reality:
https://youtu.be/8CwoluNRSSc
So two-factor authentication is bad because it requires two factors?
I think I'll sue AI because I have to enter a password to login to my password-protected account to comment on this site. I demand 100% secure zero-factor authentication!
Exactly! It might raise the security a bit, but it also raises the possibility of something going really wrong, a lot.
Also, another moral of the story is not to use Keychain to manage your passwords!!!
That said, it was a real problem for a friend in Europe who had his phone stolen, bought a new one, but wasn’t able to activate it without 2FA. He had traveled with his Apple Watch but Apple didn’t allow 2FA to go to it, because it needed the phone to set it up. So he was unable to download his contacts and info. At some point, people need to be able to deal with these kinds of issues without traveling with an electronic arsenal. That’s where a simple dongle would be helpful.